
Hardware and Network Servicing
Level-II
Based on June 2021, Curriculum Version 1
Module Title: - Administrating Network and Hardware
Peripherals
Module code: EIS HNS2 M04 0322
Nominal duration: 40Hour
Prepared by: Ministry of Labour and Skill
August , 2022
Addis Ababa, Ethiopia
Table of content
Acknowledgement..........................................................................................................5

Version -1
Page 2 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Introduction to the Module ............................................................................................7
Unit one: Confirm requirements of client..................................................................9
1.1. Confirm requirements of client....................................................................10
1.2. Client requirements.....................................................................................10
1.3. Client requirements and peripherals...........................................................10
Self check test-1. .............................................................................................13
0peration sheet-1.............................................................................................14
Lap test 1.........................................................................................................15
Unit Two: Obtain required peripheral ........................................................................16
2.1. Obtaining peripheral .....................................................................................17
2.2. Verifying client requirement .........................................................................17
2.3. Equipment inventory verification.................................................................19
Self check test:-2 .............................................................................................23
Operation sheet 2 ............................................................................................24
Lap test 2.........................................................................................................26
Unit Three: Connect hardware peripherals...............................................................27
3.1. Schedule hardware installation time ...........................................................28
3.2. Remove old peripherals................................................................................28
3.3. Connect the new peripherals .......................................................................29
3.4. Test peripherals.............................................................................................30
Self check test 3. .............................................................................................31
Unit Four:-Install and Configure peripherals to a network .......................................32
4.1. Connect peripherals to the network ............................................................33
4.2. Configure security.........................................................................................65
4.3. Configure workstation ..................................................................................65
Self check-4.....................................................................................................68
Operation sheet 3 ............................................................................................70
Lap test 4.........................................................................................................71
Unit Five:- Administer and support peripheral services...........................................72
5.1. Indentify priority ............................................................................................73
5.2. Configure network maintenance schedule settings ..................................73

Version -1
Page 3 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
5.3. Demonstrate peripheral supporting methods ............................................76
Self check test 5. .............................................................................................77
Operation sheet 4 ............................................................................................79
Lap test 4.........................................................................................................80
Unit Six:- Use command line tools..............................................................................81
6.1. Indentify command-line environment.........................................................82
6.2. The Difference between Command-line and graphical user interface. ....84
6.3. Apply Command-line tools ...........................................................................86
Self check 6. ....................................................................................................92
Unit Seven: Maintain peripherals and fix common problems ................................93
7.1. Identify regular maintenance schedule .......................................................94
7.2. Replace consumables...................................................................................94
7.3. Identify peripheral failures............................................................................96
Self check test-7 .............................................................................................99
Unit Eight:-Use and maximize operating system ....................................................100
8.1. Identify Configured Operating system ......................................................101
8.2. Explain Install and upgrade application software ....................................102
8.3. Identify Use graphical user interface and command-line interface........104
8.4. Use third-party operating system utilities.................................................105
Self check test-8 ...........................................................................................106
Operation Sheet 5. ........................................................................................108
Operation sheet-6..........................................................................................112
Lap test 5.......................................................................................................115
Unit Nine:- Support input and output devices .........................................................116
9.1. Identify input/output devices functionality ...............................................117
9.2. Explain appropriate driver installation ......................................................118
Self check Test 9. ..........................................................................................119
Reference ............................................................................................................120

Version -1
Page 4 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
We would like to thank First of all God for giving me strength and health to start and
finishing TTLM. And next we thanks Ministry of Labor and Skills that MoLS gives available
environment like dormitory, hotel, water, coffee ceremony and other facilities for the all TVE
trainers to work this Teaching, Training and Learning Materials (TTLM).
Acknowledgement

Version -1
Page 5 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Acronym
List of abbreviation
I/O Input or Output
VDU visual display unit
OS Operating system
HP-UX, AIX Hewlett Packard Unix, Advanced Interactive Executive
Mac OS Macintosh operating system
LAN Local area network

Version -1
Page 6 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
WAN Wide area network
VPN Virtual private network
PSTN public switched telephone network
Ipconfig Internet Protocol Configuration
P2P peer-to-peer
UTP Unshielded twisted-pair
STP Shielded twisted-pair
UTP Unshielded twisted-pair
STP Shielded twisted-pair
ASICs application-specific integrated circuits
ASICs application-specific integrated circuits
VLAN Virtual Local Area Network
CLI command-line interface
GUI Graphical User Interface
HDD or SSD Hard Disk Drive or Solid State Drive
CHKDSK and SFC Check Disk and System File Checker
PDA Personal digital assistant
This module provide you to acquire knowledge of Network devices and hardware peripherals
that allow user interface and networking systems, how to connect network devices and
computer hardware peripherals in general.
This module covers the units:
Confirm requirements of client
Obtain required peripherals
Connect hardware peripherals
Install peripherals to a network
Use and maximize operating system
Administer and support peripheral services
Maintain peripherals and fix common problems
Support input and output devices
Introduction to the Module

Version -1
Page 7 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Configure peripheral services
Learning Objective of the Module
Know the client requirements
Know about network client and its purpose
Understand remote system administration and available tools.
Understand Operating system initialization
To use the OS and to maximize skills
To know the way of maintenance
To support I/O devices
Know how configuration of peripherals
Module Instruction
For effective use this modules trainees are expected to follow the following module
instruction:
Read the specific objectives of this Learning Guide.
Read the information that this module contain.
Complete the Self-check.
Submit your accomplished Self-check.
Do the Operations which in the module.
Do the LAP test in page (if you are ready) and show your output to your teacher.
*Your teacher will assess your result either satisfactory or unsatisfactory. If unsatisfactory,
your teacher shall advice you on additional work. But if satisfactory you can proceed to the
next topic.

Version -1
Page 8 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Unit one: Confirm requirements of client
This unit is developed to provide you the necessary information regarding the following content
coverage and topics:
Client peripheral requirements
Client requirements and peripherals
Client requirements
Client support expectations
This unit will also support you to accomplish the learning outcomes stated in the cover page.
Specifically, upon completion of this learning guide, you will be able to:
Classify and verify client peripherals requirements.
Identify Client requirements and peripherals
explain Client requirements
Identify Client support expectations

Version -1
Page 9 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
1.1. Confirm requirements of client
Peripheral are the devices that are attached to the computer’s system unit rear or front side.
Computer peripherals grouped into
A. I/O (Input or output),
B. Communications devices and
C. Secondary storage devices.
1.2. Client requirements
Clients and customers may include but not limited to:
Internal departments
External organizations
Individual people
Employee
1.3. Client requirements and peripherals
Network equipment should be included but not limited to:-
LAN
WAN
VPN
The internet
The use of the PSTN for dial-up modems only
Private lines
Data and voice.
Workstations
Personal computers
Modems or other connectivity devices
Printers
Hard drives
Monitors
Switches
Hubs
Personal digital assistant (PDA)
Other peripheral devices
Software may included:-
May include but is not limited to commercial,
Domestic
Packaged or adapted software.

Version -1
Page 10 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Consumables may include:-
Consumables are goods used by individuals and businesses that must be replaced regularly
because they wear out or are used up. They can also be defined as the components of an end
product that is used up or permanently altered in the process of manufacturing such as
semiconductor wafers and basic chemicals.
ink cartridges
toner cartridges
Ribbons
floppy disks
CD-RW
Operational Health and Safety (OHS) standards may include:
Correct posture
Lighting
Type of desk
Type of monitor
Style of chair
Typing position
Repetitive strain injury prevention
Ventilation
Light position
Correct lifting method
Length of time in front of computer
Network operating system
May include but is not limited to Novell NetWare 5 or above or any operating system that has
multi-user ability, Linux, Mac OS, Windows 7 or above.
Tools and Equipment
Hardware peripherals and workstation
Live network
Cables
Network operating system
Soft wares
Toolkit
Cable tester
Printer (laser printers and ink jet printers[mono or colored])
Command line tools may include:
Ping Localhost (127.0.0.1)
Ipconfig
Ipconfig/all

Version -1
Page 11 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Ping
Self check test-1.
Name: _____________________________ IDNo_________ Date: ___________________
Time started: ____________ Time finished:
________________
Instruction:-Read all questions which given below and you to answer the correct one.(2
points each)
1. Follow Operational Health Safety (OH&S) guideline is not important at workplace.

Version -1
Page 12 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
A. True B. False
2. Warranty is not important to know what kind of support services are offered by the
prospective supplier.
A. True B. False
3. From the following one is used to control the movement of cursor.
A. keyboard B. Mouse C. Printer D. None
3. All peripheral devices are Input devices.
A. True B. False
4. Which one of the following Input devices that help to write or enter the letters and
numbers in to your computer?
A. Keyboard B. Printer C. Monitor Mouse
5. From the given alternatives One is output device
A. Monitor B. Printer C. Projector D. All are answers
Instruction: Match column A with column B.
Column A Column B
6. Operational Health and Safety A. Modem
7. Clients B. input or output devices
8. Connectivity devices C. Internal departments
9. Peripherals D. Correct posture
Instruction: Say true or false
10. Output peripherals are show the product or display result of input.
11. Keyboard and mouse are not input peripherals
12. Communication devices are produce sounds capture pictures.
0peration sheet-1
Start up your computer
Step 1:- Connect the power cables on the system unit and monitor.
Step 2:-Connect hardware peripherals to the computer on the back side front side.
Step 3:- Boot you Computer.

Version -1
Page 13 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Lap test 1
Instruction: Answer all the questions listed below, if you have some clarifications – feel free
to ask your teacher.
Identify the following
1. Operating System
_____________________________________________________________________
___
_____________________________________________________________________
_____________________________________________________________________
_____________________________________________________________________
_____________________________________________________________________
____________
2. Client

Version -1
Page 14 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
_____________________________________________________________________
_____________________________________________________________________
_____________________________________________________________________
_____________________________________________________________________
_____________________________________________________________________
_______________
3. Equipment
_____________________________________________________________________
_____________________________________________________________________
_____________________________________________________________________
_____________________________________________________________________
_____________________________________________________________________
_____________________________________________________________________
__________________
4. OHS
_____________________________________________________________________
_____________________________________________________________________
_____________________________________________________________________
_____________________________________________________________________
_____________________________________________________________________
_______________
Your teacher will evaluate your output either satisfactory or unsatisfactory. If
unsatisfactory, your teacher shall advice you on additional work. But if satisfactory,
you can proceed to the next topic.
Unit Two: Obtain required peripheral
This Unit is developed to provide you the necessary information regarding the following
content coverage and topics
Obtaining peripheral
Verifying client requirement
Equipment inventory Verification
This guide will also assist you to attain the learning outcome stated in the cover page.

Version -1
Page 15 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
The first step in obtaining a peripheral device is to put suppliers of that device. Then, there
are factors you need to consider about the supplier and the devices on offer, such as support
provided and purchase price. This will help you to compare and choose the most appropriate
supplier and the exact model of the device according to client requirements. Finally, you are
ready to place an order for your organization or client to purchase the device.
Locating the supplier
There are many ways to find a supplier of peripheral equipment. Some ways include:
i. Searching the Internet
Specifically, upon completion of this Learning Guide, you will be able to
Verify obtaining peripherals
Explain equipment inventory
Identify and Verify client requirements
2.1. Obtaining peripheral
2.2. Verifying client requirement

Version -1
Page 16 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
The Internet provides different methods for searching for suppliers. Using search engines
such as Google or Yahoo can help you find a hardware supplier anywhere in the world.
Suppliers will often have their own websites that can provide you with catalogues of
available equipment. Other ways to investigate suppliers are to follow links from a website
such as a manufacturer’s website, or to browse website directories that may be linked to
search engine home pages.
ii. Telephone directory
A telephone directory is useful if you need to find a hardware supplier located within your
local area.
iii. PC magazines
Computing magazines often contain a large section devoted to advertising current hardware
suppliers.
iv. Brochures/advertising material
Many larger hardware suppliers use television, radio or leaflet deliveries to inform potential
customers of their latest hardware.
v. Newspapers
Major newspapers have computer/IT sections or classified advertisements which can be a
source for finding suppliers.
Contacting the manufacturer directly
Manufacturers generally have their own websites. These may list major suppliers in your
area. Emailing or telephoning the manufacturer may also be a way to find out names of local
suppliers.
vi. Choosing supplier
With so many choices of suppliers available, how do you find the right one? There are a few
factors to consider:
vii. Selecting a peripheral
Once you have selected suitable suppliers you need to contact each supplier. Information you
should find out from the supplier includes:
Model and manufacturer names of peripherals that will satisfy the majority of your clients
requirements (including system specifications, physical dimensions, support)
You may find it helpful to keep a record of any details that you collect so you refer to this
information quickly and easily.
viii. Placing the order
Version -1
Page 17 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Before an order is submitted, it could also be necessary to obtain final approval from senior
staff. Often an order form might require signatures from the manager or supervisor before it
can be processed. A purchasing department might require written quotes from three suppliers,
a recommendation and justification for the chosen supplier. Make sure that you find out from
your supervisor or manager what procedures you need to follow when placing an order within
your organization.
ix. Sample order form
From ________________________
Date ________________________
Code
Quantity
Description
Price
Supplier: name and telephone
Total price
Delivery point ________________________________
Budget holder’s signature ________________________________
Please come back to the Purchasing Department_________________________
Hardware inventory provides a simple way of finding basic information about your installed
hardware. Hardware includes processors, memory, serial ports, parallel ports, power supplies,
fans, graphics adapters, network adapters.
Hardware inventory organization means keeping a count of every piece of IT hardware
within an inventory database and asset repository. Having solid hardware inventory
organization helps you keep track of your assets, upgrade your inventory when needed, and
avoid theft or losses.
Computer inventory management is a set of best practices used to keep track of computers
within a systems environment, and it can include information about the following: Files,
directories, and storage devices. Hardware inventory provides you with important
information, such as the configuration and location of computers, which computers require an
operating system upgrade, and which computers have the hardware that is required for a
software upgrade.
2.3. Equipment inventory verification

Version -1
Page 18 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Details that should be included within a hardware inventory include:
Description of hardware device
Serial number
Manufacturer
Warranty or maintenance conditions
Supplier
Components
Model number
Location
Number and identity of authorized users
Purchase price
Date of purchase
Storing peripherals
Peripheral devices need to be located in a suitable environment — otherwise there may be
potential problems. It is a good idea to refer to the manufacturer’s manual to determine what
guidelines should be followed.
When storing peripherals it is important to:
Make sure equipment is kept in ideal working conditions
Adhere to current Occupational Health and Safety guidelines
Ensure the electrical safety of the device
Consider security of the device.
Keeping equipment in ideal working conditions
Each manufacturer will have their own recommendations on how to store their peripheral
equipment. In order to guarantee that a peripheral will function correctly throughout its life it
is important to follow guidelines that have been recommended by the manufacturer. Some
common recommendations may include:
Keep equipment in the correct position — After unpacking, most devices will usually have a
proper resting position. If a device is not kept in its natural position, there could be problems
when trying to operate the device later on. For example, when a printer is stored in a vertical
position, components such as the ink cartridges could leak or be dislodged.
Keep equipment away from weather, dust and other harmful material — When finding a
storage location, consider what kind of elements the device may be subjected to. If, for
example, you store a USB drive in a cabinet next to chalk, dust from the chalk could
potentially damage the storage device’s USB connection.
Do not expose equipment to extreme temperatures and high humidity — Sudden changes in
temperature can cause condensation in many peripheral devices. For instance, if a video
camera is taken from a cold place to a warm place, condensation may form on the lens and
internal parts.

Version -1
Page 19 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Avoid storing the device in direct sunlight — Exposure to direct sunlight could damage many
of the external components of a device as well as subject the device to high temperatures.
Do not expose equipment to water or moisture — If water gets inside many peripheral
devices there is a risk of electric shock.
When positioning peripherals in their permanent locations it is important to take into account
many OH&S considerations as follows.
A. Positioning of the monitor
It is essential to position a monitor correctly to ensure it will suit the needs of the user. Tips
include:
Try to make sure that monitor is in a position away from the glare of sunlight.
Check that the brightness and contrast controls of the screen have been adjusted to suit
lighting conditions in the room.
The top of the screen should be the same level as the user’s eye level.
A. Positioning of other equipment
Some general Occupational Health and safety guidelines to consider when positioning other
peripheral equipment are:
Make sure that you can reach the peripheral device and its components without having to
strain your back.
Place equipment such as scanners and printers at a suitable height so a user is easily able to
reach paper trays, open scanner lids, etc.
Make sure that equipment such as speakers is easily accessible if settings such as volume
control need to be changed.
B. Ensuring electrical safety
Some tips to ensure electrical safety are:
Do not be tempted to add too many extension cables or double socket adapters to your
existing electrical sockets.
C. Never use damaged plugs or leads.
If possible, ask an electrician to check the safety of your system.
Position electrical leads where they will not cause tripping hazards to people.
D. Physical security of devices
In many situations it is important to consider the physical security of the peripheral devices.
Some devices, such as digital cameras, data projectors and USB drives, may not be

Version -1
Page 20 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
permanently connected to a computer so it will be necessary to find a secure location to store
the device. Make sure that these kinds of devices are secured in a lockable storage cupboard,
cabinet or safe when not required. Some organizations install security devices onto desks to
guarantee that computers are secure and will not be able to be taken from their position unless
unlocked.
Storing consumables
The term “consumables” are a product that is used once and then replaced by others
Example they include:-
Paper, CD or DVD and printer cartridge. These needs to placed at safe and dry environment
i. Paper
Paper needs to be stored in an area which is cool and dry, to prevent moisture from fusing
pages together.
ii. Ink cartridges and toner
Make sure to store cartridges/toner in a cool dry place, away from sparks and open flames,
with adequate ventilation and do not expose the device to high temperatures.
Also ensure that the cartridges are not taken out of their packaging until they will be used
within the printer, as the ink will dry out before use.
When possible, make sure that CDs are kept in their protective case, to minimize the chances
of being scratched. Also keep them out of direct sunlight and extreme temperatures.

Version -1
Page 21 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Self check test:-2
Name: _____________________________ IDNo_________ Date: ___________________
Time started: ____________ Time finished:
________________
Instruction: Read the following questions bellow by writing True or False
2. Locating or placing hardware peripheral at suitable environment is not important.
3. Digital cameras, data projectors and USB drives are not security devices.
4. Check that the brightness and contrast controls of the screen have been adjusted to suit
lighting conditions in the room.
5. When you use damaged plugs, your computer may be damaged immediately.
6. All consumables are used once and replaced by other.
Instruction: Choice
7. If you placing any kind of consumables direct to sunlight or on the wet place it
may________
A. Damaged B. it may reduce its quality C. A & B D. No
answer
8. ____________ is a way of recording and counting hardware or software in simple
manner.
A. Inventory B. Audit C. data capture D. All
9. From the following questions one is the way to find a supplier of peripheral equipment.
A. Searching of internet B. Newspaper C. Telephone directory D.
All
10. Which one of the following is not consumables.

Version -1
Page 22 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
A. Paper B. Ink cartridges and toner C. DVD and CD D. None
Instruction: Match column A with Column B
Column A Column B
1. Physical security of devices A. keeping a count of every piece of IT
2. Hardware inventory B. Never use damaged plugs or leads
3. Ensuring electrical safety C. Cupboard, cabinet box
4. Proper resting position D. Locating a supplier
5. Brochures/advertising materials E. Keep equipment in the correct position
Operation sheet 2
Documenting peripherals used with each computer
If the peripheral is an essential part of the computer system (for example mouse, keyboard or
monitor) it is logical to record information about the device within the documentation for the
computer to which it is connected. Individual computer inventories will often contain detailed
information about the computer’s related hardware and software. It may also be more
practical to record information about the peripheral inside the computer’s record, if the device
is also permanently connected to a computer (for example a printer or scanner).
Example of Hardware inventory
Manufacturer:
Dell
Model:
OptiPlex GX280MT
Minitower—Power
Monitor:
Dell UltraSharp
1905FP flat panel,
Operating System:
Windows XP
Printer:
HP LaserJet IID
Serial number:
12345
Keyboard:
Dell USB keyboard
RAM:
128 Mb
Pointing device:
Dell USB 2-button
optical mouse with
scroll
Hard disk space:
160 Gb
If the device is shared between several computers, it makes more sense to keep information
about the peripheral as an individual entry in an inventory. Devices such as digital cameras,
data projectors and USB drives would more likely to be used by many computers, thus it
would make more sense to record their details separate to the computer details.

Version -1
Page 23 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Below is a sample checklist for a typical inkjet printer.
printer
cartridge
power cable
USB cable
sample paper
feeding device
CD driver
Be attentive when unpacking a peripheral device — handle the packaging and contents with
care, as you do not want to damage your new device. Remove any packing material
surrounding and also within the device. Some printers, for example, have soft foam and
plastic pieces inside the device to ensure that parts are locked into the correct position. Make
sure that you remove these pieces and foam before installation.
Version -1
Page 24 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Lap test 2
Name: _____________________________ IDNo _____________Level ____________
Time started: ________________________ Time finished: ________________
Instructions: You are required to perform the following individually with the presence of
your teacher.
1. Start up your computer
2. Open Ms Excel
Write the form given bellow placing an order of peripherals in your word.
From ________________________
Date ________________________
Code
Quantity
Description
Price
Supplier: name and telephone
Total price
Delivery point ________________________________
Budget holder’s signature ________________________________
Please come back to the Purchasing Department_________________________
Unit Three: Connect hardware peripherals
Version -1
Page 25 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Installation (or setup) of a computer program (including device drivers and plug-in), is the act
of making the program ready for execution. Installation refers to the particular configuration
of a software or hardware with a view to making it usable with the computer.
This unit is developed to provide you the necessary information regarding the following content
coverage and topics
Schedule hardware installation time
Remove old peripherals
Connect the new peripherals
Test peripherals
This guide will also assist you to attain the learning outcome stated in the cover page.
Specifically, upon completion of this Learning Guide, you will be able to:
Schedule installation time
Explain removing old peripherals
Explain connecting the new peripherals
Identify configuration of a computer with the new peripherals
Test peripherals
3.1. Schedule hardware installation time

Version -1
Page 26 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Thorough planning ensures that you have everything to meet all the prerequisites for the successful
setup and installation of the system. Planning minimizes errors during installation and enables a
quicker upgrade or installation.
Guidelines for hardware/software installation plan. Burn-in means to configure the hardware and run it for
some period of time, usually 24-72 hours.
Open the My Computer window, right-click on the peripheral device (usually labeled Removable
Disk) and select Eject from the contextual menu. open the My Computer window, select the
peripheral device (usually labeled Removable Disk) and then select Eject this Disk from the Common
Tasks pane of the window.
To remove a piece of hardware or peripheral from your computer, use these steps:
1. Open Settings.
2. Click on Devices.
3. Click on Bluetooth & other devices.
4. Select the device that you no longer need.
5. Click the Remove device button.
6. Click View tab and select Show hidden devices.
7. Expand the branches in the device tree & look for the faded icons.
8. These indicate unused device drivers.
9. Right-click on it and select Uninstall.
How do I get my external keyboard off?
Just plug it into your laptop, either into the keyboard port or a USB port, whichever is
available. You can start using the keyboard the second it's plugged in. Note that adding an
external keyboard often doesn't disable the laptop's internal keyboard. You can use both!
Should you delete old drivers?
It is generally not recommended to uninstall GPU drivers solely through the operating
system, as the process may leave some residual files and folders that can still cause conflicts.
Clean Unplugged Data once a device plugged into your computer, there will be some space
available for it to release or save files. After unplugging, some data of the device may leave
on your computer to occupy some space, Driver Booster can clean these unplugged data
conveniently and thoroughly to spare more space.
3.2. Remove old peripherals

Version -1
Page 27 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Perform the following steps in the Device Manager window that appears:
1. Select View > Show Hidden Devices.
2. Expand the Network Adapters list.
3. Uninstall ALL of the grayed out network adapters (there will likely be several; do NOT
delete drivers).
4. Uninstall any unknown devices.
5. Leave the other network devices alone.
How do I remove old Nic from registry?
Right-click the network adapter interface name (the long alphanumeric string) in the
Windows Registry and select Delete.
Peripheral devices can be connected to your computer via USB port, serial port, parallel
port, specialized network card, or Ethernet network. Local area networks (LANs)
commonly use Ethernet networks for machine connection.
What is a new peripheral device?
Peripheral device, also known as peripheral, computer peripheral, input-output device, or
input/output device, any of various devices (including sensors) used to enter information and
instructions into a computer for storage or processing and to deliver the processed data to a
human operator.
The most common peripherals are a printer, scanner, keyboard, mouse, tape device,
microphone, and external modem that are externally connected to the computer.
A test procedure is a formal specification of test cases to be applied to one or more target
program modules. Test procedures are executable. A process called the VERIFIER applies a
test procedure to its target modules and produces an exception report indicating which test
cases, if any, failed. Simply right-click on the Windows button in the bottom-left corner of
your screen, and then click System. In the window that opens, look near the middle for
3.3. Connect the new peripherals
3.4. Test peripherals

Version -1
Page 28 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Device specifications. That's where you'll find the Device name, Processor, Installed RAM,
and other information.
A typical hardware testing process
1. Create a testing environment (e.g., measurement hardware, test software, cabling, fixtures,
etc.)
2. Place part into the condition needed for the measurement (apply pressure, voltage,
temperature, etc.)
3. Take some measurements.
4. Put those measurements through one or more pass/fail criteria.
Use the device troubleshooter to diagnose and resolve the issue.
1. Open Settings.
2. Click on Update & Security.
3. Click on Troubleshoot.
4. Select the troubleshoot that matches the hardware with the problem.
5. Click the Run the troubleshooter button.
Self check test 3.
Name __________________________________ IDNo ______________ Level
____________
Start time ___________________ Finishing time
_______________________
Instruction :- Say true or false
1. Installation refers to the particular configuration of a software only.

Version -1
Page 29 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
2. A test procedure is a formal specification of test cases to be applied to one or
more target program modules.
3. When you install a new hardware peripherals you never remove the old one.
Instruction: Write a short answer.
1. List down steps To remove a piece of hardware or peripheral from your computer?
a. ________________________________
b. ________________________________
c. ________________________________
d. ________________________________
e. ________________________________
f. ________________________________
g. ________________________________
h. ________________________________
i. ________________________________
2. What is test procedure means?
_________________________________________________________
_________________________________________________________
_________________________________________________________
_________________________________________________________
_________________________________________________________
_________________________________________________________
_________________
Instruction: Match the following columns
Column A Column B
1. Installation A. Measuring hardware
2. Test peripherals B. Configuring hardware or software
3. Input/output C. Peripherals
Unit Four:-Install and Configure peripherals to a network
This unit is developed to provide you the necessary information regarding the following content
coverage and topics
Connect peripherals to the network
Configure security
Version -1
Page 30 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Computer networking refers to interconnected computing devices that can exchange data and
share resources with each other. These networked devices use a system of rules, called
communications protocols, to transmit information over physical or wireless technologies.
A computer network is a set of computers sharing resources located on or provided by
network nodes. The computers use common communication protocols over digital
interconnections to communicate with each other.
Configure workstation
This guide will also assist you to attain the learning outcomes stated in the cover page.
Specifically, upon completion of this learning guide, you will be able to:
Meaningful names are used for peripherals and control queues
How to install software and manage peripherals
How to Allow access and security for users
Test the cable correction and operation based on organizational requirement.
How to locate peripherals its proper place
How to connect peripherals to the network
4.1. Connect peripherals to the network
Version -1
Page 31 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
A computer network, also referred to as a data network, is a series of interconnected nodes
that can transmit, receive and exchange data, voice and video traffic. Examples of nodes in a
network include servers or modems. Computer networks commonly help endpoint users share
resources and communicate.
Advantage of Networking:
Share Documents
Exchange e-mail messages
Live audio and video broadcast
Using one device for many computers like printer
Sharing external memory like Hard disk.
Security.
A computer network is mainly of four types by their geographical coverage:
1. LAN(Local Area Network)
2. PAN(Personal Area Network)
3. MAN(Metropolitan Area Network)
4. WAN(Wide Area Network)
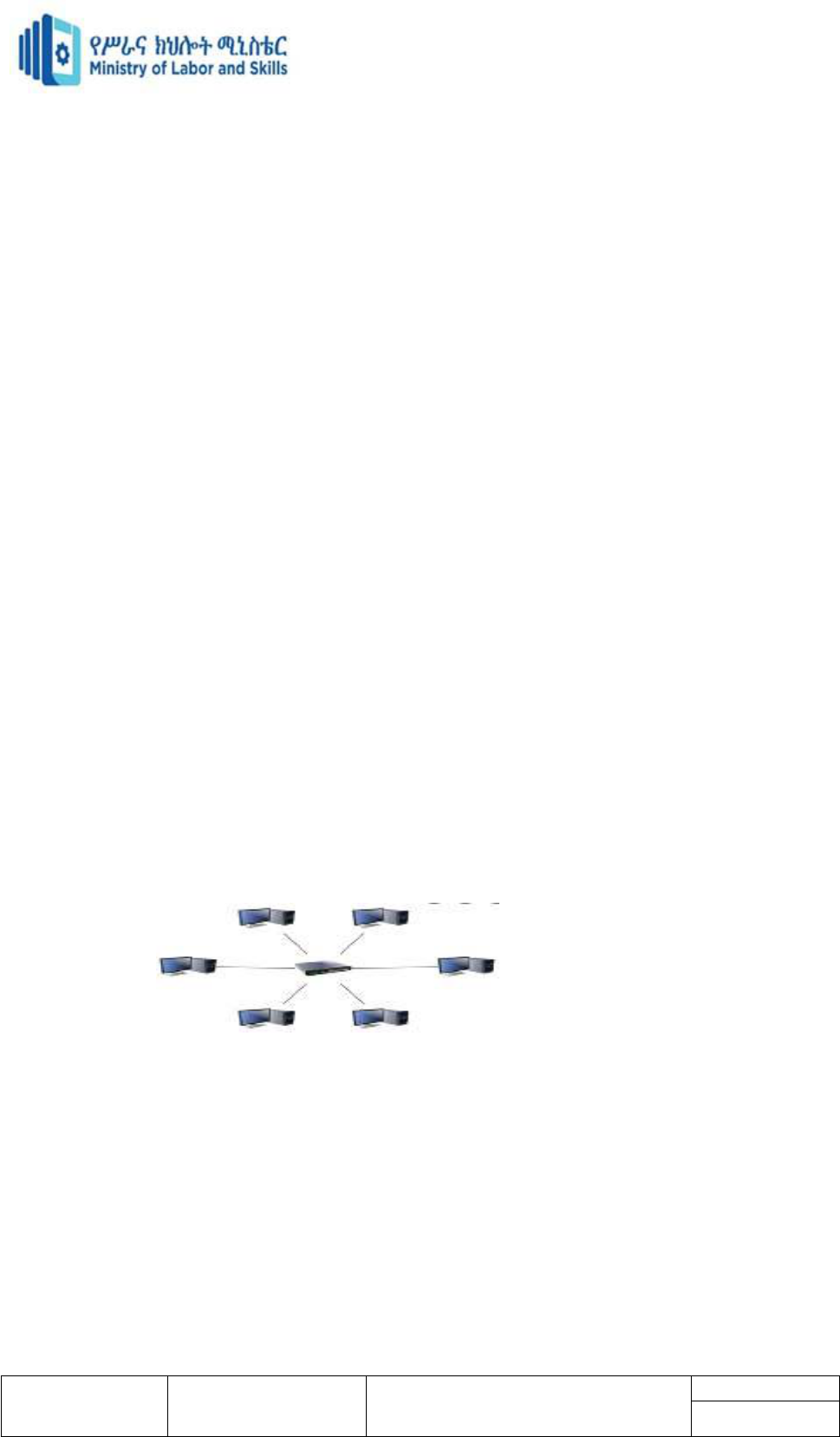
LAN(Local Area Network)
A local area network (LAN) is a collection of devices connected together in one physical
location, such as a building, office, or home.
LAN stands for local area network. A network is a group of two or more connected
computers, and a LAN is a network contained within a small geographic area, usually within
the same building. Home WiFi networks and small business networks are common examples
of LANs.
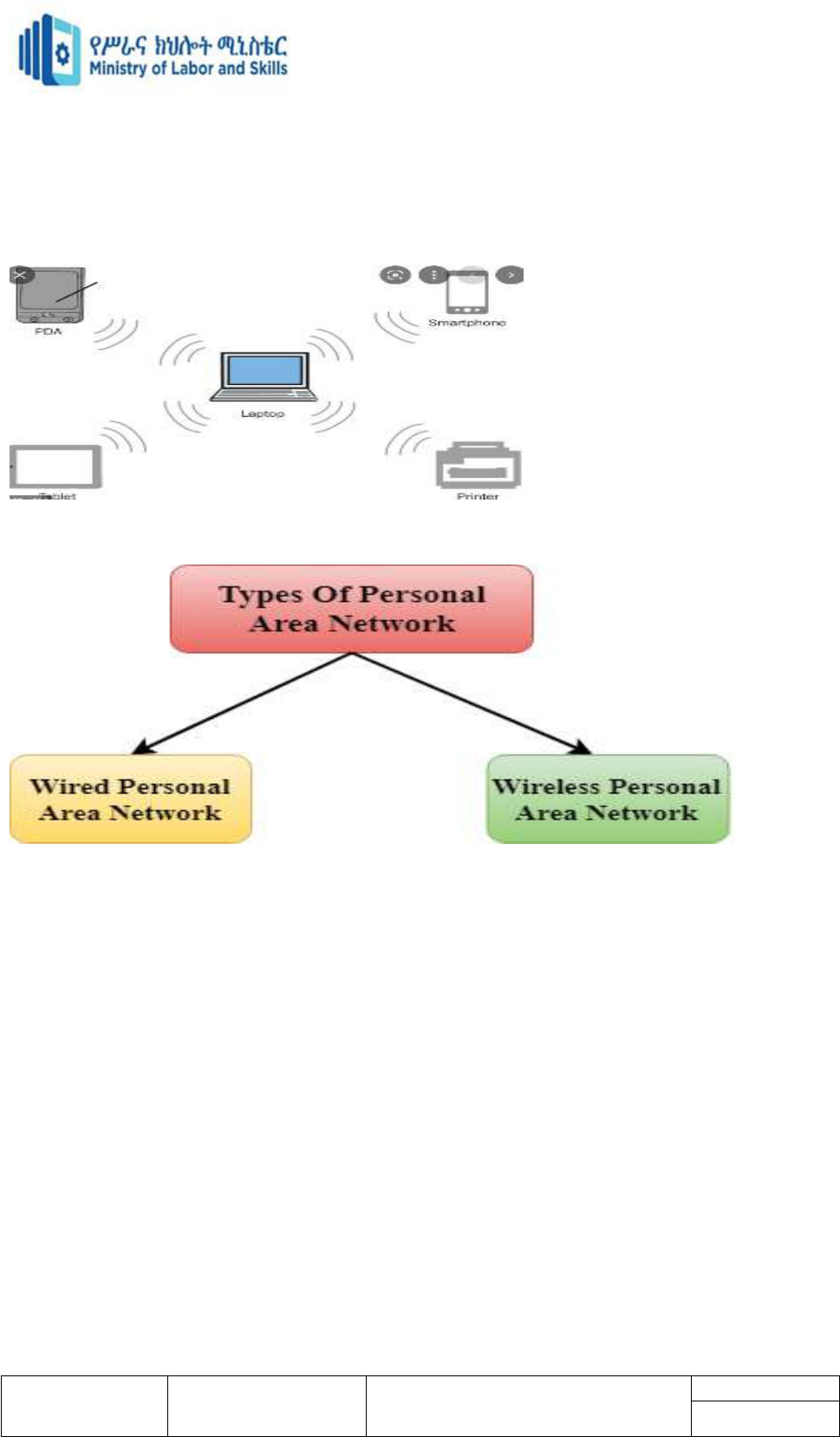
Personal area network (PAN)
A personal area network (PAN) is a computer network for interconnecting electronic devices
within an individual person's workspace. A PAN provides data transmission among devices
such as computers, smart phones, tablets and personal digital assistants.
One of the most common real-world examples of a PAN is the connection between a
Bluetooth earpiece and a Smartphone. PANs can also connect laptops, tablets, printers,
keyboards, and other computerized devices.
Features of PAN :
Low cost, little or No infrastructure setup.
Version -1
Page 32 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Short range communication.
Small personal network , use anywhere.
Wide range of devices.
Low power consumption.
No complex connectivity.
There are two types of Personal Area Network:
Wired Personal Area Network
Wireless Personal Area Network
Wireless Personal Area Network:
Wireless Personal Area Network is developed by simply using wireless technologies such as
Wi-Fi, Bluetooth. It is a low range network.
Wired Personal Area Network:
Wired Personal Area Network is created by using the USB and Network cable.
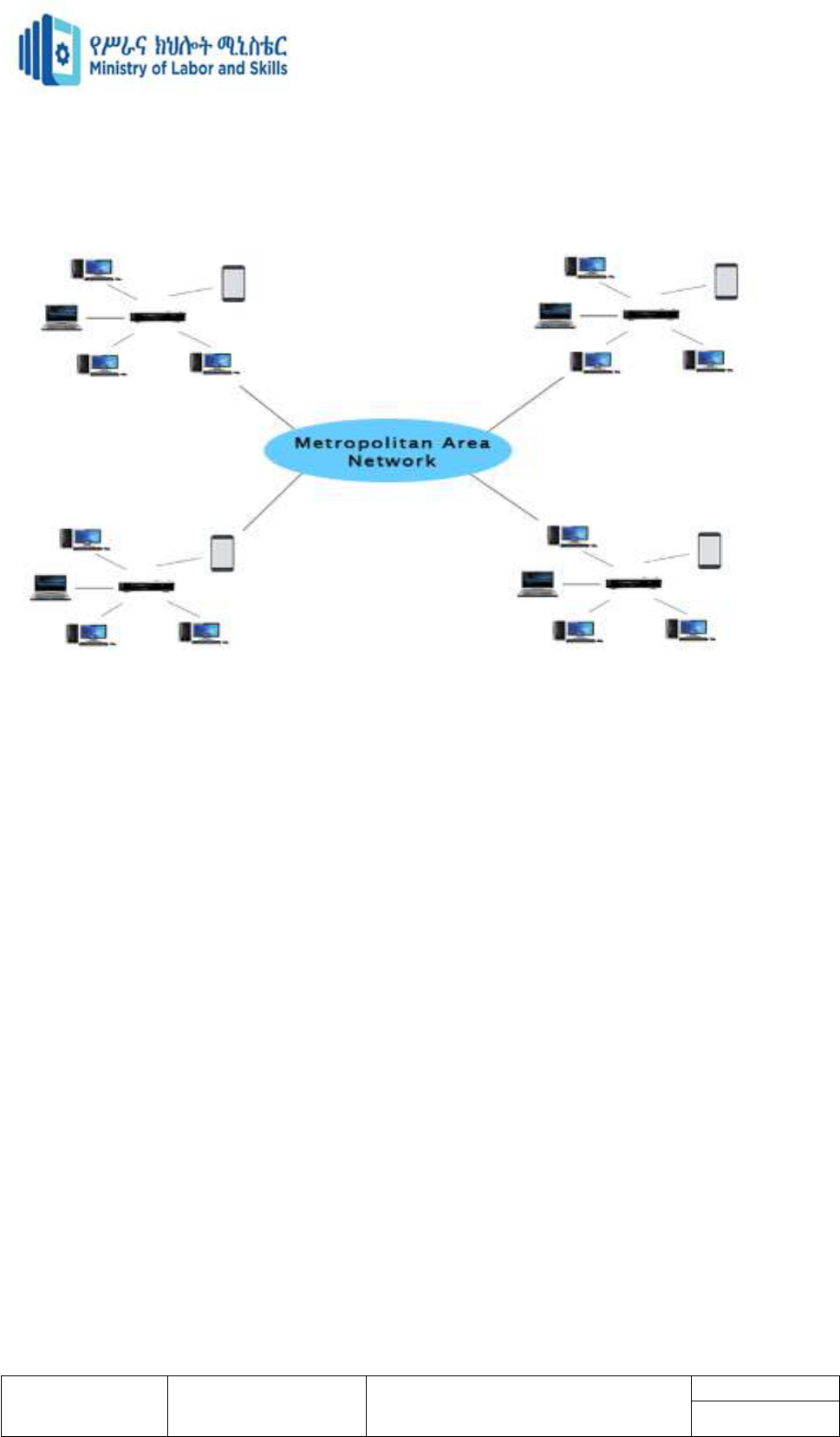
MAN (Metropolitan Area Network)
A metropolitan area network is a network that covers a larger geographic area by
interconnecting a different LAN to form a larger network.
Government agencies use MAN to connect to the citizens and private industries.
In MAN, various LANs are connected to each other through a telephone exchange line.
Version -1
Page 33 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
The most widely used protocols in MAN are RS-232, Frame Relay, ATM, ISDN, OC-3,
ADSL, etc.
It has a higher range than Local Area Network(LAN).
Uses Of Metropolitan Area Network:
MAN is used in communication between the banks in a city.
It can be used in an Airline Reservation.
It can be used in a college within a city.
It can also be used for communication in the military.
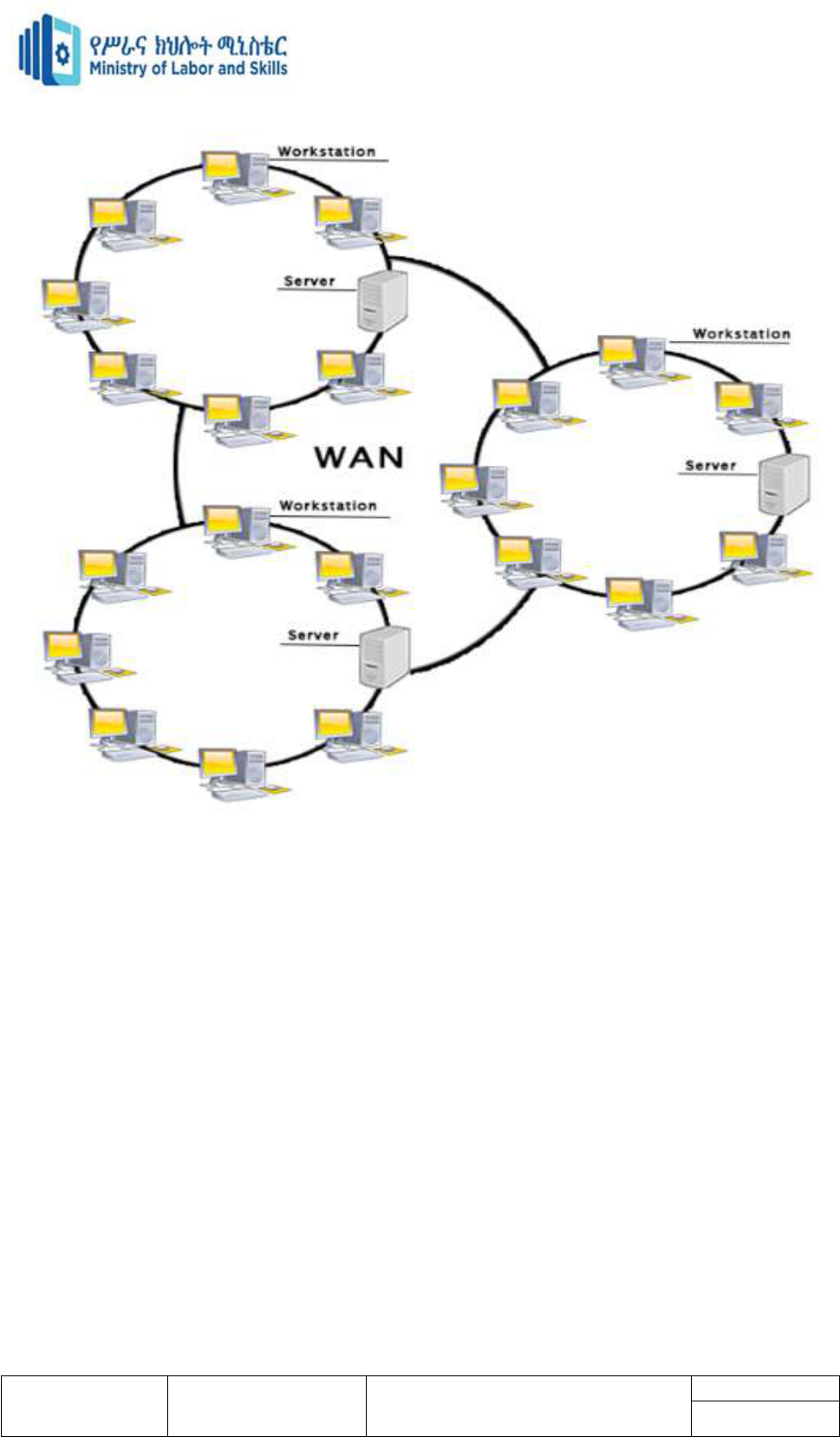
WAN (Wide Area Network)
A Wide Area Network is a network that extends over a large geographical area such as states
or countries.
A Wide Area Network is quite bigger network than the LAN.
A Wide Area Network is not limited to a single location, but it spans over a large
geographical area through a telephone line, fibre optic cable or satellite links.
The internet is one of the biggest WAN in the world.
A Wide Area Network is widely used in the field of Business, government, and education.
Version -1
Page 34 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Advantages of Wide Area Network:
Following are the advantages of the Wide Area Network:
a. Geographical area: A Wide Area Network provides a large geographical area.
Suppose if the branch of our office is in a different city then we can connect with
them through WAN. The internet provides a leased line through which we can
connect with another branch.
b. Centralized data: In case of WAN network, data is centralized. Therefore, we do not
need to buy the emails, files or back up servers.
c. Get updated files: Software companies work on the live server. Therefore, the
programmers get the updated files within seconds.
d. Exchange messages: In a WAN network, messages are transmitted fast. The web
application like Facebook, Whatsapp, Skype allows you to communicate with friends.
e. Sharing of software and resources: In WAN network, we can share the software
and other resources like a hard drive, RAM.
f. Global business: We can do the business over the internet globally.

Version -1
Page 35 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
g. High bandwidth: If we use the leased lines for our company then this gives the high
bandwidth. The high bandwidth increases the data transfer rate which in turn
increases the productivity of our company.
Disadvantages of Wide Area Network:
The following are the disadvantages of the Wide Area Network:
a. Security issue: A WAN network has more security issues as compared to LAN and
MAN network as all the technologies are combined together that creates the security
problem.
b. Needs Firewall & antivirus software: The data is transferred on the internet which
can be changed or hacked by the hackers, so the firewall needs to be used. Some
people can inject the virus in our system so antivirus is needed to protect from such a
virus.
c. High Setup cost: An installation cost of the WAN network is high as it involves the
purchasing of routers, switches.
d. Troubleshooting problems: It covers a large area so fixing the problem is difficult.
Category of computer Network by its Functional Relationship:
1. Peer-to-Peer Networking:
2. Client-Server Network
Peer-to-Peer Networking:
In peer-to-peer (P2P) networking, a group of computers are linked together with equal
permissions and responsibilities for processing data. Unlike traditional client-server
networking, no devices in a P2P network are designated solely to serve or to receive data.
In a peer-to-peer network, computers on the network are equal, with each workstation
providing access to resources and data. This is a simple type of network where computers are
able to communicate with one another and share what is on or attached to their computer with
other users.
The primary goal of peer-to-peer networks is to share resources and help computers and
devices work collaboratively, provide specific services, or execute specific tasks. As
mentioned earlier, P2P is used to share all kinds of computing resources such as processing
power, network bandwidth, or disk storage space.
Other key uses of a P2P network include: File sharing: The use of P2P in file sharing is
extremely convenient for businesses. P2P networking can also save you money with this
feature because it eliminates the need to use another intermediate server to transfer your file.
Peer-to-Peer computer network is a network that relies on computing power at the edges of a
connection, there is no hierarchy among the computers.
Advantages
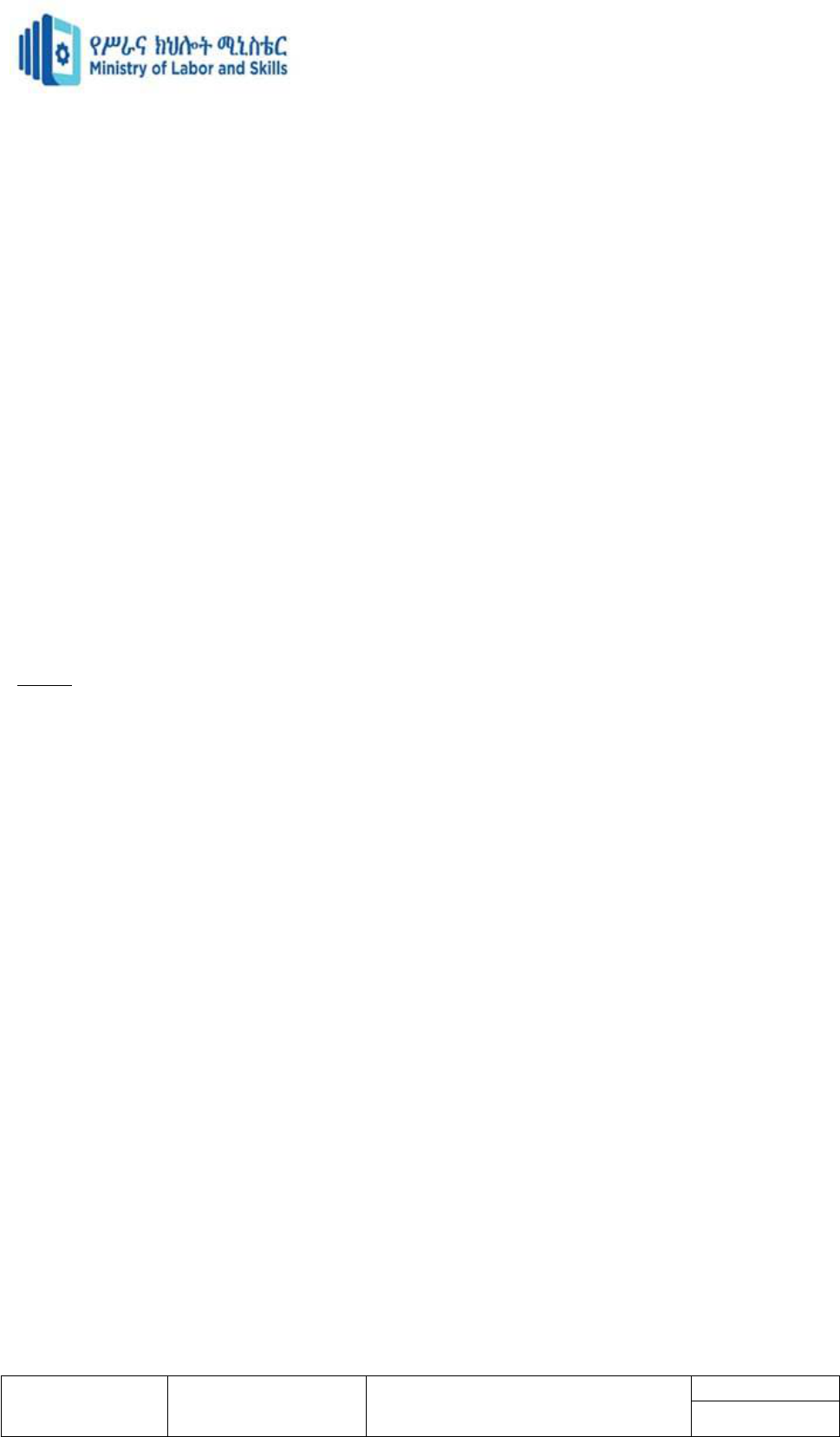
Version -1
Page 36 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Much easier to set up than a client-server network - does not need specialist
knowledge
Less initial capital – no need for a dedicated server
No need for system administration (administrator)
Disadvantages
Ensuring that viruses are not introduced to the network is the responsibility of each
individual user
Decentralized – no central repository for the files and application.
Security – does not provide the security available on a client/server network.
Client-Server Network
In the environment with more than 10 users, a peer to peer network will not adequate. There
need comes to use a dedicated computer which optimized (increase) the service of network to
clients quickly and ensure the security of files. Therefore, there will be one or more server
computers which serve other station (client) computers to optimized network system. A
dedicated computer with software that carries out some task on behalf of users.
What is Server?
Server is a dedicated computer that provide resources to Network users or Client computers.
Advantages of server-based network
Centralized – resources and data security are controlled through the server
Scalability – any or all elements can be replaced individually as need increase.
Flexibility – new technology can be easily integrated into system
Interoperability – all components (client/network/server) work together
Accessibility – server can be accessed remotely and across multiple platforms.
Disadvantages of server-Based computer networks
Expensive – requires initial investment in dedicated server
Maintenance – large networks will require a staff to ensure efficient operations
Dependence- when a server goes down, operations will cease across the network.
Server may fail- incase the server failed, the entire network goes down
Types of Server:
- File and Printer server
- Mail server
- Communication server
- Directory service server

Version -1
Page 37 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
- Application server
- Fax server
- Backup Server
Network Topology
Network topology is the arrangement of the elements of a communication network. Network
topology can be used to define or describe the arrangement of various types of
telecommunication networks, including command and control radio networks, industrial field
busses and computer networks.
Network topology is the topological structure of a network and may be depicted physically or
logically.
The term topology, or more specifically, network topology, refers to the arrangement or
physical layout of computers, cables, and other components on the network. “Topology” is
the standard term that most network professionals use when they refer to the network’s basic
design. In addition, the term “topology” you will find several other terms that are used to
define a network’s:
Physical design network diagram/Map
1. Bus Topology
2. Star Topology
3. Ring Topology
4. Mesh Topology
5. Hybrid Topology
Bus topology
, also known as line topology, is a type of network topology in which all devices in the
network are connected by one central RJ-45 network cable or coaxial cable. The single cable,
where all data is transmitted between devices, is referred to as the bus, backbone, or trunk.
An example of bus topology is connecting two floors through a single line. Ethernet networks
also use a bus topology. In a bus topology, one computer in the network works as a server
and other computers behave as clients. The purpose of the server is to exchange data between
client computers.
Version -1
Page 38 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
It is often referred to as a “linear bus” because the computers are connected in a straight line.
This is the simplest and most common method of networking computers.
In a bus topology, all computers are connected to a shared communication line, called a trunk
or a backbone.
The computers are connected to the backbone using T-connectors.
Both ends of the backbone use terminators in order to prevent reflection of signals.
If the terminator is missing or is deliberately removed, the data transmissions are disrupted.
There is no central device or any special configuration.
Advantages
A bus network is the cheapest of all topologies.
No special configuration is required.
It is easy to install, and no special equipment is
needed for installation.
It needs less cable length than do other topologies.
Disadvantages
1. A break in cable or a missing terminator can
2. bring down the entire network.
3. It is not possible to add or remove computers
4. without disrupting the network.
5. It is difficult to troubleshoot and administer.
6. Addition of more computers degrades performance.
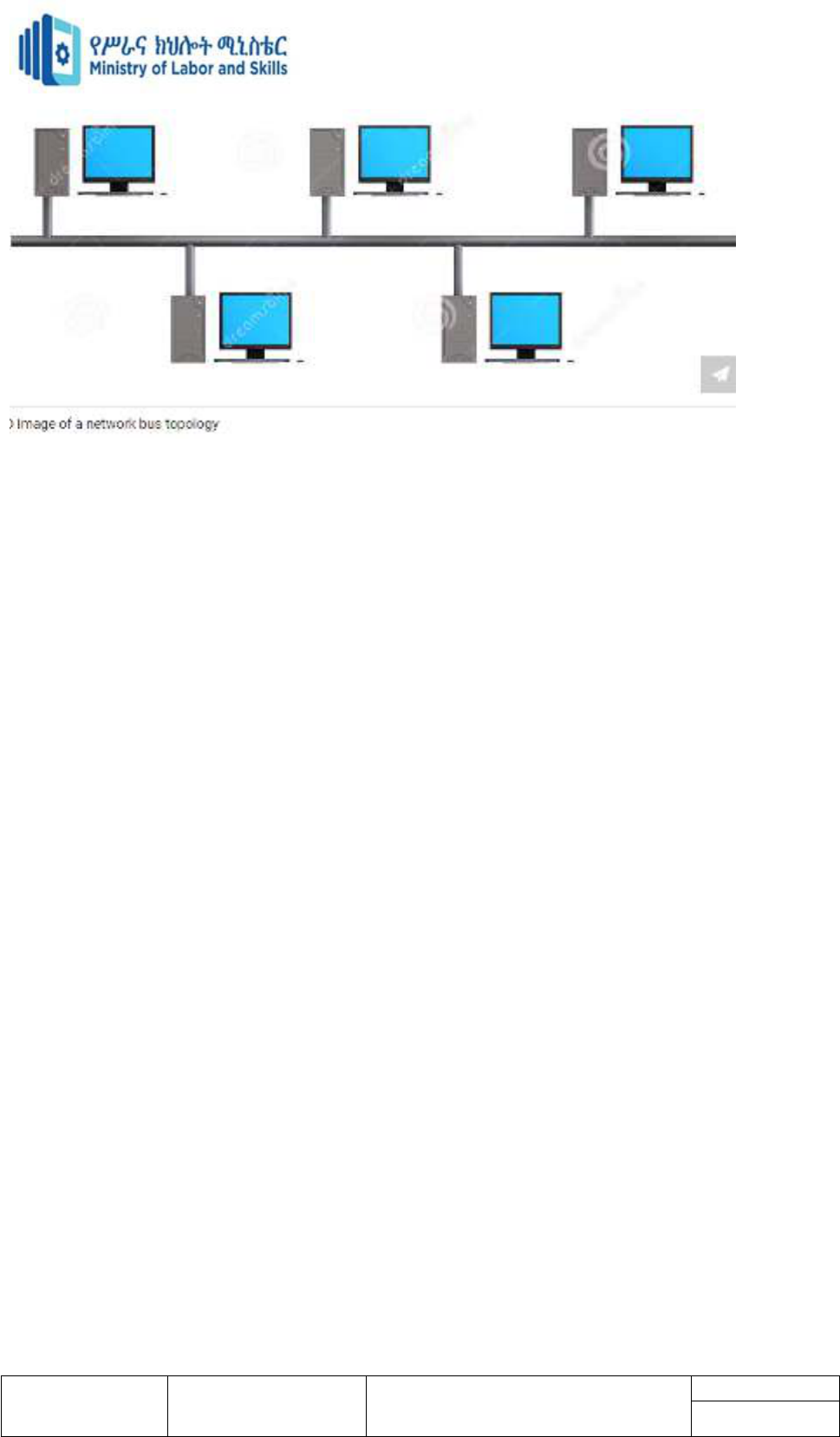
Star Topology
Version -1
Page 39 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
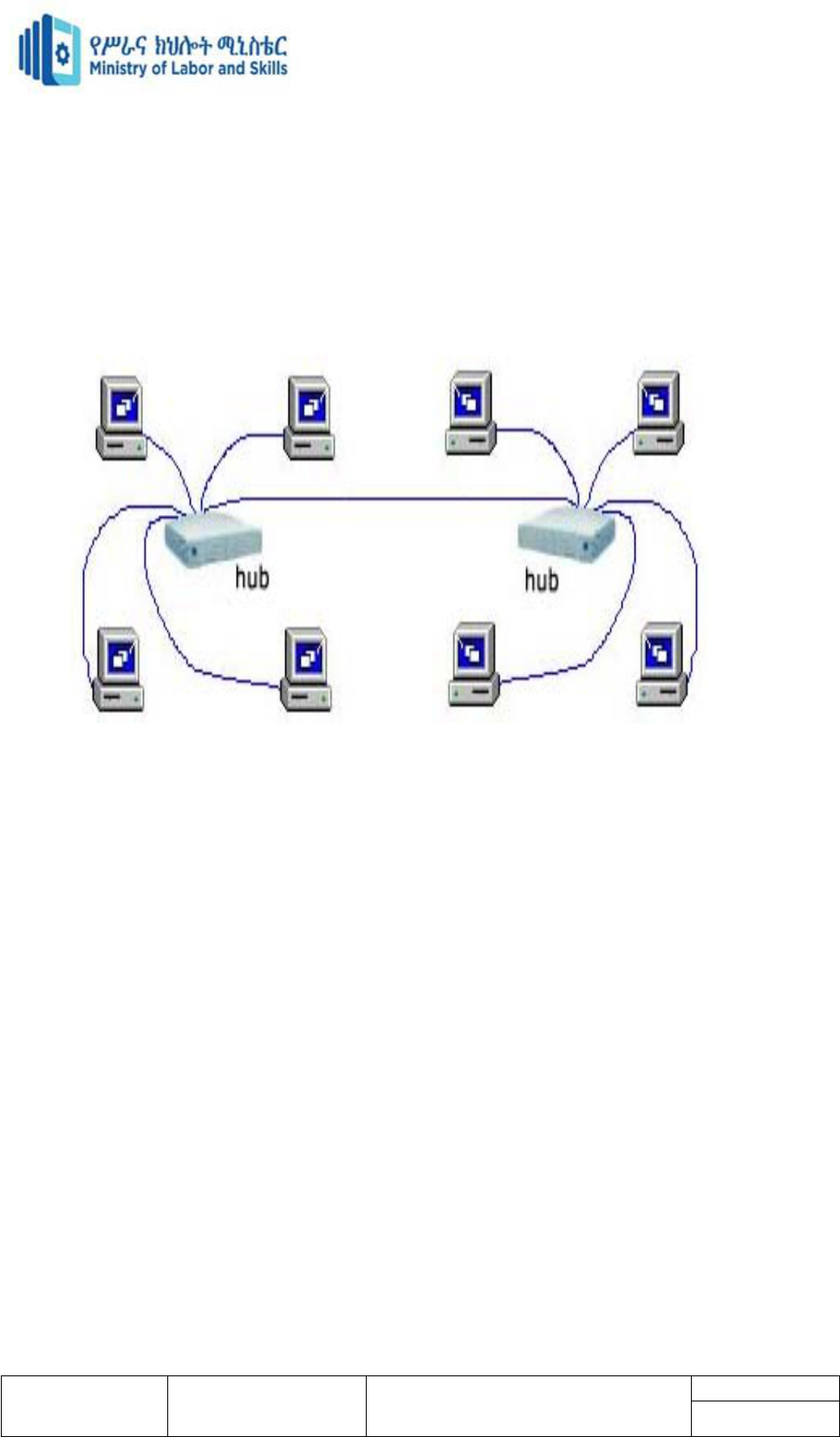
Star topology is a network topology in which each network component is physically
connected to a central node such as a router, hub or switch. In a star topology, the central hub
acts like a server and the connecting nodes act like clients.
A star network is a local area network (LAN) in which all nodes (workstations or other
devices) are directly connected to a common central Hub or Switch.
Every workstation is indirectly connected to each other through the central Hub or Switch.
Data on a star network passes through the hub, switch, or concentrator before continuing to
its destination. The hub, switch, or concentrator manages and controls all functions of the
network. It also acts as a repeater for the data flow. This configuration is common with
twisted pair cable; however, it can also be used with coaxial cable or fiber optic cable.
Advantages of a Star Topology
Easy to install and wire.
No disruptions to the network when connecting or removing devices.
Easy to detect faults and to remove parts.
Disadvantages of a Star Topology
Requires more cable length than a linear topology.
If the hub, switch, or concentrator fails, nodes attached are disabled.
More expensive than linear bus topologies because of the cost of the hubs, etc.
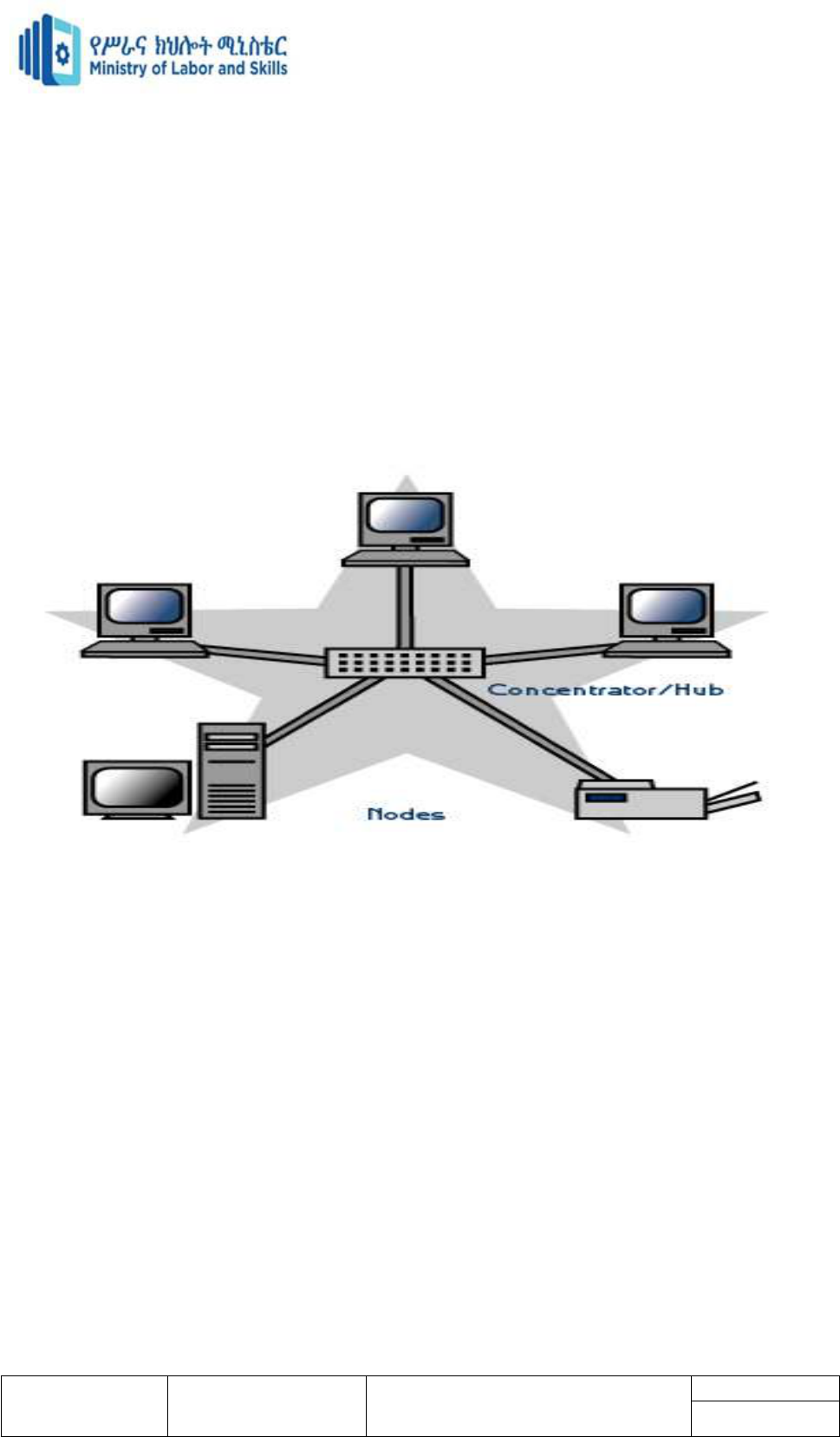
Ring topology
Ring topology is a type of network topology in which each device is connected to two other
devices on either side via an RJ-45 cable or coaxial cable. This forms a circular ring of
Version -1
Page 40 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
connected devices which gives it its name. Data is commonly transferred in one direction
along the ring, known as a unidirectional ring.
A ring network is a network topology in which each node connects to exactly two other
nodes, forming a single continuous pathway for signals through each node – a ring. Data
travels from node to node, with each node along the way handling every packet.
A Comparison Table for Advantages and Disadvantages of Ring Topology
Advantages
Disadvantages
Fast Execution
Quite Expensive
Better Administration
Slow Activity Rate
Straightforward Adaptability
Easy to install
Unprotected use
Need for Hardiness
Break in a cable /fault computer can bring slow down entire network
Difficult to troubleshoot
Version -1
Page 41 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
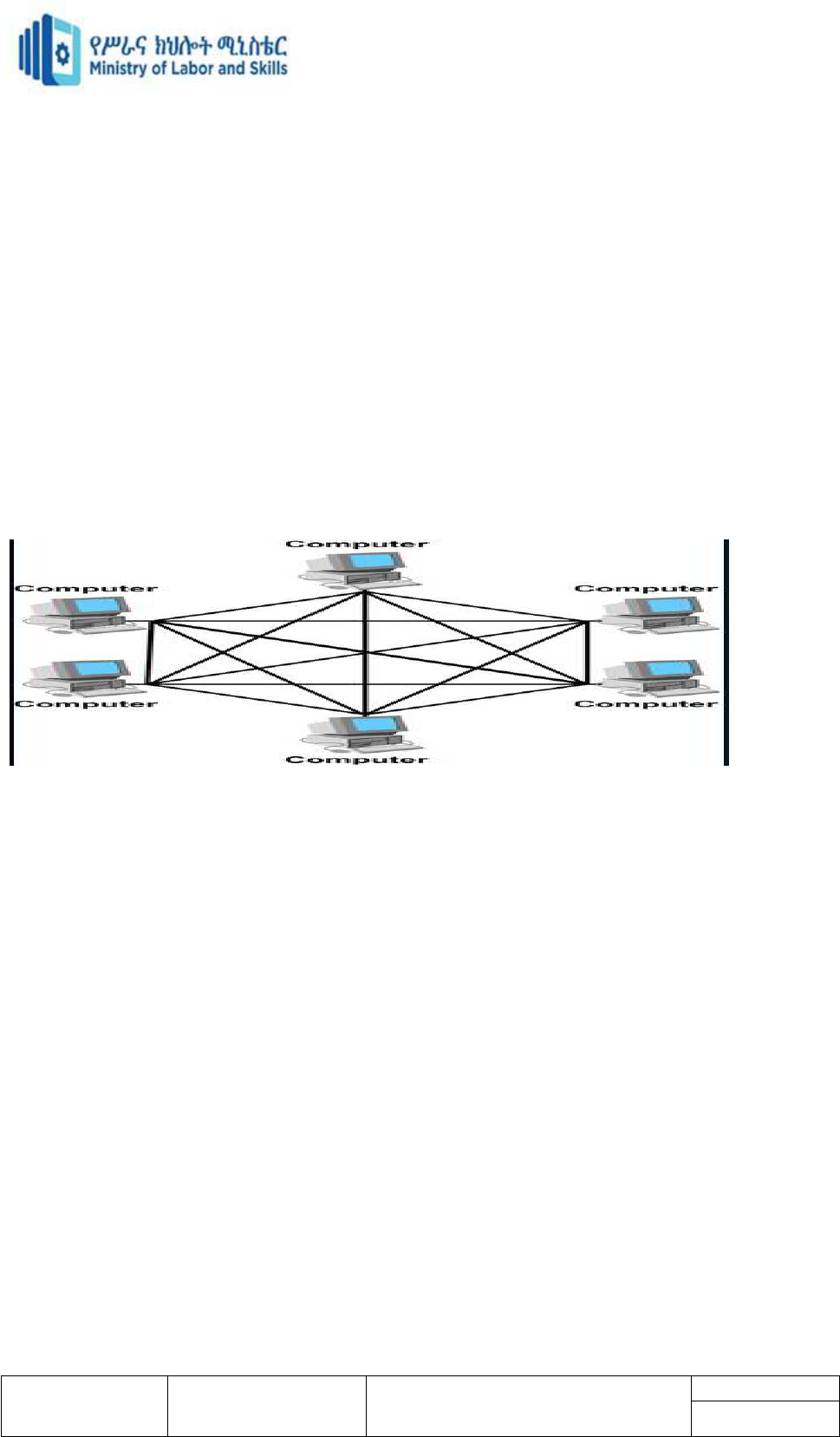
Mesh Topology
A mesh topology is a network setup where each computer and network device is
interconnected with one another. This topology setup allows for most transmissions to be
distributed even if one of the connections goes down. It is a topology commonly used for
wireless networks.
In a mesh topology, all computers in the network are connected to every other computer,
forming a mesh of connections and each computer makes a point-to-point connection to
every other computer.
There are two types of mesh topology
Full mesh topology
Each node (workstation or other device) is connected directly to each of the others.
Partial mesh topology
Some nodes are connected to all the others, but some of the nodes are connected only to
those other nodes with which they exchange the most data.
Advantages
A mesh network is highly reliable because of redundant multiple paths between
computers.
The failure of a single computer or a cable fault does not affect network operations.
Computers can be added or removed without affecting the network.
Disadvantages
It is difficult to install and troubleshoot.
It is very expensive because of the length of cable required to make multiple
redundant connections.
Only a limited number of computers can be connected in a mesh topology.
Version -1
Page 42 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Hybrid Topology
It is combination of any two or more network topologies. These instances can occur where
two basic network topologies, when connected together, can still retain the basic network
character, and therefore not be a hybrid network.
A hybrid topology is a type of network topology that uses two or more differing network
topologies. These topologies can include a mix of bus topology, mesh topology, ring
topology, star topology, and tree topology.
Advantages of Hybrid Topology
Used for a vast network
Reliable to use
Any topology can be combined to make a new network
Scalable and very effective
Disadvantages of Hybrid Topology
Costly very expensive
Difficult to install
Need more Hardware requirements
Cable failure
Some of the major applications of the hybrid topology are the financial and banking sector,
automated industries, multi-national companies, research organizations, and many
educational institutions.
The best cabled network topology for large businesses is the star topology. This is because it
is easier to control from a central console as the management software just needs to
communicate with the switch to get full traffic management features.

Version -1
Page 43 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Network Transmission Media
Transmission Media is the physical path between the transmitter and the receiver in a data
communication system.
Transmission Media categorized in two categories:-
1. Wired/Guided
2. Wireless/Unguided.
Wire/Guided Transmission Media uses a "cabling" system that guides the data signals along a
specific path. The data signals are bound by the "cabling" system. Guided Media is also
known as Bound Media. Cabling is meant in a generic sense in the previous sentences and is
not meant to be interpreted as copper wire cabling only.
Wireless/Unguided Transmission Media consists of a means for the data signals to travel but
nothing to guide them along a specific path. The data signals are not bound to a cabling
media and as such are often called Unbound Media.
Commonly types of guided transmission are:-
Twisted Pair Cable
Coaxial Cable
Optical fiber cable
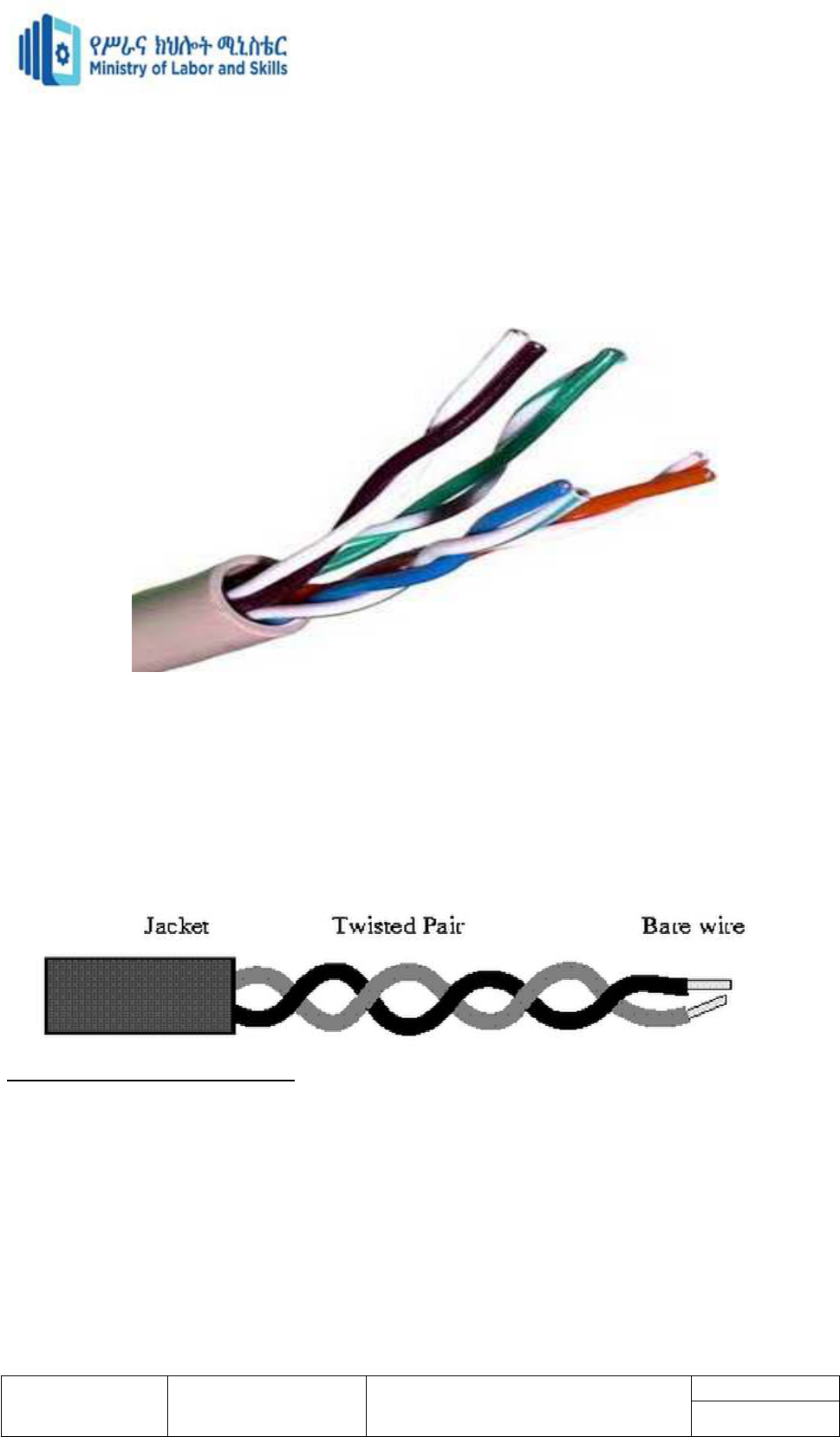
Twisted pair cable
Twisted Pair Cable
Twisted pair cabling is a type of wiring in which two conductors of a single circuit are
twisted together for the purposes of improving electromagnetic compatibility.
Twisted-pair cable consists of two insulated strands of copper wire twisted around each other.
The oldest, least expensive and most commonly used transmission media.
Two types of twisted-pair cable:-
1. Unshielded twisted-pair (UTP)
2. Shielded twisted-pair (STP) cable.
Unshielded twisted pair
(UTP)
Unshielded twisted pair
(UTP) cables are widely
used in the computer and
telecommunications industry as Ethernet cables and telephone wires. In an UTP cable,
Version -1
Page 44 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
conductors which form a single circuit are twisted around each other in order to cancel out
electromagnetic interference (EMI) from external sources.
UTP cables are mostly used for LAN networks. They can be used for voice, low-speed data,
high-speed data, audio and paging systems, and building automation and control systems.
UTP cable can be used in both the horizontal and backbone cabling subsystems.
It is the most commonly used cable types in LANs.
It is made up of four twisted pairs enclosed in a plastic jacket.
Depending on the bandwidth offered there are seven types of UTP cables such as Cat-1,Cat-
2,cat-3,cat-4,cat-5,cat-6 and cat-7
The Most commonly used UTP cables are category-5 cables and its bandwidth is 1000Mbps.
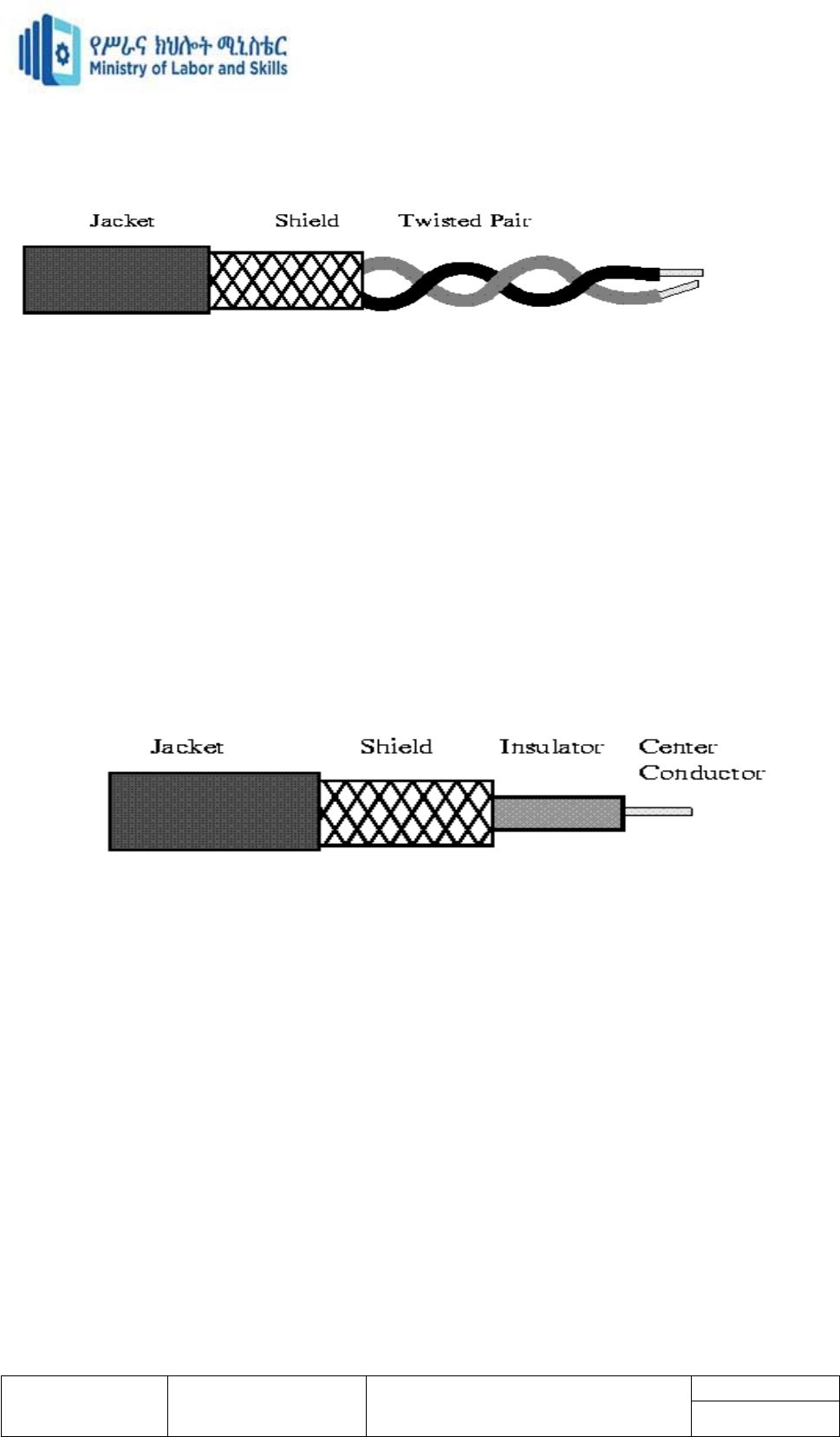
Shielded Twisted Pair (STP) cable
Uses a woven copper braid jacket and higher quality protective jacket. Also uses foil wrap
b/n and around the wire pairs
Much less susceptible to interference and supports higher transmission rates than UTP
shielding makes it somewhat harder to install
same 100 meters limit as UTP
Version -1
Page 45 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
uses RJ-45 telephone-type connectors (larger than telephone and consists of eight wires vs.
telephone’s 4 wires)
Coaxial Cable
Coaxial Cable consists of 2 conductors. The inner conductor is held inside an insulator with
the other conductor woven around it providing a shield. An insulating protective coating
called a jacket covers the outer conductor.
The outer shield protects the inner conductor from outside electrical signals. The distance
between the outer conductor (shield) and inner conductor plus the type of material used for
insulating the inner conductor determine the cable properties or impedance. Typical
impedances for coaxial cables are 75 ohms for Cable TV, 50 ohms for Ethernet Thinnet and
Thicknet. The excellent control of the
impedance characteristics of the cable allow higher data rates to be transferred than Twisted
Pair cable.
Fiber optic (Optical Fiber)
Optical fiber is the technology associated with data transmission using light pulses travelling
along with a long fiber which is usually made of plastic or glass. Metal wires are preferred for
transmission in optical fiber communication as signals travel with fewer damages. Optical
fibers are also unaffected by electromagnetic interference. The fiber optical cable uses the
application of total internal reflection of light. An optical fiber consists of an extremely thin
cylinder of glass, called the core, surrounded by a concentric layer of glass, known as the
cladding. The fibers are sometimes made of plastic. Plastic is easier to install, but cannot
carry the light pulses for as long a distance as glass.
The basic function of any optical fiber is to guide light, i.e., to act as a dielectric waveguide.
Light injected into one end should stay guided in the fiber. In other words, it must be
prevented from getting lost e.g. by reaching the outer surface and escaping there. We explain
this here for glass fibers, but the operation principle of plastic optical fibers is the same.
Version -1
Page 46 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
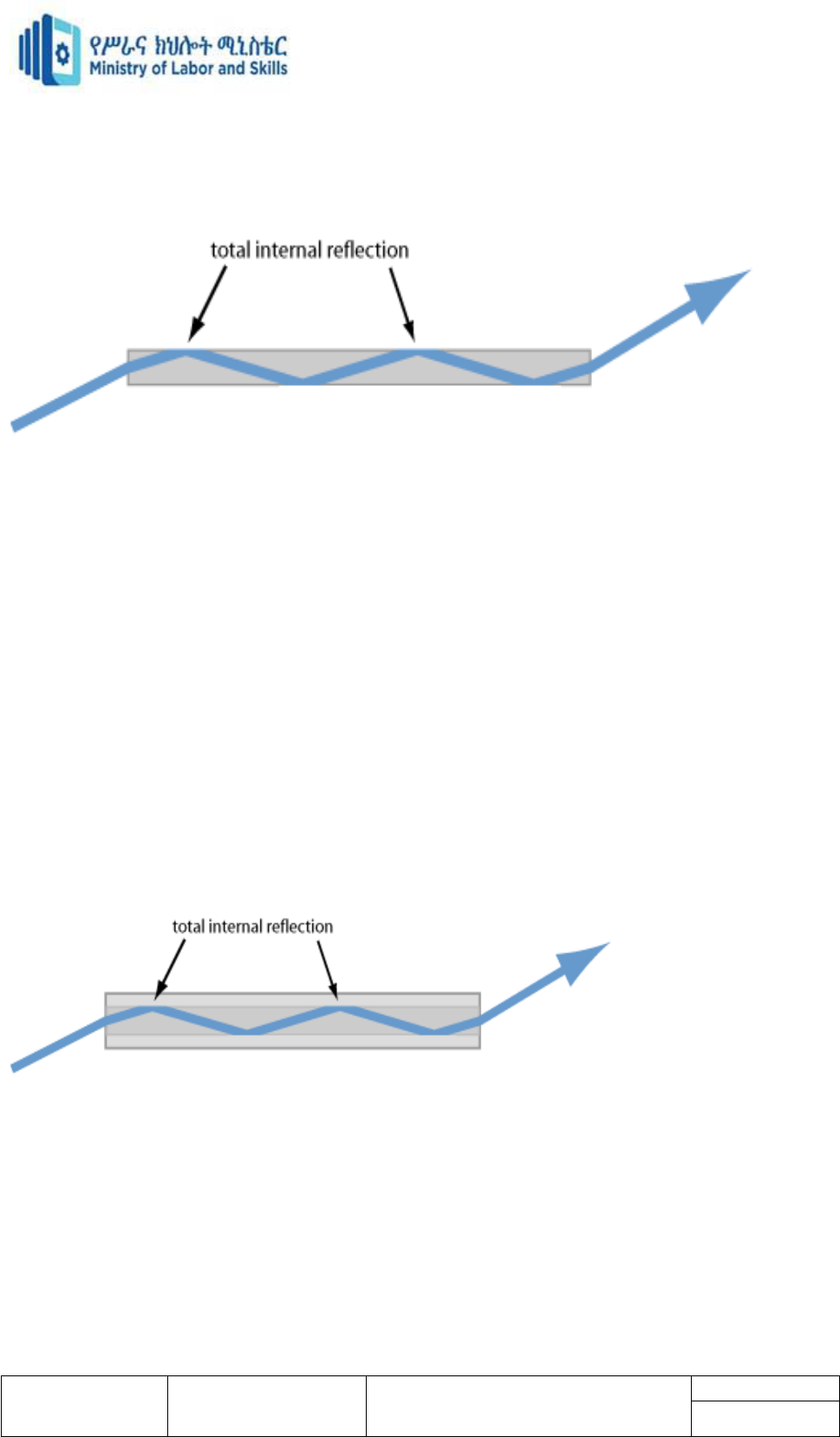
In principle, the simplest solution for guiding light would be a homogeneous glass rod. If it is
thin enough, it can also be bent to some degree. The outer surface can reflect light via total
internal reflection. Due to the large refractive index contrast, this works for a considerable
range of input beam angles, and in principle there don't need to be any power losses.
Figure 1: Total internal reflection can be used to guide light in a homogeneous fiber. Note
that only partial reflection occurs at the end faces, where the angle of incidence is smaller.
However, this simple solution has some crucial disadvantages.
Due to the high index contrast, even tiny scratches of the glass on the outer surface could lead
to substantial optical losses by scattering. Therefore, the outer surface would have to be made
with high optical quality and well protected against damage and dirt. This problem can be
mitigated only to some extent with some suitable buffer coating around the fiber. Such
coatings, not being highly homogeneous, can hardly provide very low optical losses.
Even if the fiber were pretty thin (e.g., with a diameter of 0.1 mm), it would support a huge
number of modes which is bad e.g. when preserving a high beam quality is important.
One can, however, modify the idea of a very clean coating. Use another glass region, having
a slightly smaller refractive index than the core glass, as a cladding:
Figure 2: A multimode glass fiber with a cladding, made of glass with a slightly lower
refractive index. Total internal reflection can occur at the glass/glass interface, but the
incidence angles need to be larger.
That gives us several advantages. Glass can be much more clean and homogeneous than a
plastic buffer coating. That already reduces the losses.
Version -1
Page 47 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Due to the reduced index contrast at the reflection points, small irregularities of the interface
do not cause as serious optical losses as for a glass/air interface. Irregularities at the outer
interface do not matter anymore, as the light cannot “see” them.
The guiding region – called the fiber core – can now be made much smaller than the total
fiber, if this is wanted. One can adapt the core size e.g. to the size of some small light emitter.
With a combination of small core size and weak index contrast one can even obtain single-
mode guidance (see below).
Note, however, that smaller index contrasts imply a smaller acceptance angle: total internal
reflection can only occur if the incidence angle is above the critical angle. The maximum
angle of incidence at the input face of the fiber is then determined by the numerical aperture
(NA).
Two types of
optical fiber
are commonly
available:
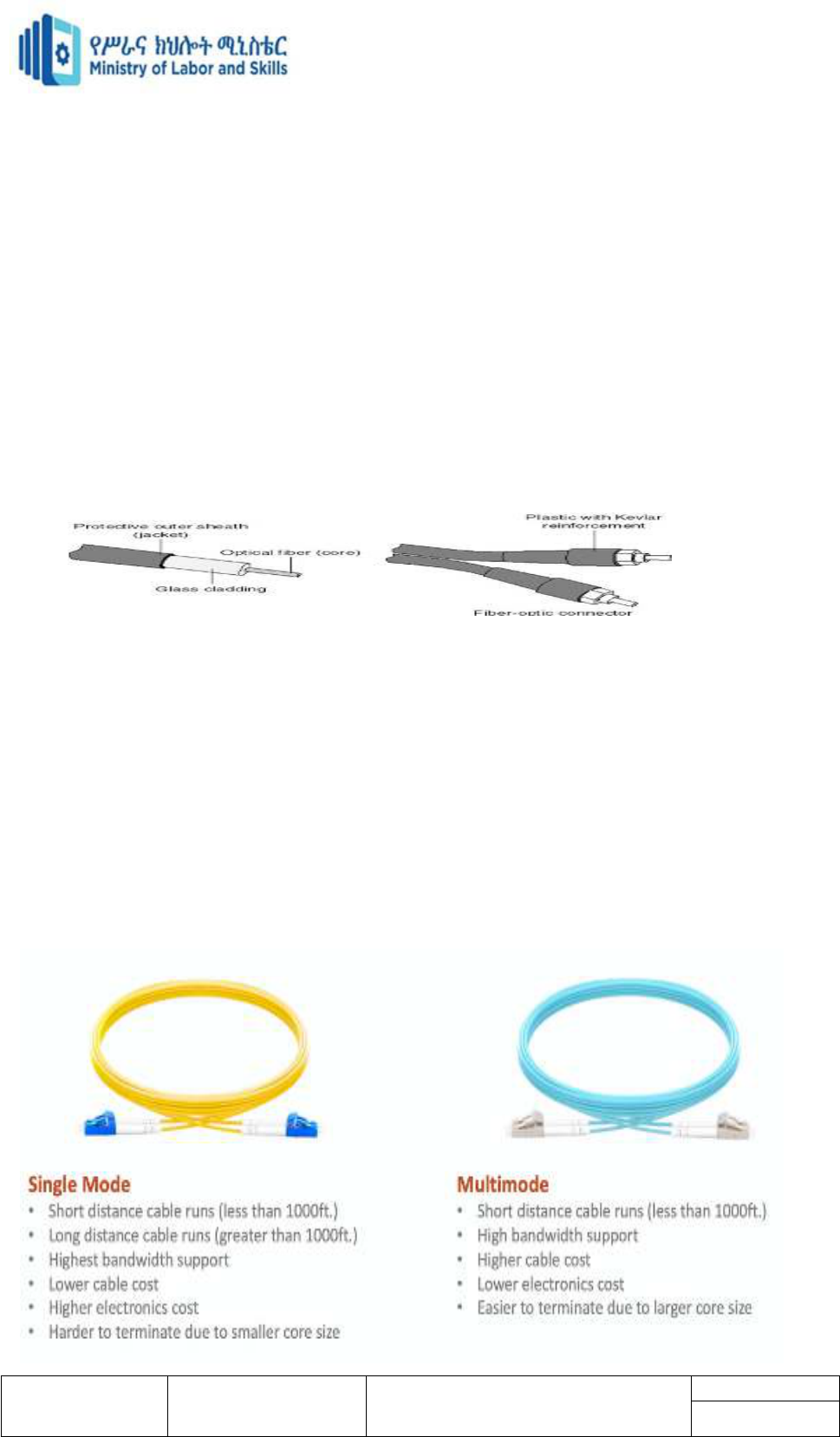
4. Single-mode and Multimode.
Single-mode fiber is used for long runs because it can transmit data 50 times further than
multimode fiber and at a faster rate. For example, single-mode fiber might be used on an
organization’s corporate campus between buildings. Single-mode fiber (SMF), on the other
hand, has a small core that allows only a single light beam to pass. The light transmissions in
single-mode fiber pass through the core in a direct line, like a flashlight beam.
So what's better? Single mode or multimode Well, they are different.... Single mode cable is
less expensive, supports higher bandwidths and longer distances; however, the cost of
electronics is greater.
Version -1
Page 48 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Multimode fiber (MMF)
Multimode fiber (MMF) has a larger core than single-mode. This larger core allows hundreds
of light rays to flow through the fiber simultaneously.
The numerous light beams in multimode fiber bounce around inside the core, inching toward
their destination. Because light beams bounce within the core, the light beams slow down,
reduce in strength, and take some time to travel along the cable. Multimode fiber provides
high bandwidth at high speeds over medium distances (up to about 3000 feet) but can be
inconsistent for very long runs.
Types of LAN cables and connectors
Cable Type
Maximum
Speed
Maximum
Cable length
Advantages
Disadvantages
Connector
used
STP
100Mbps
185m
Resistant to EMI
Expensive
D-shell
connector
UPT
100Mbps
185m
Inexpensive
Easy to install
Resistant to
physical stress
Not resistant to EMI
RJ-45
connector
Coaxial
10Mbps
185m, 500m or 10
km
Easy to install
Less sensitive to
EMI than UTP/STP
Not resistant to
physical stress
Expensive compared
to UTP
BNC
Connector
T-connector
Terminator
Optical
Fiber
155Mbps-
1000Mbps
10km depending on
the fiber type
Resistant to EMI
High data transfer
rate
Expensive
Difficult to install
SMA
connector
Version -1
Page 49 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
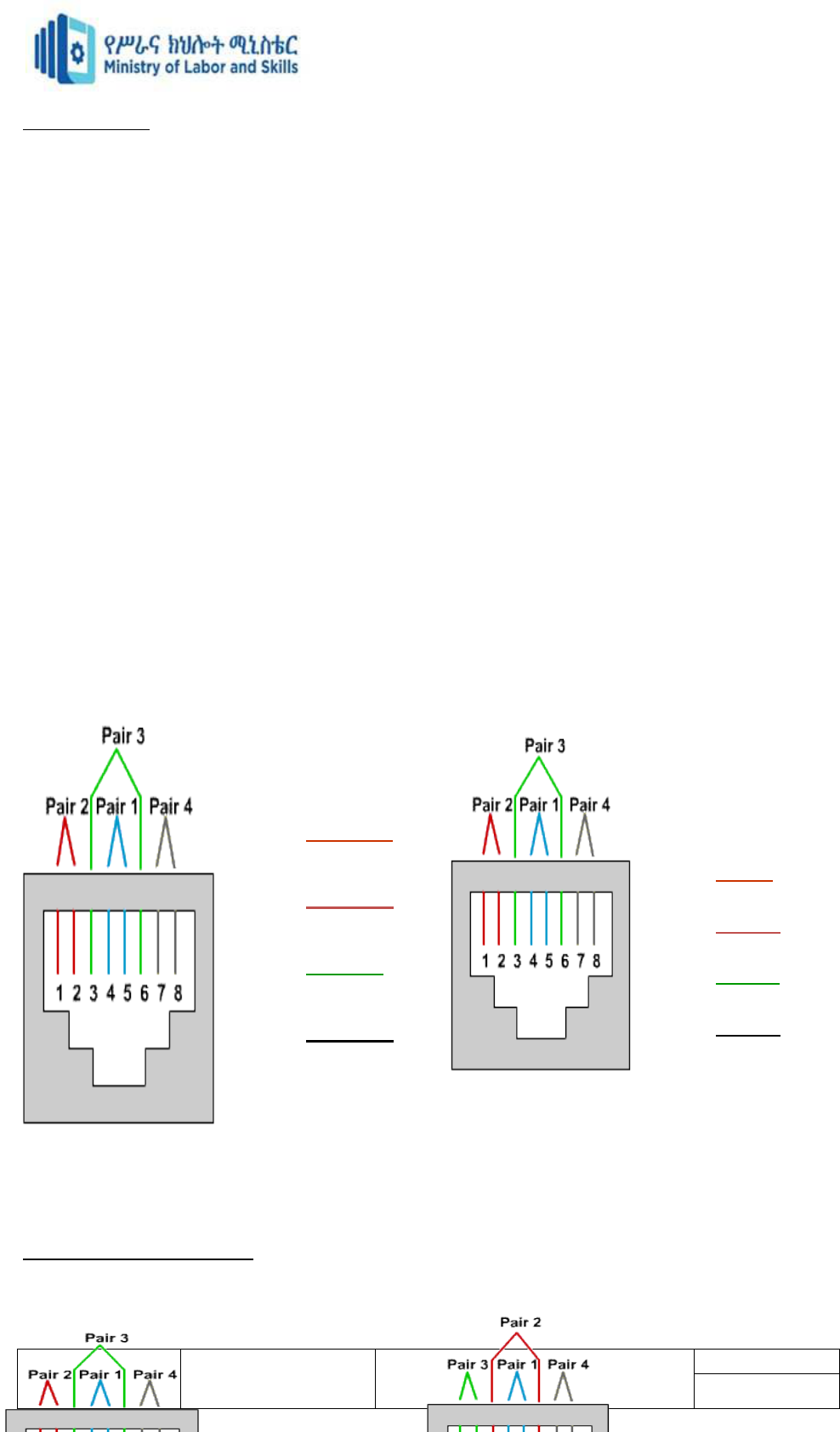
1: Transmit
2: Transmit
3: Receive
4: Not used
5: Not used
6: Receive
7: Not used
8: Not used
1: Receive
2: Receive
3: Transmit
4: Not used
5: Not used
6: Transmit
7: Not used
8: Not used
Cabling system
Three types of Ethernet cables are available
Straight-through cable
Crossover cable
Rolled cable
Making Ethernet 10Base-T cables:
Straight-through cable: PC-to-HUB.
Crossover cable: PC-to-PC.
Making console cables:
Rollover cable:
10Base-T: NIC network port 10Base-T: HUB network port
10Base-T: Cross Over cable
10Base-T: T568-B 10Base-T: T568-A
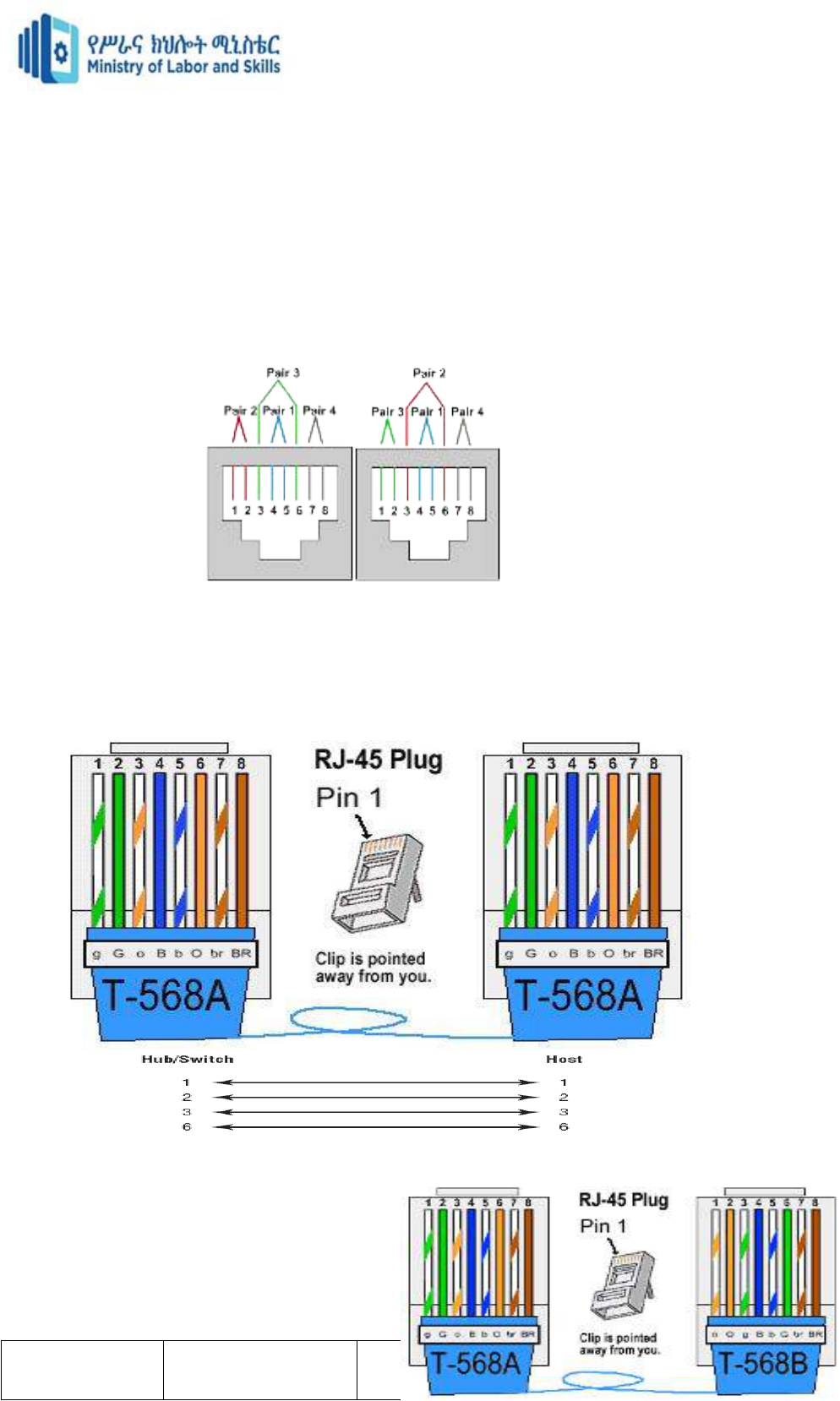
Version -1
Page 50 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
1: White Orange
2: Orange
3: White Green
4: Blue
5: White Blue
6: Green
7: White Brown
8: Brown
1: White Green
2: Green
3: White Orange
4: Blue
5: White Blue
6: Orange
7: White Brown
8: Brown
1: White Orange
2: Orange
3: White Green
4: Blue
5: White Blue
6: Green
7: White Brown
8: Brown
1: White Green
2: Green
3: White Orange
4: Blue
5: White Blue
6: Orange
7:
White Brown
8: Brown
PC
PC
The straight-through cable is used to connect
Host to switch or hub
Router to switch or hub
The crossover cable can be used to connect
Switch to switch
Hub to hub
Host to host
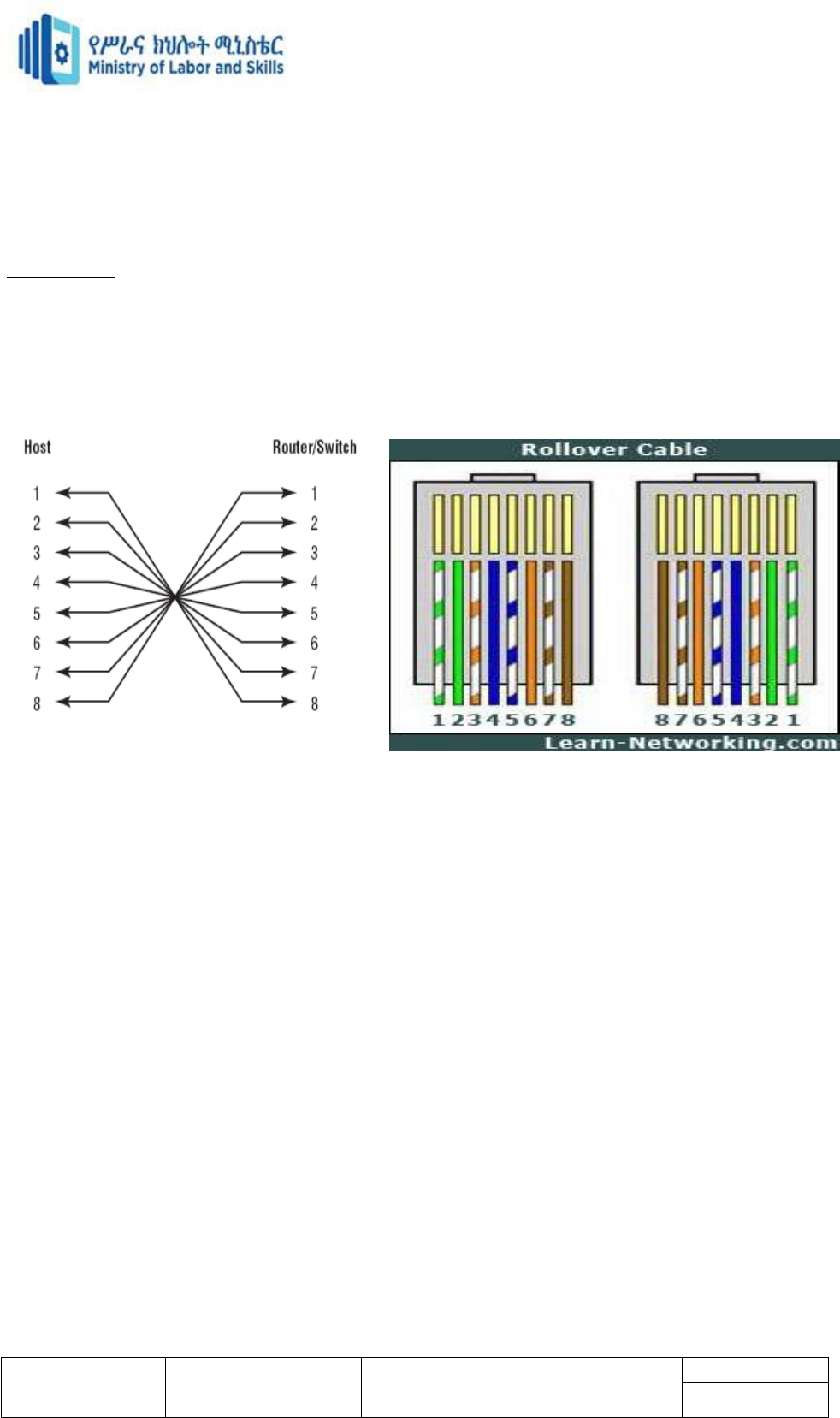
Version -1
Page 51 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Hub to switch
Router direct to host
Pc to Pc
Rolled Cable
You can use a rolled Ethernet cable to connect a host to a router console serial
communication (com) port.
Connect peripherals with the computer
What are some common computer peripherals? There are three kinds of peripherals: input,
input/output, and output devices. Some common computer peripherals include keyboards,
mice, tablet pens, joysticks, scanners, monitors, speakers, printers, external hard drives,
network devices and media card readers.
Keyboard, mouse, monitor, printer, scanner, and USB drive are examples of peripheral
devices.
Networking Devices
The network device is one kind of device used to connect devices or computers together to
transfer resources or files like fax machines or printers. 2). What are the examples of network
devices? The examples are switch, hub, bridge, router, gateway, modem, repeater & access
point.
Here is the common network device list:
Hub
Switch

Version -1
Page 52 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Router
Bridge
Gateway
Modem
Repeater
Access Point
HUB
A network hub is a node that broadcasts data to every computer or Ethernet-based device
connected to it. A hub is less sophisticated than a switch, the latter of which can isolate data
transmissions to specific devices. Network hubs are best suited for small, simple local area
network (LAN) environments.
In general, a hub refers to a hardware device that enables multiple devices or connections to
connect to a computer. An example is a USB hub, which allows multiple USB devices to
connect to one computer, even though that computer may only have a few USB connections.
There are three types of network hubs: passive, active, and intelligent. network. They do not
improve the performance of local area networks (LANs), and may limit maximum media
distances. Typically, passive hubs are connected to other devices in a star configuration.
Switch

Version -1
Page 53 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Just like a hub and a bridge, a switch is also used to connect multiple devices in a LAN
segment. A switch is the upgraded version of the bridge. Besides providing all the
functionalities of a bridge, it also offers several additional features.
The biggest advantage of a switch is that it makes switching decisions in hardware by using
application-specific integrated circuits (ASICs).
Unlike the generic processors that we use in our PC, ASICs are specialized processors built
only to perform particular tasks. Usually, the ASICs in switches have a single task and that is
switching the frames as fast as they can.
An ASIC occupied switch performs this task blazingly fast. For example, an entry-level 2960
Catalyst Switch can process 2.7 million frames per second.
Router
A router connects different network segments. It switches data packets between networks that
are either located in different logical segments or constructed with different network-layer
protocols.
A router is a networking device that forwards data packets between computer networks.
Routers perform the traffic directing functions on the Internet.
When a router receives a data packet on any of its interfaces, it checks the destination address
of that packet, and based on that destination address, forwards that data packet to the
interface that is associated with the destination address.
To forward data packets to their destination, the router keeps a record of the connected
network. These records are maintained in a database table known as the routing table.
Routing tables can be created statically or dynamically.

Version -1
Page 54 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
The following image shows two routers.
The main functions of routers are the following: -
3. To connect different network segments.
4. To connect different network protocols such as IP and IPX.
5. To connect several smaller networks into a large network.
6. To break a large network into smaller networks.
7. To connect two different media types such as UTP and Fiber optical.
8. To connect two different network architectures such as Token Ring and Ethernet.
9. To connect LAN network with Telco company's office.
10. To access DSL services.
Bridge
A bridge is used to divide a large network into smaller segments. The basic functions of a
bridge are the following: -
1. Breaking a large network into smaller segments.
2. Connecting different media types such as UTP and fiber optic.
3. Connecting different network architectures such as Ethernet and the Token ring.
The following image shows an example of a bridge.
A bridge can connect two different types of media or network architecture, but it cannot
connect two different types of network layer protocols such as TCP/IP or IPX. It requires the
same network-layer protocols across all segments.
Version -1
Page 55 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
There are three types of bridge:-
Local Bridge: - The Bridge directly connects two LAN segments. In Ethernet
implementations, this is known as a transparent bridge. In the Token Ring network, this is
called a source-routed bridge.
Remote Bridge: - This Bridge connects with another Bridge over the WAN link.
Wireless Bridge: - This Bridge connects with another Bridge without using wires. It uses
radio signals for connectivity.
In networking models such as the OSI layers model and TCP/IP model, the functionalities of
Bridges are defined in the physical layer and data link layer.
Just like a Hub, a Bridge is also no longer used in the computer network. Bridges have been
replaced by switches.
Gateway

Version -1
Page 56 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Gateway is used to forward packets that originate from a local host or a local network and are
intended for remote networks. If a data packet does not get its destination address in the local
network then it takes the help of the gateway device to find the destination address in the
remote network. The gateway device knows the path to the remote destination address. If
necessary, it also encapsulates the packet so that it can travel through other networks to reach
its destination address.
The following image shows a gateway device.
Examples of the Gateway
Email Gateway: - An email gateway translates SMTP e-mails in standard X.400 format
before forwarding.
GSNW Gateway: - A GSNW gateway allows Windows clients to access resources from the
NetWare server.
PAD Gateway: - A PAD gateway provides connectivity between a LAN network and an X.25
network.
Modem
In simple language, a modem is a device that is used to connect to the Internet. Technically, it
is the device that enables digital data to be transmitted over telecommunication lines.
A Telco company uses entirely different data transmission technology from the technology
that a PC uses for data transmission. A modem understands both technologies. When it
receives signals from the PC, it converts them into the format that the Telco company
understands. When it receives signals from the Telco company, it converts them into a format
that the PC understands.
It enables communication between the PC (Known as the DTE device) and the Telecom
company's office (Known as the DCE device).

Version -1
Page 57 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Repeater
Repeaters are usually used to strengthen signals going long distances.
A repeater amplifies the signal it receives on one port before it transmits it on other ports.
Because the repeater does not check on the contents of the data it receives or retransmits,
frames that are corrupted by noise and other factors can also be repeated.
The development of the hub replaced the repeater for all practical purposes, because it
performs the same functions, and can include additional features.
Network Interface Cards (NICs)
NICs are the mechanisms by which computers connect to a network.
NICs come in all shapes and sizes, and they come in prices to suit all budgets.
Known as network card, network adapter, and LAN adapter, etc.
When buying one consider
1. Network compatibility – Ethernet/Token Ring
2. Bus compatibility – PCI/ ISA /PCI-e
3. Port compatibility – UTP/ Fibre
4. Hardware compatibility – Easy to install / Recognized by many OS’s
Version -1
Page 58 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Wireless Access Point (WAP)
are a transmitter and receiver (transceiver) device used for wireless LAN (WLAN) radio
signals.
Depending on the size of the network, one or more WAPs may be required. Additional WAPs
are used to allow access to more wireless clients and to expand the range of the wireless
network.
Transceivers
The term transceiver does not necessarily describe a separate network device but rather an
integrated technology embedded in devices.
transceiver = transmitter and a receiver
device that receives data, converts it, and then sends it to another location
RF transceivers, fiber-optic transceivers, Ethernet transceivers, are examples
can also be used in pairs to insert a fiber segment into copper networks

Version -1
Page 59 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Firewall
a hardware or software system that is used to separate one computer or network from another
one.
The most common type is used to protect a computer or an entire network from unauthorized
access from the Internet.
can also be used to control the flow of data to and from multiple networks within the same
organization. Firewalls
can be programmed to filter data packets based on the information that is contained in the
packets.
IP Terminology
Bit A bit is one digit, either a 1 or a 0.
Byte A byte is 7 or 8 bits, depending on whether parity is used.
Octet An octet, made up of 8 bits, is just an ordinary 8-bit binary number.
Network address This is the designation used in routing to send packets to a remote network
for example, 10.0.0.0, 172.16.0.0, and 192.168.10.0.
You can depict an IP address using one of three methods:
Dotted-decimal, as in 172.16.30.56
Binary, as in 10101100.00010000.00011110.00111000
Hexadecimal, as in AC.10.1E.38
Summary of the three classes of networks
Network Address Range: Class A
0xxxxxxx

Version -1
Page 60 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
00000000 = 0
01111111 = 127
Network Address Range: Class B
10000000 = 128
10111111 = 191
Network Address Range: Class C
11000000 = 192
11011111 = 223
Network Address Ranges: Classes D and E
The addresses between 224 to 255 are reserved for Class D and E networks.
Class D (224–239) is used for multicast addresses and Class E (240–255) for scientific
purposes Private IP Addresses.
Subnet Masks
A subnet mask is a 32-bit value that allows the recipient of IP packets to distinguish the
network ID portion of the IP address from the host ID portion of the IP address.
The network administrator creates a 32-bit subnet mask composed of 1s and 0s.
The 1s in the subnet mask represent the positions that refer to the network or subnet
addresses.
The Network Security Configuration feature lets apps customize their network security
settings in a safe, declarative configuration file without modifying app code. These settings
can be configured for specific domains and for a specific app.
How to Set Up a Secure Network: Back to Basics
1. Step One: Locate and Open Up Your Router Settings Page.
2. Step Two: Create a Password for Your Router.
3. Step Three: Change the Name of Your Network's SSID.
4.2. Configure security

Version -1
Page 61 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
4. Step Four: Enable Network Encryption.
5. Step Five: Filter Out Your Mac Addresses.
6. Step Six: Reduce Your Wireless Signal's Range.
8 ways to improve wired network security
1. Perform auditing and mapping.
2. Keep the network up-to-date.
3. Physically secure the network.
4. Consider MAC address filtering.
5. Implement VLANs to segregate traffic.
6. Use 802.1X for authentication.
7. Use VPNs to encrypt select PCs or servers.
8. Encrypt the entire network.
Devices needed to be secured
These devices include routers, firewalls, switches, servers, load-balancers, intrusion detection
systems, domain name systems, and storage area networks. These devices are ideal targets for
malicious cyber actors because most or all organizational and customer traffic must pass
through them.
Start first with establishing neutral posture in the chair with your feet on the floor or footrest.
Then progress to keyboard and mouse placement (keyboard tray), followed by desk height
adjustment as able, then monitor height, and lastly, organize everything else within easy
reach. Good ergonomics takes practice.
A good workstation ergonomic arrangement will allow any computer user to work in a
neutral, relaxed, posture that will minimize the risk of developing any injury. An ideal
keyboard arrangement is to place this on a height-adjustable negative-tilt tray.
Workstation management also involves Maintaining and monitoring them to ensure they are
running efficiently. It's hard to monitor machines that are remote so there is a number of
agents out there you can install to allow you to both manage and monitor machines both
inside and outside your network.
How do you manage a workstation?
Workstation management also involves Maintaining and monitoring them to ensure they are
running efficiently. It's hard to monitor machines that are remote so there is a number of
agents out there you can install to allow you to both manage and monitor machines both
inside and outside your network.
How do you position your body at a computer workstation?
Hands, wrists, and forearms are straight, in-line and roughly parallel to the floor. Head is
level, forward facing, and balanced. Generally it is in-line with the torso. Shoulders are
relaxed and upper arms hang normally at the side of the body.
4.3. Configure workstation

Version -1
Page 62 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Why it is important to have a workstation set up ergonomically?
What aspects of your workspace can you make ergonomic? If you spend a lot of time sitting
at your desk, it can wreak havoc on your body - even if the effects aren't immediately
noticeable. Over time, a poor setup can mean pinched nerves, sore wrists, and other
discomforts.
How do I make my computer workstation fit me?
The lower part of the backrest should support the curve of your lower back. The lower part of
the backrest (the lumbar support) of your chair should support the curve of your lower
back. If your backrest is adjustable, raise or lower it so the lumbar support fits snugly against
your lower back.

Version -1
Page 63 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Self check-4
Name: _____________________________ IDNo_________ Date: ___________________
Time started: ____________ Time finished:
________________
Instruction:-Choose the correct answer from the given alternatives and write your own
choice.
1. If the break in a cable or fault computer can bring slow down entire
network_____________ type of topology.
A. Mesh topology C. Bus topology
B. Ring topology D. Hybrid topology
2. From the following comparison one is can explain Personal Area Network?
A. Low cost little or No infrastructure setup.
B. Short range communication.
C. Small personal network , use anywhere.
D. All are answers
3. Which one of the following network topology is fault tolerant?
A. Mesh topology C. Ring topology
B. Bus topology D. Hybrid topology
4. ___________ refers physical arrangement or layout of the computer network devices
& cables?
A. Topology C. Server
B. Network D. All
5. From the following one is an advantage of client-server based Network?
A. Centralized C. Accessibility
B. Scalability D. All
1. ___________ usually used to strengthen signals going long distances.
A. Switch B. Repeater C. HUB D. None
2. A device that is used to connect to the Internet and changes digital data to analog
signal.
A. Modem B. Digital camera C. NIC D. All
3. From the following alternatives one is an advantage client-server based network.
A. Centralized

Version -1
Page 64 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
B. Scalability
C. Flexibility
D. All are answers
Part II. Write “True” if the given question is correct and say “False” if it is incorrect.
4. A good workstation ergonomic arrangement is important for our health & minimize
the risk of developing any injury.
5. Hub broadcasts data to every computer or Ethernet-based device connected to it.
Part III. Match the following their correct answers column A with B
Column A Column B
6. Wide Area Network A. has equivalent capacity
7. Server B. Fault tolerant topology
8. Mesh topology C. Internet
9. peer-to-peer D. Hybrid topology
10. combination of any two or more network E. dedicated computer that
provide recourses

Version -1
Page 65 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Operation sheet 3
How to Create Subnets
To create a subnet follows these steps:
1. Determine the number of required network IDs:
One for each subnet
One for each wide area network connection
2. Determine the number of required host IDs per subnet:
One for each TCP/IP host
One for each router interface
3. Based on the above requirements, create the following:
One subnet mask for your entire network
A unique subnet ID for each physical segment
A range of host IDs for each subnet
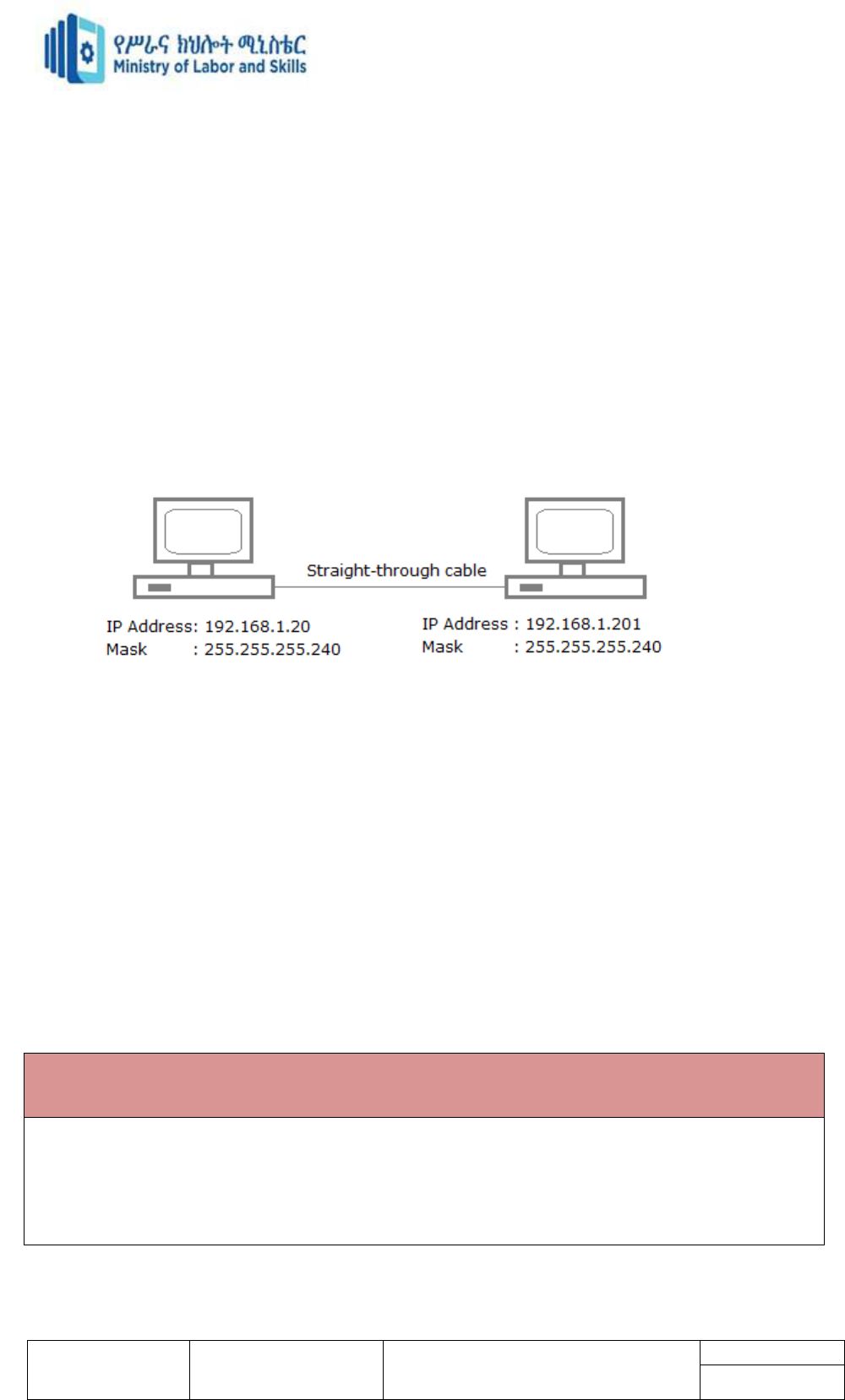
Version -1
Page 66 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Lap test 4
Name: _____________________________ IDNo_________ Date: ___________________
Time started: ____________ Time finished:
________________
Part I. Instruction:-Answer the following questions from number 1-3 and choose the
correct one.
1. A network administrator is connecting hosts A and B directly through their Ethernet
interfaces, as shown in the illustration. Ping attempts between the hosts are
unsuccessful. What can be done to provide connectivity between the hosts?
1. A crossover cable should be used in place of the straight-through cable.
2. A rollover cable should be used in place of the straight-through cable.
3. The subnet masks should be set to 255.255.255.192.
4. A default gateway needs to be set on each host.
5. The subnet masks should be set to 255.255.255.0.
A. 1 only
B. 2 only
C. 3 and 4 only
D. 1 and 5 only
E. 2 and 5 only
Unit Five:- Administer and support peripheral services
This unit is developed to provide you the necessary information regarding the following content
coverage and topics:-
Indentify priority
Configure network maintenance schedule settings
Version -1
Page 67 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Priority is defined as that something or someone is more urgent or important than other
things. An example of priority is a claim that has to be processed right away and that jumps
to the head of the line.
After establishing the physical or wireless connections of the computers, you can
electronically connect them, test or check that they can "see" each other. Microsoft Windows
7 or 10 makes networking ridiculously easy.
Demonstrate peripheral supporting methods
This guide will also assist you to attain the learning outcomes stated in the cover page.
Specifically, upon completion of this learning guide, you will be able to:
Explain and identifying priority
Identify network configuring setting
Demonstrating peripheral supporting methods
5.1. Indentify priority
Version -1
Page 68 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Prioritize your technology initiatives and opportunities against value and cost drivers to
align around a more effective roadmap.
How do you prioritize client issues?
Best Practices for Prioritizing Customer Requests
1. First come, first serve.
2. Allow customers to determine the level of urgency.
3. Create categories for types of requests.
4. Create categories for types of customers.
5. Respond quickly, no matter what.
6. Streamline your reassign process.
7. Create service level agreements (SLA's).
Maintenance schedules allow you to temporarily disable monitoring on specific
resources (such as data backups and service restarts) so you can perform maintenance
on the host machines. When the scheduled maintenance is
completed, ipMonitor reactivates the affected monitors. This process ensures that your
planned maintenance activities do not trigger alerts or negative results in your historic
reports.
You can schedule maintenance based on rules (such as Microsoft Outlook rules) or
while ipMonitor performs routine actions. This allows you to define a list of actions
using the reboot server, restart service, or pause commands. You can configure
credentials as required on a per-action basis, as well as schedule maintenance to
disable monitors while actions outside of ipMonitor occur.
Maintenance Objectives
Describe network maintenance tasks
Explain the difference between proactive and reactive network maintenance.
Describe well-known network maintenance models.
Identify common maintenance procedures.
Describe tools required for network maintenance.
Maintenance Tasks
Device installation and maintenance: Includes tasks such as installing
devices and software and creating and backing up configurations and software.
Failure response: Includes tasks such as supporting users that experience
network problems, troubleshooting device or link failures, replacing
equipment, and restoring backups.
Network performance: Includes tasks such as capacity planning,
performance tuning, and usage monitoring.
Business procedures: Includes tasks such as documenting, compliance
auditing, and service level agreement (SLA) management.
5.2. Configure network maintenance schedule settings

Version -1
Page 69 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Security: Includes tasks such as following and implementing security
procedures and security.
What is a Network Maintenance Plan?
A network maintenance plan is the range of services a company intends to use to keep the network
running smoothly. That plan may include tasks performed by internal resources as well as those that
are easier to team up with network hardware support experts to complete.
Maintaining your computer network is important because there are many factors that can go
wrong on a daily basis. Regular maintenance can keep the big problems away, while helping
to maintain your networks optimal performance.
The your networked computers should maintained regularly within 24 hours or in weeks.
You must build processes and procedures for performing your network maintenance tasks; this is
called network maintenance planning.
Network maintenance planning includes the following:
1. Scheduling maintenance
2. Formalizing change-control procedures
3. Establishing network documentation procedures
4. Establishing effective communication
5. Defining templates/procedures/conventions standardization.
6. Disaster Recovery.
Scheduled Maintenance
The benefits of scheduled maintenance include the following:
Network downtime is reduced.
Long-term maintenance tasks will not be neglected or forgotten.
Predictable lead times for change requests.
Disruptive maintenance tasks can be scheduled during assigned maintenance
windows, reducing downtime during production hours.
During maintenance periods, ITS will be performing the following types of
maintenance:
File server maintenance.
Email and antivirus maintenance.
Firmware updates and directory maintenance on the Email and file servers.
Switch and router firmware/software maintenance.
Dorm-Net and Network Security Systems maintenance.
Things to Maintain and Repair Computer System and Networks
1. Back up your data.
2. Clean dust from your computer.
3. Clean up your cabling and everything else too.
4. Organize your installation disks.

Version -1
Page 70 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
5. Run antivirus and spyware and scans regularly.
6. Clean up your software.
7. Clean up your OS.
What is the importance of maintenance planning and scheduling?
The basic goal of planning and scheduling is avoiding delay.
The role of the Maintenance Planner is to improve work force productivity and work
quality by anticipating and eliminating potential delays through planning and
coordination of labor, parts and material, and equipment access.
Usage logs
Every activity within a network is considered a security event. Emails, firewall updates, and
user activity are all recorded in a complex series of logs that define your network's
environment. The resulting data logs contain a huge amount of information that would make
threats impossible to detect with the human eye.
A peripheral device provides input/output (I/O) functions for a computer and serves as an
auxiliary computer device without computing-intensive functionality.
A peripheral activity or issue is one which is not very important compared with other
activities or issues. A peripheral or peripheral device is an auxiliary device used to put
information into and get information out of a computer.
There are many other examples of peripherals, such as a microphone, web camera,
headphones, external hard drive and flash drive. Most computer users have at least several of
these peripheral devices.
5.3. Demonstrate peripheral supporting methods

Version -1
Page 71 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Self check test 5.
Name _________________________ IDNo _____________ Level _____________
Start time _____________ Finishing time _____________
Instruction:- Write short answer for the given questions below.
1. What is maintenance schedule?
_______________________________________________________________
_______________________________________________________________
_______________________________________________________________
_______________________________________________________________
_______________________________________________________________
_______________________________________________________________

Version -1
Page 72 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
_______________________________________________________________
____________________
2. Write and discuss importance maintenance scheduling
_______________________________________________________________
_______________________________________________________________
_______________________________________________________________
_______________________________________________________________
_______________________________________________________________
______________
Instruction:
Instruction: Say True or False
3. Maintenance Scheduling procedures are for Maintenance use only.
4. Mechanics availability for work must be documented and used by scheduler.
5. A Prioritization system that correctly identifies jobs that can be planned from
rush jobs is key to a proactive maintenance program.
6. The best priority system is one developed, controlled and executed by the
Maintenance Organization.
Instruction: Choice Part
7. The Best process for distributing Maintenance Work Schedules is:
A. Job start and completion are assigned to crew and published more
than 3 days prior to starting work.
B. Schedules of job start, completion and crew assignments are
distributed the day before starting the work.
C. Schedules of job start, completion and crew assignments are
distributed the day to do the work.
D. Job assignments are given out to crews 1 -2 days prior to starting
work or the day to do the work.
8. Schedule performance is measured and reported until it exceeds 90%.
A. True.
B. False
9. Schedule breakers and reactive work are managed by and responsibility of:
A. Planner and Scheduler
B. Operations and Maintenance Manager
C. Production and Maintenance Supervisors
D. Mechanics and Operators
10.Maintenance and Production schedules should be combined into an
integrated shop floor schedule to eliminate confusion on priorities,
equipment out of service and work flow patterns.
A. True
B. False

Version -1
Page 73 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Operation sheet 4
Here is a simple list to go over once per month to keep your equipment running at peak
performance.
Be sure to always backup your data. This is one of the most crucial rules in the IT industry.
Loss of company and customer data is a serious issue that can be easily prevented. Being
proactive with backups will give you peace of mind, as well as protect your data from
numerous possible threats.
1. Regularly scheduled, automated backups are a great resource to utilize. You can
schedule them daily, weekly, or monthly, depending on the amount of critical data
being stored. It is also strongly suggested that you store backups in a remote location
in addition to the local network. Having a second secure location is beneficial in times
of data corruption and hardware failure.
2. Keep software and plug-in up-to-date. Always look for new versions of any critical
software and plug-in. Updated versions may have patches for functionality and
security. It is best to then delete the ones you do not need. Any miscellaneous and
extra plugins will likely slow down your machines.
Version -1
Page 74 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
3. Remove server clutter. It is a good idea to look at your server’s RAM, CPU, and
disk storage to be sure you are keeping only the essentials. If you are nearing peak
capacity, it may be time to upgrade your server.
4. Consolidate content. While you are inspecting your resources, you may want to
consolidate and archive any old content. Any databases, files, and scripts that are no
longer useful or necessary are only taking up space and bogging down your server.
5. Change passwords regularly. Anyone using your server should be changing
passwords frequently. Having strong password requirements helps to protect your
company network from intrusions.
6. Keep your equipment and equipment area clean. Dust and dirt can wreak havoc on
the components of IT equipment; be sure to keep areas clean. Maintaining proper
temperatures and spacing is also crucial to decrease the risks of overheating and
downtime.
7. Have security measures in place. Firewall and other security measures can help to
protect company and customer data, as well as prevent security threats that bog down
your system.
Lap test 4
Name _____________________________ IDNo __________ Level __________
Start time __________________________ Finishing time ___________________
1. Write maintenance schedule in the check list below.
Instruction: Your teacher will evaluate your output either satisfactory or unsatisfactory. If
unsatisfactory, your teacher shall advice you on additional work. But if satisfactory, you can
proceed to the next topic.
Personal name _________________________ Date of issued
____________
No
Maintenance
description
component
description
Daily
Weekly
Monthly
Annually
Remark
1.
Data backups
2.
Virus protection
3.
Network
documentation
updates
Version -1
Page 75 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
4.
Device inventory
5.
Power checks
6.
Device filter
dusting
7.
Cable organization
8.
Check security
9.
Keep you
equipment is clean
Unit Six:- Use command line tools
This learning guide is developed to provide you the necessary information regarding the
following content coverage and topics
Indentify command-line environment
Differentiate command-line and graphical user interface
Apply command-line tools
This guide will also assist you to attain the learning outcomes stated in the cover page.
Specifically, upon completion of this learning guide, you will be able to:
Indentifying command line environment according to organizational guidelines
Explain Differentiate command-line and graphical user interface
Explain how to know command-line tools

Version -1
Page 76 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
What is command-line environment?
The environment of the command line refers to the settings and preferences of the current
user. It enables users to set greetings, alias commands, variables, and much more.
To check if an environment variable Exists:-
Select Start > All Programs > Accessories > Command Prompt. In the command window that
opens, enter echo %VARIABLE%. Replace VARIABLE with the name of the environment
variable.
A command-line interpreter or command-line processor uses a command-line interface to
receive commands from a user in the form of lines of text. This provides a means of setting
parameters for the environment, invoking executables and providing information to them as
to what actions they are to perform.
The command line, also called the Windows command line, command screen, or text
interface, is a user interface that's navigated by typing commands at prompts, instead of using
a mouse. For example, the Windows folder in a Windows command line is "C:\Windows>"
(as shown in the picture).
A Command line is a horizontal line on an interface that allows the user to type in various
commands. Typically, there is a command prompt at the left side of a screen, with a blank
line extending to the right where commands are typed.
6.1. Indentify command-line environment
Version -1
Page 77 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
What is command line and types?
A command-line interface (CLI) is a text-based user interface (UI) used to run programs,
manage computer files and interact with the computer. Command-line interfaces are also
called command-line user interfaces, console user interfaces and character user interfaces.
How to use command prompt/ Using command-line tools?
Right-click a Command Prompt shortcut.
Click Run As Administrator. When you open the Command Prompt window as
Administrator, an operating-system dialog appears that asks you if you want to continue.
Click Continue to proceed.
When you run these command-line tools from a Command Prompt, run them from a
Command Prompt window that is launched by performing the following actions: Right-click
a Command Prompt shortcut. Click Run As Administrator.
Version -1
Page 78 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
The main difference between GUI and CLI is that the Graphical User Interface (GUI) allows
the user to interact with the system using graphical elements such as windows, icons, menus
while the Command Line Interface (CLI) allows the user to interact with the system using
commands.
An operating system is an interface between the user and the hardware components. It
performs different tasks. An operating system provides GUI or CLI for the user to perform
tasks. Some operating systems only provide CLI while others provide both GUI and CLI. A
GUI consists of controls or widgets to interact with the computer. On the other hand, when
using the CLI, the user should enter commands to perform the tasks. Overall, GUI is more
user-friendly, but the execution speed is higher in CLI.
What is GUI
GUI stands for Graphical User Interface. It takes the advantage of computer graphics. It
allows the user to interact with the computer using components such as windows, icons,
labels, text boxes, and radio buttons. It is easy for the user to perform tasks using GUI as it
6.2. The Difference between Command-line and graphical user
interface.
Version -1
Page 79 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
does not require remembering commands. He can easily click on icons, drag and drop objects
using the mouse.
There are various GUI components. The window is the complete visible screen to the user. It
has a rectangular shape and it can overlap with the area of other windows. A text box is a
component for the user to enter input data. A menu provides a list of options for the user to
select an option. A button allows selecting one particular option. A radio button appears as a
group and the user can select one option at a time. Moreover, checkbox is a graphical element
that allows the user to select an option out of multiple alternatives.
Operating Systems such as Windows and Linux provide GUI. They contain windows, icons,
search boxes, menus, drop down lists and many graphical elements. There is also application
software designed for specific business requirements such as Human Resource Management
systems, Library Management Systems, etc. They consist of GUIs to accomplish necessary
tasks. Overall, a GUI is a user-friendly mechanism to interact with the system.
A GUI is a type of user interface that allows users to interact with electronic devices through
graphical icons and visual indicators.
What is CLI
CLI stands for Command Line Interface. CLI is also called Command Language
Interpreter, Console User Interface or Character User Interface. It allows the users to
enter commands to the terminal to perform the task. When the user enters a command and
presses “enter” key, the terminal or the shell will interpret that command and will display the
response back to the terminal. Likewise, the user can communicate with the operating system.
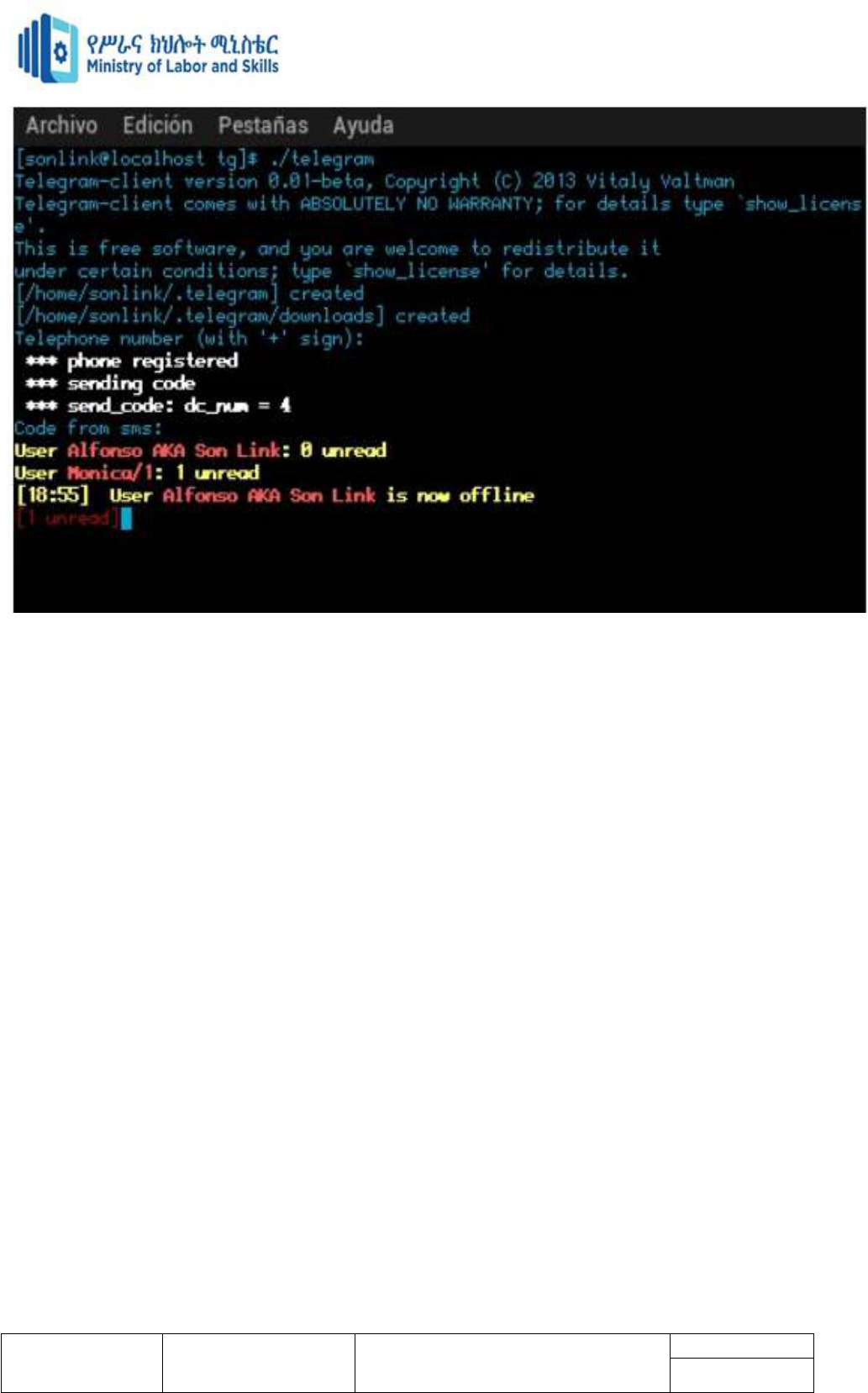
Version -1
Page 80 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
A CLI is an interface for the user to issue commands in the form of successive lines of text or
command lines to perform the tasks.
Usability
It is easy to use the GUI. It is not necessary to have a vast knowledge to operate the system
using the GUI. Even a beginner can easily handle the tasks using the GUI. On the other hand,
CLI is complex. The user should have good knowledge of the commands. Miss pelt
commands are of no use.
Memory Requirement
GUI requires more memory as it contains a lot of graphical components. CLI is a command
interface, and it does not require more memory.
Speed
GUI is slower but the CLI is fast.
Customizability
The user can change the appearance of the GUI. There are customizable options to change the
appearance. It is not possible to change the CLI.
Flexibility
GUI is more flexible whereas CLI is not much flexible.

Version -1
Page 81 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Command line tools are scripts, programs, and libraries that have been created with a unique
purpose, typically to solve a problem that the creator of that particular tool had himself.
Because of that, we have divided this roundup of the best command line tools to include
different categories, like Web Development, Utilities, Productivity, and others. Beyond being
categorized, note that the following 50 command line tools are listed in no particular order —
they’re not ranked or rated, but are numbered simply to make a list easier to navigate.
Windows Command-line Tools
PowerShell
ConEmu
PSReadLine
Chocolatey
Babun (optional)
A. PowerShell
Significantly closer to a real 'shell' than cmd.exe, offering us a powerful scripting
environment for task automation. It's fair to compare it to Bash or zsh.
Auto completes directory and filenames
Auto completes application names
Has integrated aliases and commands (called cmdlets - e.g Select-String is like grep, Invoke-
Elevated is like sudo, Sort-Object is like sort, Get-Process lists all active processes). If
moving from another shell to PS, Set-Alias lets you map aliases you're used to to Windows
equivalents. For example: Set-Alias server python -m http.server 8000 launches a Python
server when the server alias is used.
Aliases can be persisted in a PowerShell profile
Supports piping, like Unix. Unlike Unix, it pipes objects rather than text streams. This
requires getting used to but avoids reparsing when you want to get out a property.
Supports modules. PSGet is a package manager for PowerShell allowing you to easily extend
it.
Optionally consider Posh-Git, a PowerShell script for git to gain contextual tab-completion.
If you're interested in trivia, here's an answer to why MS created PowerShell from the
lead architect.
6.3. Apply Command-line tools
Version -1
Page 82 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
B. ConEmu(console host)
An advanced console emulator where you can run your shell of choice.
Supports opening multiple terminals in different tabs. Makes it trivial to launch terminals as
different users.
Extremely customizable - everything from shortcuts to text selection and status bar colors can
be changed.
Supports a split-screen view
Simple GUI apps can be run in tabs
Support for Windows 7+ Jump Lists
Supports smooth window resizing
Windows font anti-aliasing
Starting tabs can be fully customized to start in a particular directory
Intelligent copy/paste
Version -1
Page 83 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
C. PSReadLine (console editing helpers)
Significantly improves the console editing experience
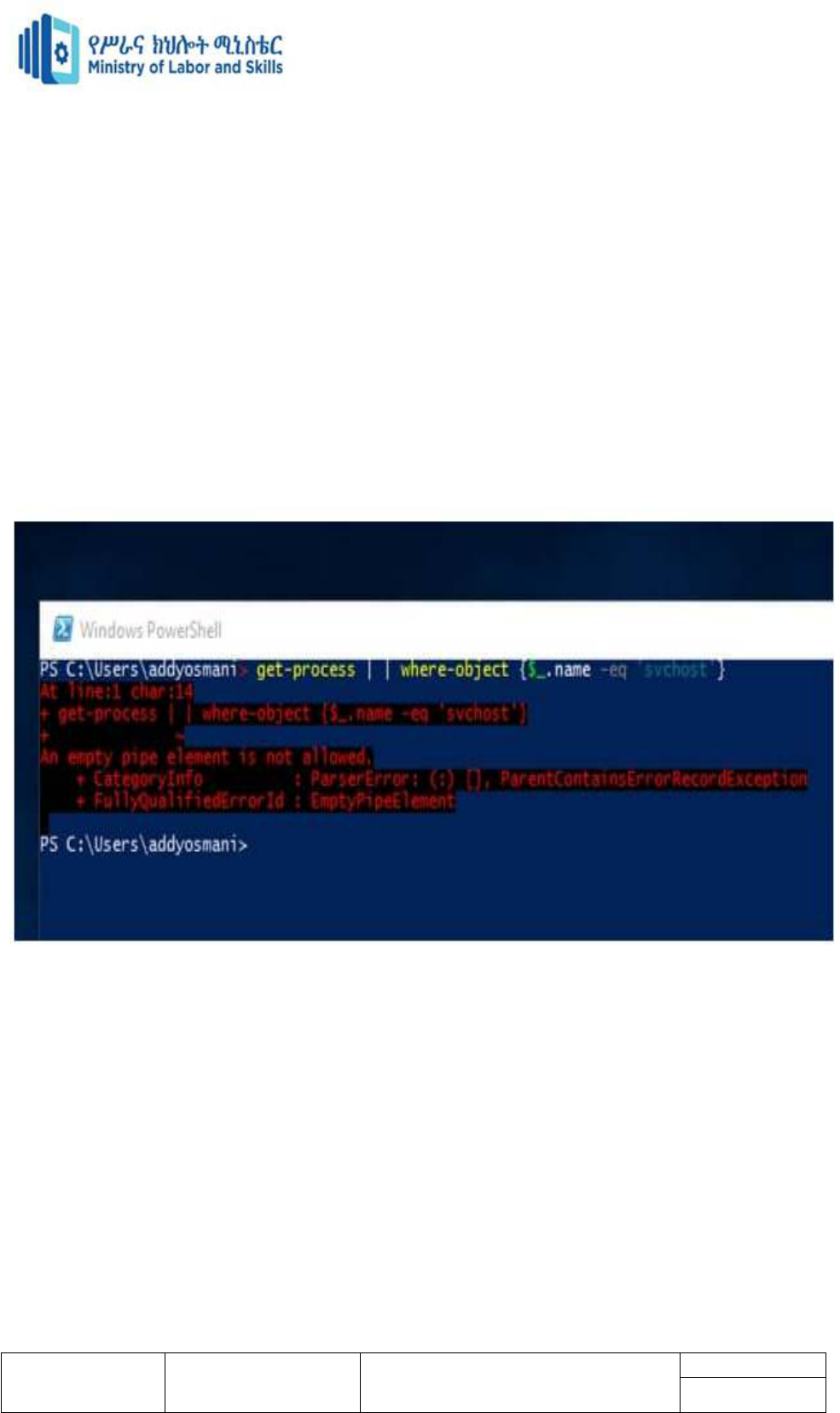
Version -1
Page 84 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Syntax highlighting whenever you start typing commands. Clearly indicates syntax errors
with a red ">" character.
Highly customizable key bindings
D. Bash-style autocompletion
Bash/zsh interactive history search (Ctrl + R). Powerful command history traversal too.
Easily view previous multi-line commands using arrow keys rather than just the last line of
the command.
Proper support for copy/paste/cut (Ctrl+C/X/V should all work just fine)
Good support for undo/redo
History saving is automatic
E. Chocolatey (package manager)
Basically homebrew for Windows, allowing you to pull in your favorite Windows apps
conveniently. There are currently ~3K packages available that can be updated using
Chocolatey directly.
Differs from Nuget. NuGet is for development libraries. Chocolatey is a binary machine
package manager and is built on NuGet infrastructure.
Offers effectively silent builds
You may also be interested in learning about OneGet, Microsoft's package
manager..manager, which should work with Chocolatey under Windows 10.
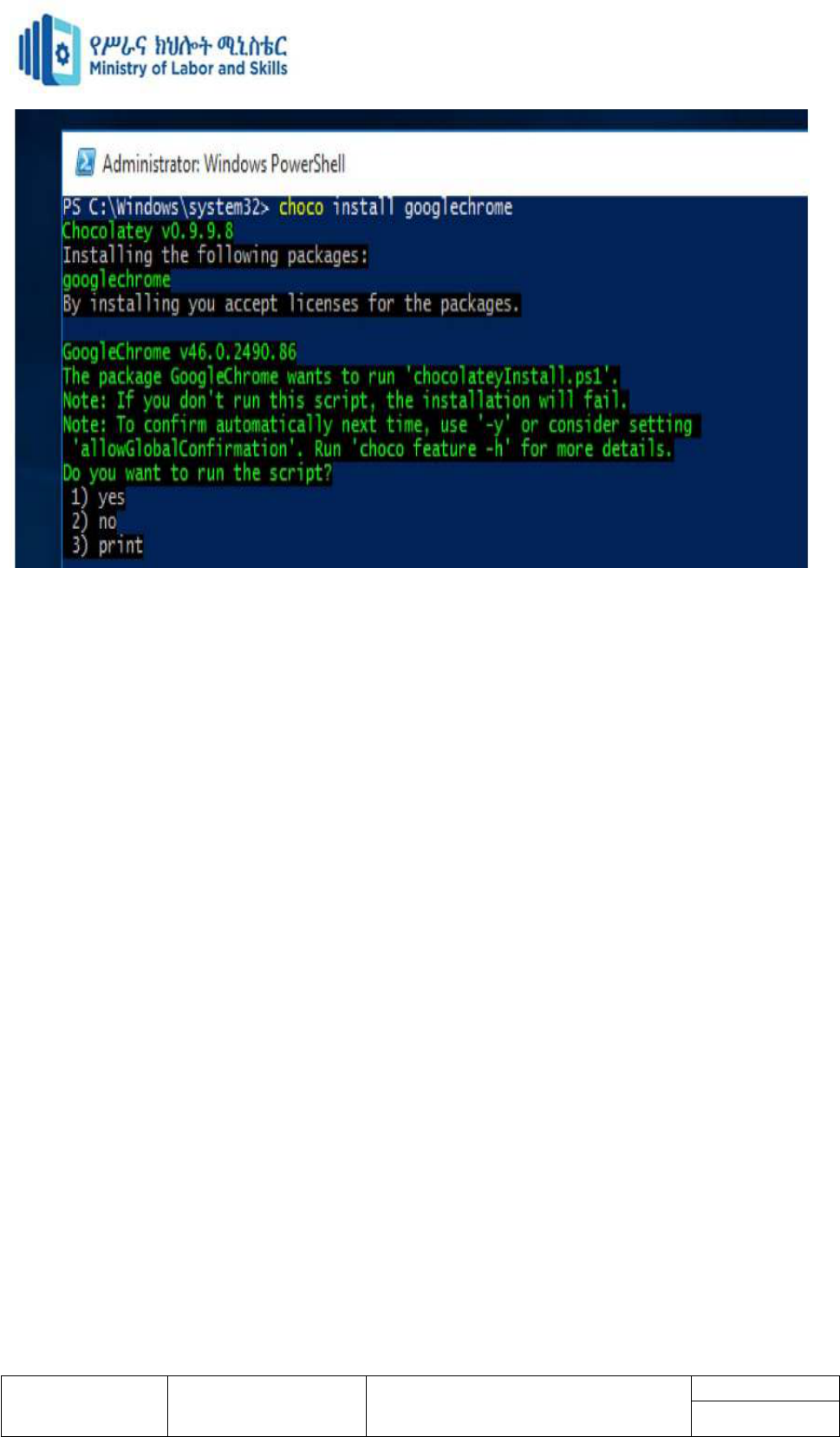
Version -1
Page 85 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
F. Babun (optional/ Cygwin preconfigured)
Cygwin (the Linux-like env for Windows) minus some of the historically known quirks. The
overall setup is significantly more straight-forward using the Babun installer. If you're
particularly experienced with Unix and would prefer to avoid learning PowerShell,
cygwin/Babun are worth considering.
Includes a package manager called pact (a little similar to brew) similar to apt-get. This is a
big deal as you currently have to re-run the Cygwin installer when adding packages vs. just
using pact.
Vim pre-installed and pre-configured
Integrated support for oh-my-zsh
Auto-updates
Self check 6.

Version -1
Page 86 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Name _______________________________________ IDNo _____________ Level
________________
Start time ____________________ Finish _____________________
Instruction:-Say true of False
1. A command-line interface is a text-based user interface used to run programs, manage
computer files and interact with the computer.
2. GUI allows the user to interact with the computer using components
3. CLI requires more memory as it contains a lot of graphical components and GUI is a
command interface, and it does not require more memory.
4. CLI is faster than but GUI requires more memory.
5. It is not possible to change the CLI that User to change the appearance
Instruction: Match the following a given columns
Column A Column B
6. CLI A. Slow
7. GUI B. Highly customizable key bindings
8. Simple GUI apps can be run in tabs C. Good support for undo/redo
9. Bash-style auto completion. D. ConEmu(console host)
10. PSReadLine (console editing helpers) E. Fast
Unit Seven: Maintain peripherals and fix common problems
Version -1
Page 87 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
How to Maintain
Computer Peripherals
PC hardware maintenance is the process of auditing, upgrading, and maintaining a computer's
physical parts to ensure the components perform optimally. IT hardware maintenance
involves caring for components such as the keyboard, CD drives, hard disk, battery, and other
peripherals. Hardware maintenance and support services are preventive and remedial services
This Unit is developed to provide you the necessary information regarding the following
content coverage and topics
Identify regular maintenance schedule
Replace consumables
Identify peripheral failures
This guide will also assist you to attain the learning outcome stated in the cover page.
Specifically, upon completion of this Learning Guide, you will be able to
Identify regular maintenance schedule according to guidelines
Identify replacing consumables
Identify command-line tools
Identify peripheral failures
7.1. Identify regular maintenance schedule

Version -1
Page 88 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
that physically repair or optimize hardware, including contract maintenance and per-incident
repair.
Computer hardware maintenance involves taking care of the computer's physical
components, such as its keyboard, hard drive and internal CD or DVD drives. Cleaning the
computer, keeping its fans free from dust, and defragmenting its hard drives regularly are all
parts of a computer hardware maintenance program.
Update your firmware every 6 months.
Keep your devices clean daily in 24 hours.
Follow recommended maintenance schedules weekly or monthly.
Adhere to the manufacturer's best practices.
Use the recommended settings.
Use the media recommended by the manufacturer.
Keep device media in a well protected area.
What is peripheral maintenance?
This activity entails the repair and maintenance of all types of computers and peripheral
equipment (printers, displays, keyboards, modems, scanners, smart card readers, computer
projectors etc.)
How do you clean computer parts and peripherals?
Use an anti-static cloth to lightly dust your computer casing. Do not use furniture cleaners or
strong solvents. Use a can of compressed air to blow out debris from the air intake slots.
Ammonia diluted with water—or glass cleaner comprised mostly of ammonia and water—is
a safe cleaning solution for computer surfaces.
What is the first step to performing hardware maintenance?
What is the first step to performing hardware maintenance? Turn off the computer and
remove its power source. All-in-one computers are easier to service and upgrade but occupy
more space than desktop computers.
Why do we maintain computer hardware?
Keeping computers well maintained can prevent viruses and malware, and keep your
computer in good working order. Regular maintenance ensures that your antivirus software is
kept up to date and working properly. Nothing could be more annoying than a computer
running too slowly.
Types of maintenance
Predictive.
7.2. Replace consumables

Version -1
Page 89 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Preventive.
Corrective.
Predictive
Predictive maintenance (PdM) is a type of condition-based maintenance that monitors the
condition of assets through sensor devices. These sensor devices supply data in real-time,
which is then used to predict when the asset will require maintenance and thus, prevent
equipment failure.
Predictive maintenance techniques are designed to help determine the condition of in-service
equipment in order to estimate when maintenance should be performed. This approach
promises cost savings over routine or time-based preventive maintenance, because tasks are
performed only when warranted.
Predictive maintenance refers to maintenance based on the actual condition of a component.
Maintenance is not performed according to fixed preventive schedules but rather when
certain changes in characteristics are noted. A useful analogy can be made with automobile
oil changes.
What is an example of predictive maintenance?
Some examples of using predictive maintenance and predictive maintenance sensors
include vibration analysis, oil analysis, thermal imaging, and equipment observation.
What is required for predictive maintenance?
Some of the main components that are necessary for implementing predictive maintenance
are data collection and preprocessing, early fault detection, fault detection, time to failure
prediction, maintenance scheduling and resource optimization.
Predictive Maintenance allows for safety compliance, preemptive corrective actions, and
increased asset life. By looking ahead, and knowing what failure is likely to occur when, pre-
emptive investigations, maintenance schedule adjustments, and repairs can be performed
before the asset fails.
What is advantage and disadvantage of predictive maintenance?
Predictive maintenance presents you with the best time to work on an asset so
that maintenance frequency is minimal and reliability is as high as possible while eliminating
unnecessary costs.
However, there are few disadvantages to predictive maintenance is
High start-up costs and the need for specialized personnel.
Preventive
In preventive maintenance, equipment is repaired and serviced before failures occur. The
frequency of maintenance activities is pre-determined by schedules. Preventive maintenance

Version -1
Page 90 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
aims to eliminate unnecessary inspection and maintenance tasks, to implement additional
maintenance tasks when and where needed and to focus efforts on the most critical items.
The higher the failure consequences, the greater the level of preventive maintenance that is
justified.This ultimately implies a trade-off between the cost of performing preventive
maintenance and the cost to run the equipment to failure.
Inspection assumes a crucial role in preventive maintenance strategies. Components are
essentially inspected for corrosion and other damage at planned intervals, in order to identify
corrective action before failures actually occur. Preventive maintenance performed at regular
intervals will usually results in reduced failure rates. As significant costs are involved in
performing preventive maintenance, especially in terms of scheduled downtime, good
planning is vital.
Corrective maintenance
Corrective maintenance refers to action only taken when a system or component failure has
occurred. It is thus a retro-active strategy. The task of the maintenance team in this scenario is
usually to effect repairs as soon as possible. Costs associated with corrective maintenance
include repair costs (replacement components, labor, and consumables), lost production and
lost sales. To minimize the effects of lost production and speed up repairs, actions such as
increasing the size of maintenance teams, the use of back-up systems and implementation of
emergency procedures can be considered. Unfortunately, such measures are relatively costly
and/or only effective in the short-term.
Common problems with PC hardware peripherals and how to fix them?
Hardware Fault means any fault, issue or matter relating to any Supported
Equipment excluding. Hardware Fault means a Hardware fault arising solely or primarily
from the failure of a physical component of the Hardware but excluding any arising from any
Application Fault or any Firewall Downtime.
Some of the most common PC hardware problems that need troubleshooting are:
Your computer won't turn on.
Your computer turns on, but still doesn't work.
Your computer screen freezes.
Your computer has insufficient memory.
You get a CMOS error.
Your operating system is missing or your hard drive isn't detected.
Most Common Computer Problems
The Computer Won't Start. A computer that suddenly shuts off or has difficulty starting up
could have a failing power supply.
7.3. Identify peripheral failures

Version -1
Page 91 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
The Screen is Blank.
Abnormally Functioning Operating System or Software. ...
Windows Won't Boot.
The Screen is frozen.
Computer is Slow.
Strange Noises.
Slow Internet.
How do I fix malfunctioning hardware?
Use the device troubleshooter to diagnose and resolve the issue.
Open Settings.
Click on Update & Security.
Click on Troubleshoot.
Select the Troubleshoot that matches the hardware with the problem. ...
Click the Run the troubleshooter button.
What causes a hardware failure?
Harsh environmental conditions such as extreme temperatures can damage hardware
components. Unregulated power supply of any sort can damage hardware components. This
includes power surges from the regular power line or from lightning.
What a Solutions to fix this problems:
Check the power supply.
Make sure the monitor or display is functional.
Eliminate external hardware.
Reinstall system.
Restart the modem.
Fix your Wi-Fi signal.
Kill any unwanted background software.
Contact your ISP.
Version -1
Page 92 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Self check test-7
Name __________________________ IDNo______________ Level _______________
Start time_____________ Finish time ___________________
Instruction:-Read the given questions below and write your own answers on time.
I. Match column A with column B
A B
1. Corrective maintenance A. make to keep equipment failures
2. Preventive maintenance B. Condition based maintenance
3. Predictive maintenance C. Carried out to correct failure
D. prevent unauthorized use
II. Choice
4. From the following given alternatives one is a method of to fix malfunctioning of
hardware.
A. Use the device troubleshooter to diagnose and resolve the issue, Open
Settings.
B. Click on Update & Security, Click on Troubleshoot
C. Click the Run the troubleshooter button
D. All are answers
5. From the following One is disadvantages of predictive maintenance.
Version -1
Page 93 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
A. Reliability
B. Condition-based maintaining activity
C. High start-up costs
D. Eliminating unnecessary costs
III. Say True or False
6. Maintaining hardware peripherals regularly is not important for hardware life.F
7. Turning off the computer and remove its power source is fundamental step or process.T
8. Preventive maintenance is cost and time effective maintenance.T
9. Predictive is not performed according to fixed preventive schedules but rather when
certain changes in characteristics are noted.T
10. Unkind environmental conditions such as extreme temperatures can damage hardware
components.T
Unit Eight:-Use and maximize operating system
This Unit is developed to provide you the necessary information regarding the following
content coverage and topics
Identify Configured Operating system
Explain Install and upgrade application software
Identify Use graphical user interface and command-line interface
Use third-party operating system utilities
This guide will also assist you to attain the learning outcome stated in the cover page.
Specifically, upon completion of this Learning Guide, you will be able to
Types of peripheral devices
Identifying peripheral devices
Obtaining and storing peripheral devices

Version -1
Page 94 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
What is an operating system?
An operating system (OS) is the program that, after being initially loaded into the computer
by a boot program, manages all of the other application programs in a computer. The
application programs make use of the operating system by making requests for services
through a defined application program interface (API). In addition, users can interact directly
with the operating system through a user interface, such as a command-line interface (CLI) or
a graphical UI (GUI).
Why use an operating system?
The operating system (OS) manages all of the software and hardware on the computer. It
performs basic tasks such as file, memory and process management, handling input and
output, and controlling peripheral devices such as disk drives and printers.
An operating system brings powerful benefits to computer software and software
development. Without an operating system, every application would need to include its own
UI, as well as the comprehensive code needed to handle all low-level functionality of the
underlying computer, such as disk storage, network interfaces and so on. Considering the vast
array of underlying hardware available, this would vastly bloat the size of every application
and make software development impractical.
Operating system types and examples
Although the fundamental roles of an operating system are ubiquitous, there are countless
operating systems that serve a wide range of hardware and user needs.
8.1.Identify Configured Operating system

Version -1
Page 95 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
General-purpose operating system.
A general-purpose OS represents an array of operating systems intended to run a multitude of
applications on a broad selection of hardware, enabling a user to run one or more applications
or tasks simultaneously. A general-purpose OS can be installed on many different desktop
and laptop models and run applications from accounting systems to databases to web
browsers to games. General-purpose operating systems typically focus on process (thread)
and hardware management to ensure that applications can reliably share the wide range of
computing hardware present.
Common desktop operating systems include the following:
Windows is Microsoft's flagship operating system, the de facto standard for home and
business computers. Introduced in 1985, the GUI-based OS has been released in many
versions since then. The user-friendly Windows 95 was largely responsible for the
rapid development of personal computing.
Mac OS is the operating system for Apple's Macintosh line of PCs and workstations.
Unix is a multiuser operating system designed for flexibility and adaptability.
Originally developed in the 1970s, Unix was one of the first operating systems to be
written in the Linux is a Unix-like operating system that was designed to provide PC
users a free or low-cost alternative. Linux has a reputation as an efficient and fast-
performing system.
Operating system functions
Controls the backing store and peripherals such as scanners and printers.
Deals with the transfer of programs in and out of memory.
Organizes the use of memory between programs.
Organizes processing time between programs and users.
Maintains security and access rights of users.
Uses of operating system
Manage the computer's resources, such as the central processing unit, memory, disk
drives, and printers,
Establish a user interface, and
Execute and provide services for applications software.
Windows 10 system requirements
Processor: 1 gigahertz (GHz) or faster processor
RAM: 1 gigabyte (GB) for 32-bit or 2 GB for 64-bit.
Hard disk space: 16 GB for 32-bit OS or 20 GB for 64-bit OS.
Graphics card: DirectX 9 or later with WDDM 1.0 driver
8.2.Explain Install and upgrade application software

Version -1
Page 96 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Install and upgrade application software
What is application software?
Application Software is a type of computer program that performs specific functions. These
functions, performed by application software, can be personal, business as well as
educational. Thus, application Software is also known as end-user software or productivity
software.
Application software enables the user to complete tasks such as creating documents,
spreadsheets, databases, and publications, doing online research, sending email, designing
graphics, running businesses, and even playing games.
When a user interacts directly with a piece of software, it is called application software. The
sole purpose of application software is to assist the user in doing specified tasks. Microsoft
Word and Excel, as well as popular web browsers like Firefox and Google Chrome, are
examples of application software.
Who is the father of software?
Watts Humphrey, the “Father of Software Quality,” passed away at his residence in Florida
on October 28, 2010. His unparalleled contribution to software engineering made him one of
the icons of the discipline.
Types of Application Software
Web browsers.
Presentation software.
Spreadsheet software.
Graphic software.
Word processors.
Database software.
Multimedia software.
Education software.
Advantages of Application Software:
Their single greatest favorable position is that it meets exact requirements of client.
Business that accompanies it can confine access and may think of intends to monitor
their organization additionally.
What are operating system utilities?
In computers, a utility is a small program that provides an addition to the capabilities
provided by the operating system. In some usages, a utility is a special and nonessential part
of the operating system. The print "utility" that comes with the operating system is an
example.

Version -1
Page 97 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Third Party Utilities means computer programs provided by third parties which OSHPD is
authorized under this Agreement to access through the Services, where OSHPD is not
obligated to enter into a separate agreement with a third party to use such computer programs.
What is the difference between OS and utility software?
This software is focused on how OS works on that basis it perform task to enable smooth
functioning of computer.
How to design graphical user interface?
Best Practices for Designing an Interface
Keep the interface simple.
Create consistency and use common UI elements.
Be purposeful in page layout.
Strategically use color and texture.
Use typography to create hierarchy and clarity.
Make sure that the system communicates what's happening.
Think about the defaults.
Changing the GUI Appearance
Create or load a saved session.
In the Category dialog, click Window > Appearance.
In the Font settings, click the Change… button.
Select Font: Courier New, Regular Size: 10.
Click Apply.
What are the 4 features of a graphical user interface?
Answer: the four features of A Graphical User Interface (GUI) are constituted of four main
parts Windows, Icons, Menus and Pointer. They are also the Main Components of the
Interface, also known as the WIMP system.
How can I Personalize my operating system?
Windows 10 allows you to tweak the looks and feels of the OS, making it appear and
work as you want. To access these customization options, press the “Win + I”
shortcut keys on your keyboard to open the settings app and then select
“Personalization” from the options.
8.3.Identify Use graphical user interface and command-line
interface

Version -1
Page 98 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
How do I create a GUI in Windows 10?
Click File > New, then select Dialog System Screen set on the New dialog box, and
click OK. Click Yes on the message asking if you want to create a project. Select
Windows GUI Project. Enter Welcome as the name of the project.
Types of user interfaces
1. Graphical user interface (GUI)
2. Command line interface (CLI)
3. Menu-driven user interface.
4. Touch user interface.
5. Voice user interface (VUI)
6. Form-based user interface.
7. Natural language user interface
Types of Utility Software
Antivirus
A virus is malicious software that enters the system along with a host program.
File Management System.
This utility software are used to manage files of the computer system.
1. Compression Tools.
2. Disk Management Tools.
3. Disk Cleanup Tool.
4. Disk Defragmenter.
5. Backup Utility.
8.4.Use third-party operating system utilities
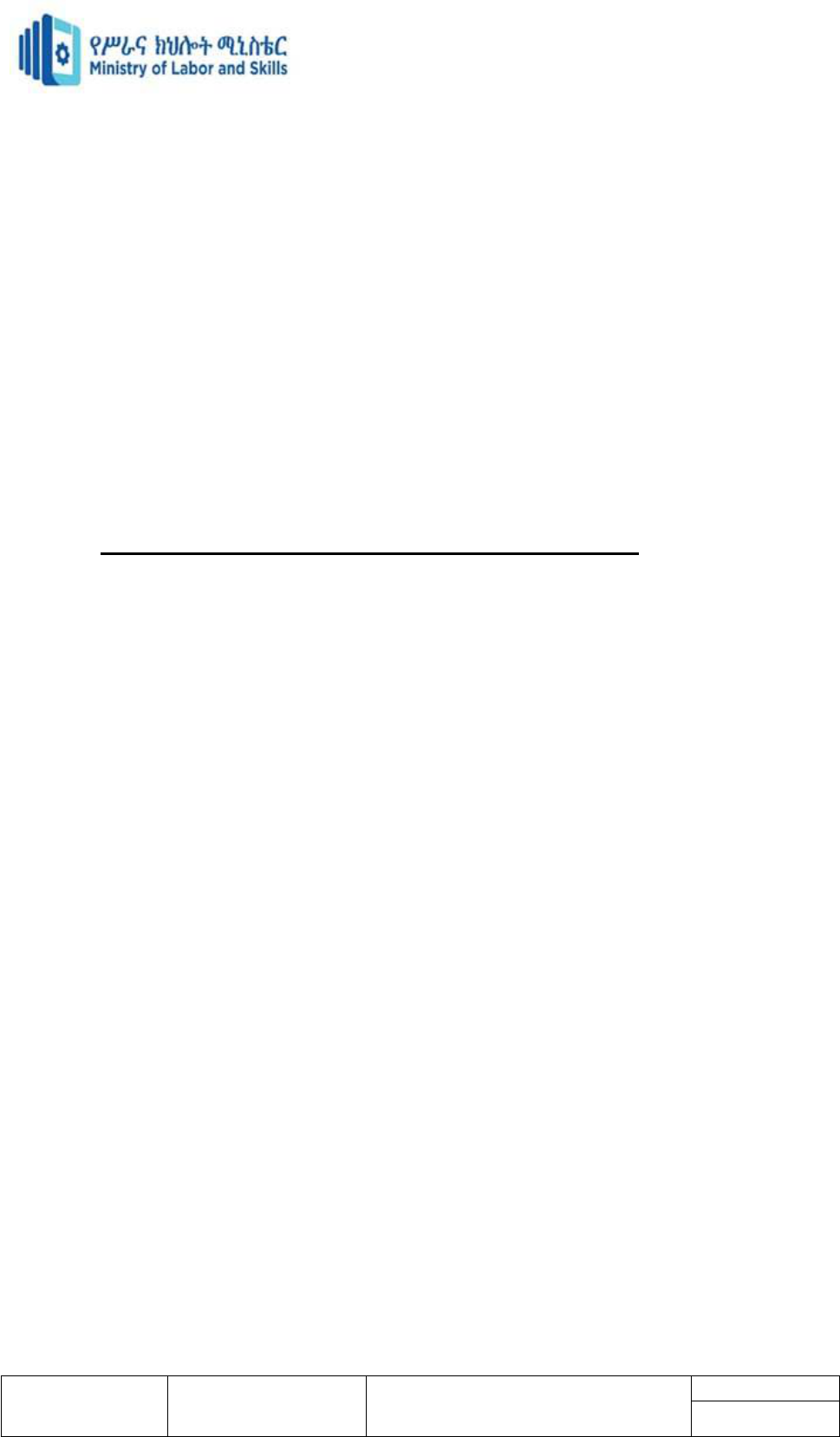
Version -1
Page 99 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Self check test-8
Name ______________________________________ IDNo ___________ Level
___________
Start time ________________ finishing time
______________________
Instruction:- Read the following questions carefully and answers your choices.
I. Choose the correct answer from 1-10 and write your answer.
A. Small program that provides an addition to the capabilities provided by the __________.
A. Application software C. Data base management
B. Operating system D. None
B. An Application software provide for the end user __________________.
A. To complete the tasks like
B. To run Business
C. No answer
D. A & B are
C. From the following alternatives one is well described about Operating system.
A. Operating system Manages all of the software and hardware on the computer
B. Operating system should be installed after Application software being installed
C. All Operating system hasn’t GUI
D. None
D. Which one of the following is function of an operating system.
A. Organizes the use of memory between programs
B. Uses of operating system
C. Maintains security and access rights of users
D. Establish a user interface
E. What is an operating system?
A. Interface between the hardware and application programs
B. Collection of programs that manages hardware resources
C. System service provider to the application programs
D. All of the mentioned
6. Which one of the following errors will be handle by the operating system?
A. Lack of paper in printer
B. Connection failure in the network
C. Power failure
D. All of the mentioned

Version -1
Page 100 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
7. Where is the operating system placed in the memory?
A. Either low or high memory (depending on the location of interrupt vector)
B. In the low memory
C. In the high memory
D. None of the mentioned
8. The main memory accommodates ____________
C. Cpu C. operating system
D. User processes D. all of the mentioned
9. The operating system is responsible for?
A. bad-block recovery C. disk initialization
B. booting from disk D. all of the mentioned
10. The operating system keeps a small table containing information about all open files
called ____________
A. file table C. Open-file table
B. directory table D. System table
II. From question number 11-13 say True if the question is correct and False if
it is incorrect.
11. A user interacts directly with a piece of software called application software. T
12. Unix is a multiuser operating system designed for flexibility and adaptability
developed in the 1970s. T
III. Match the following columns
A B
1. Application software A. Windows
2. Operating system B. Web browsers
3. 1 gigahertz (GHz) processor speed C.NIC
D. Windows 10 requirements

Version -1
Page 101 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Operation Sheet 5.
Install Windows 10
How to install Windows 10: Full installation
Check your device meets the Windows 10 system requirements. ...
Create USB installation media.
Run the installer tool.
Use your installation media.
Change your computer's boot order.
Restart your device.
Complete the installation.
Steps to install
Insert your installation DVD or drive.
Restart the PC.
Select the option to boot from the media and press any key to start from media.
Select your language preferences and click Next.
Click Install Now.
Enter your product key and click Next.
Accept the terms.
Follow the on-screen instructions.
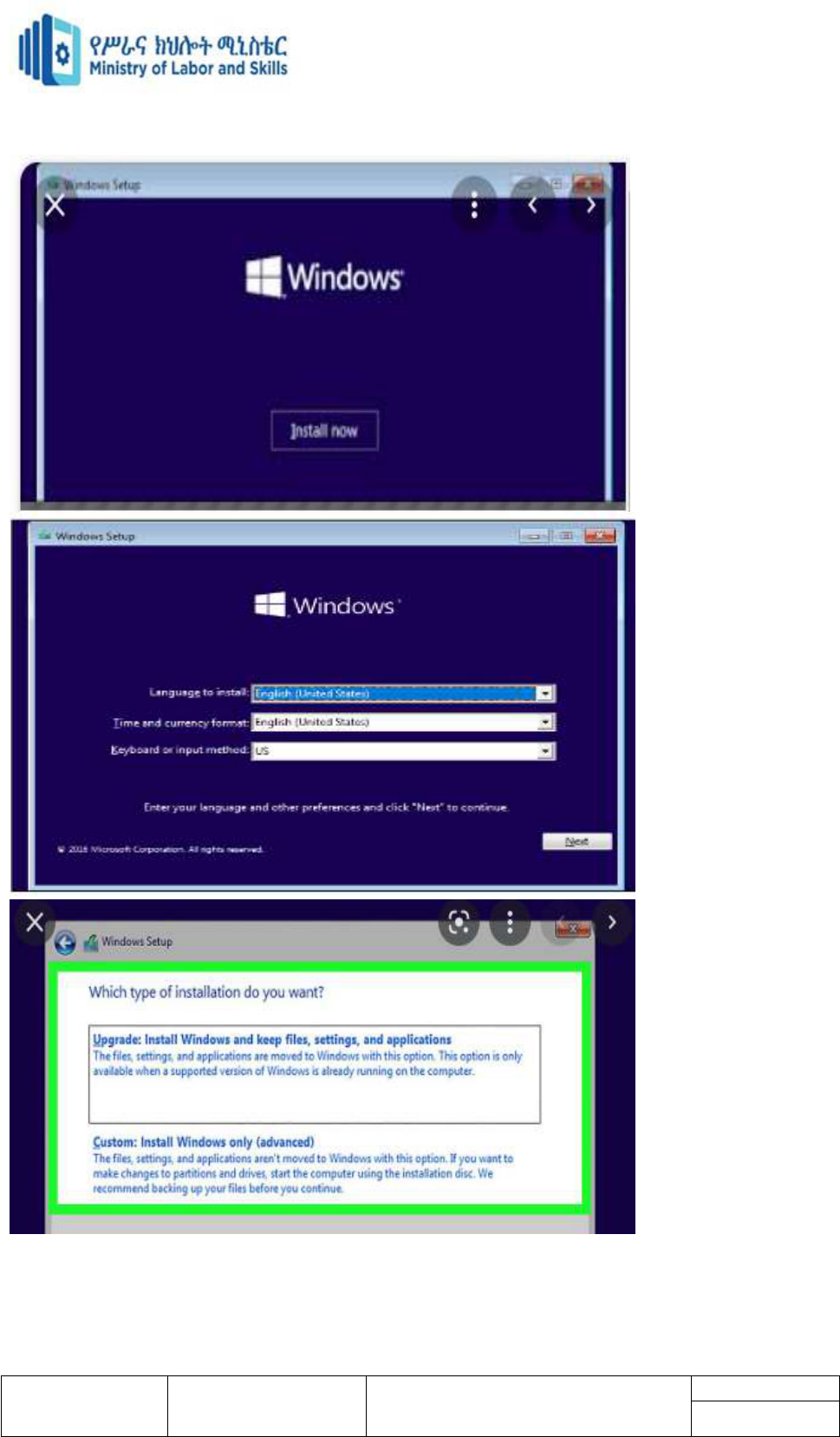
Version -1
Page 102 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
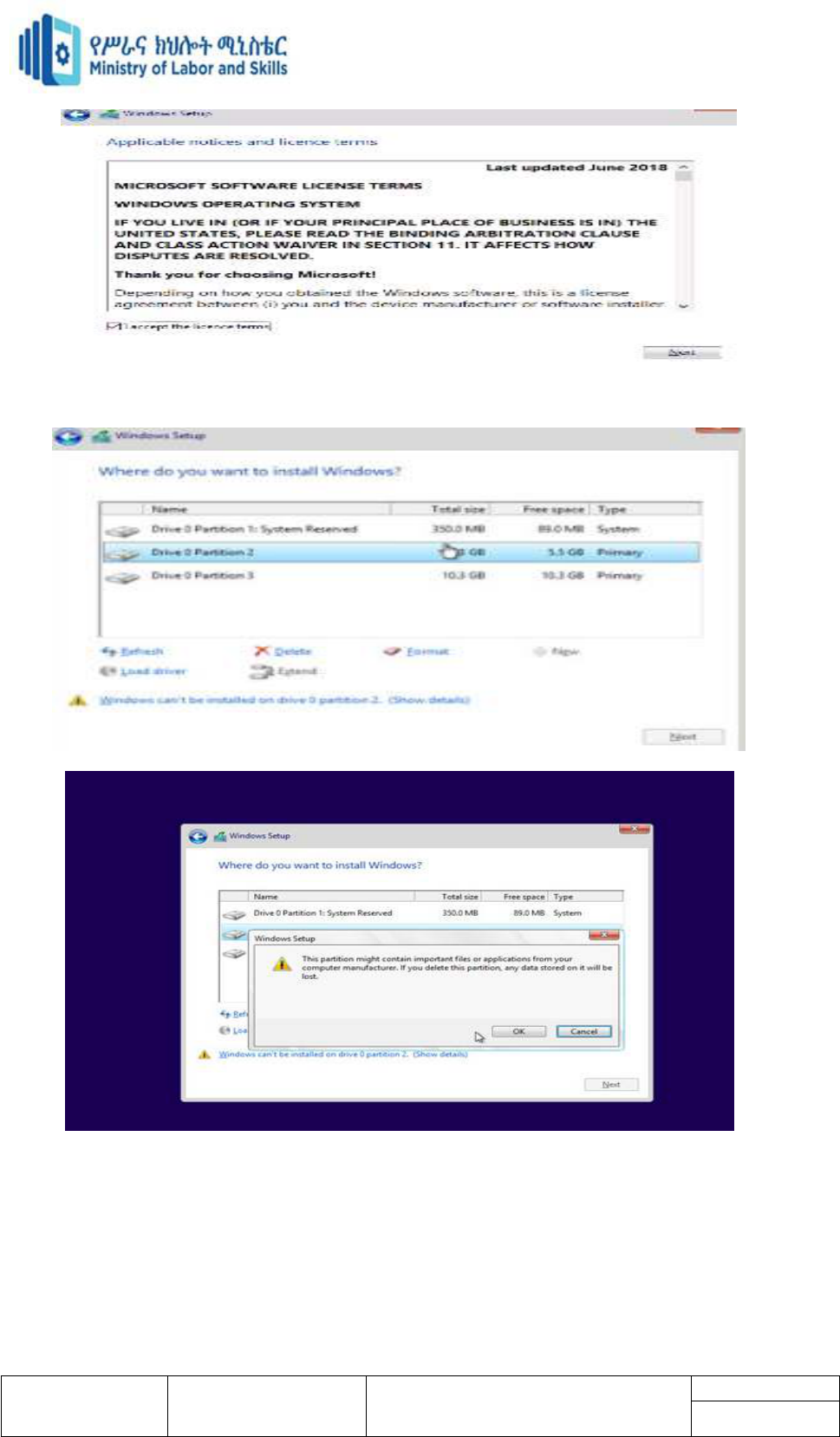
Version -1
Page 103 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022

Version -1
Page 104 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Operation sheet-6
Install and Microsoft Office
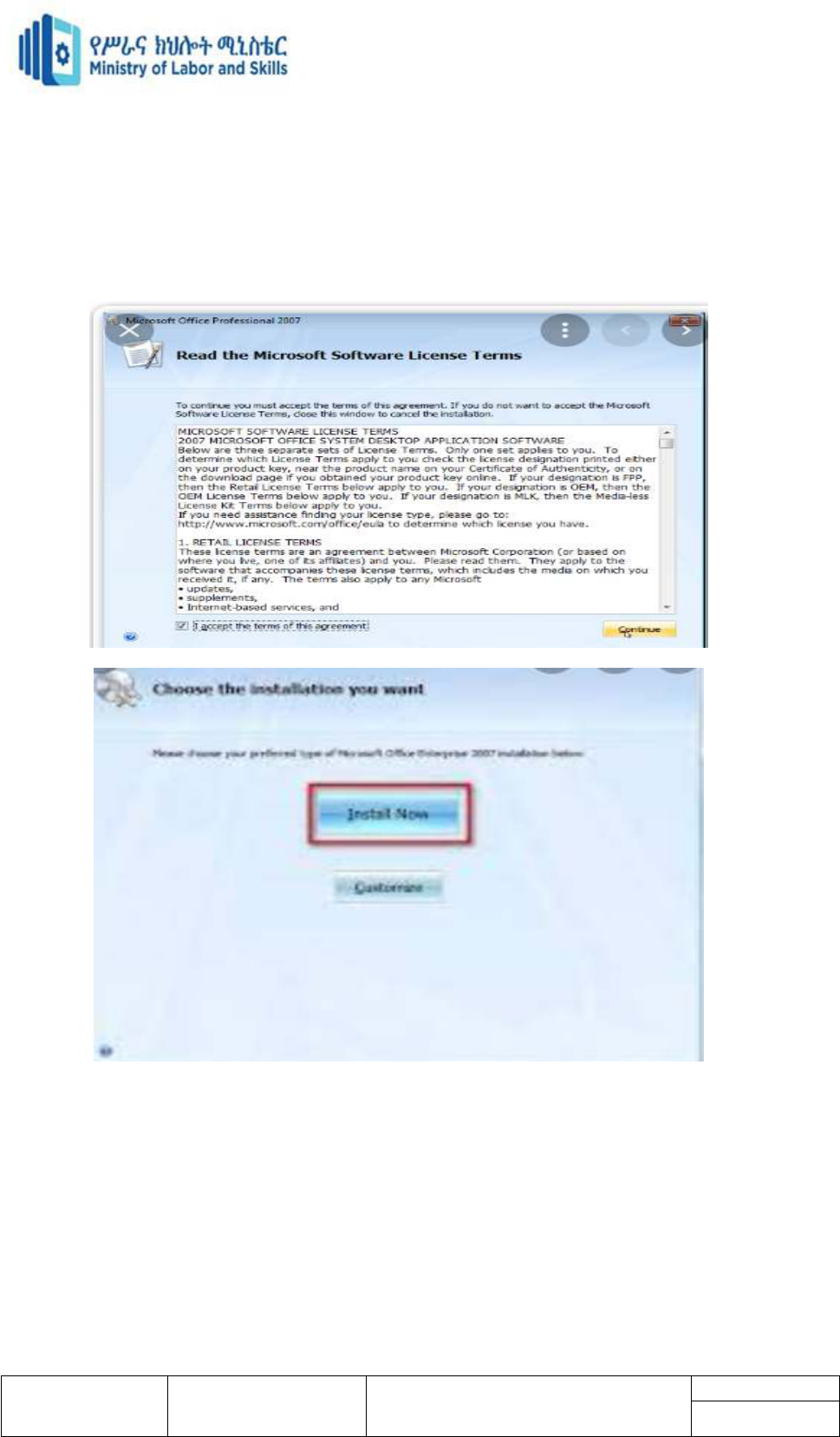
Version -1
Page 105 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Install Office 2007
Insert your Office 2007 CD into the drive.
When prompted, enter the product key.
Read and accept the Microsoft Software License Terms, and then click Continue.
Follow the prompts and after Office installs,
click Close.
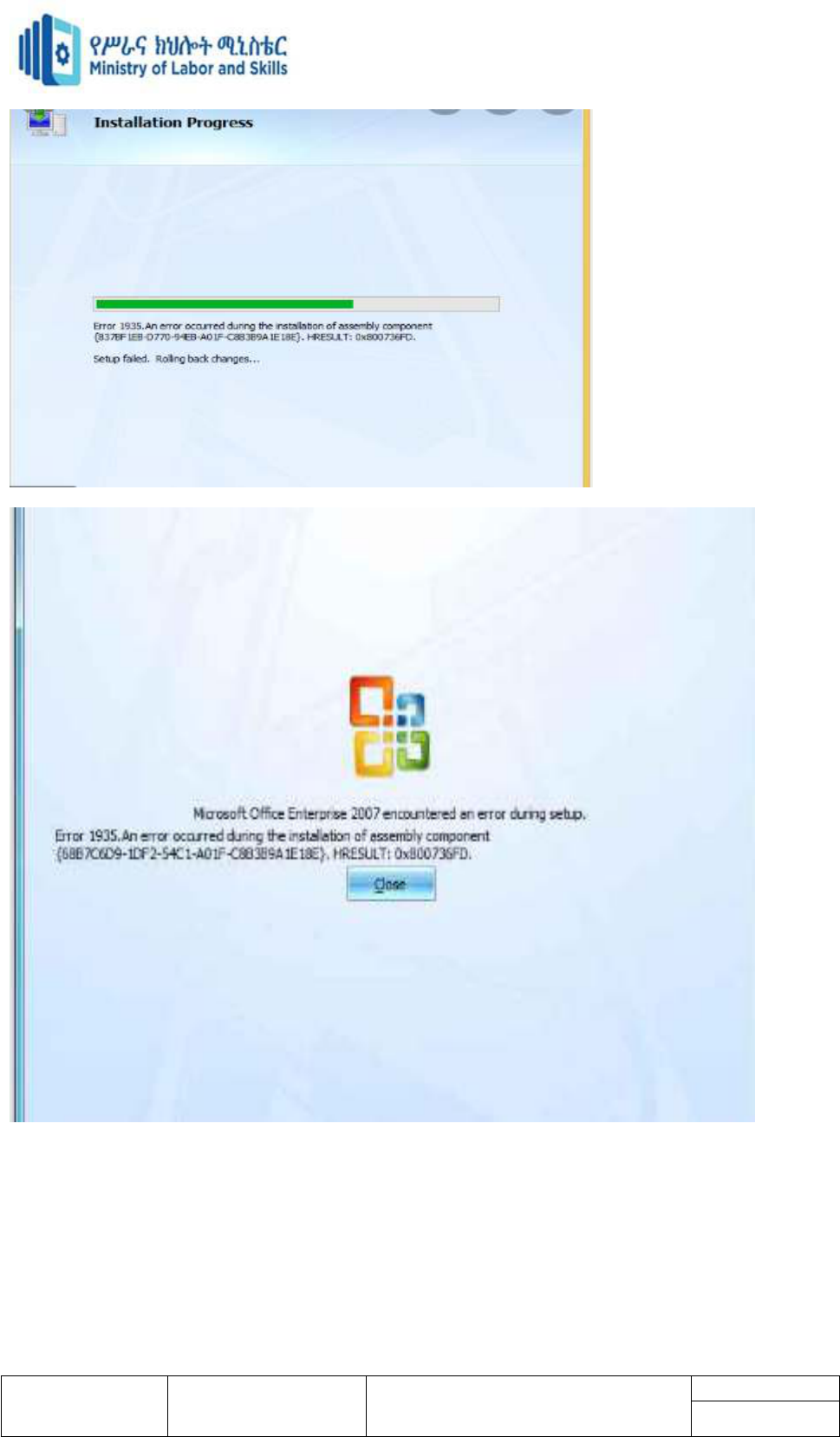
Version -1
Page 106 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022

Version -1
Page 107 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Lap test 5
1. Install Windows 10:
Follow Full installation procedure
1. Check your device meets the Windows 10 system requirements.
2. Create USB installation media.
3. Run the installer tool.
4. Use your installation media.
5. Change your computer's boot order.
6. Restart your device.
7. Complete the installation.
8. Create you account called ITL2
2. Install application software.
1. Install Office 2007
2. Insert your Office 2007 CD into the drive.
3. When prompted, enter the product key.
4. Read and accept the Microsoft Software License Terms, and then click Continue.
5. Follow the prompts and after Office installs,
6. Click Close.
3. Install antivirus
1. Using an antivirus is essential when trying to keep your computer healthy and
free from viruses.
2. Install an Antivirus.
3. Keep Your Software up to Date.
4. Backup Your Computer.
5. Use a Strong Password.
6. Watch the Downloads.

Version -1
Page 108 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
7. Install an Ad-block.
8. Run a Virus Scan Often
Avast Free Antivirus really is free — you'll never need to pay for it and it'll provide you with
essential online security and protection. If you're looking for more security and privacy
features, our Avast Premium Security software is the right product for you.
Unit Nine:- Support input and output devices
This Unit is developed to provide you the necessary information regarding the following
content coverage and topics
Identify input/output devices functionality
Explain appropriate driver installation
This guide will also assist you to attain the learning outcome stated in the cover page.
Specifically, upon completion of this Learning Guide, you will be able to
Input or output device functionality explained according to policy guidelines
Identify deriver installation

Version -1
Page 109 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Check Input and Output devices functionality
In computing, an input device is a piece of equipment used to provide data and control
signals to an information processing system, such as a computer or information appliance.
Examples of input devices include keyboards, mouse, scanners, cameras, joysticks, and
microphones.
Input and output devices allow the computer system to interact with the outside world by
moving data into and out of the system. An input device is used to bring data into the system.
Some input devices are:
Keyboard
Mouse
Microphone
Bar code reader
Graphics tablet
An Input/output device error on the computer happens when a drive is inaccessible. So when
you try to open a drive, you would see the error message – the request could not be
performed. I/O errors cause a panic because sometimes, your files may get deleted. And
often, there is no feasible way to recover them.
An I/O device error (short for Input/output device error) happens when Windows is not able
to perform an input/output action (such as reading or copying data) when it is trying to access
a drive or disk. It can occur to many different types of hardware devices or media.
An I/O device error is a problem with the device that prevents Windows from perusing its
content or writing on it. It can show up on the hard drive (HDD or SSD), external hard disk,
USB, SD card, CD/DVD, and so on. If the external hard drive is showing a disk I/O error,
you can't move PC data to and from that drive. The most common cause of a non-accessible
I/O error is a disconnected cable. When the computer tries to access a device and it gets no
response after several tries, it will generate this type of error. Another common cause is when
a program tries to access a file that has been removed or deleted.
How to Fix a Disk I/O Error in Windows
What Is an I/O Device Error? Input Output device errors are quite common.
Restart Your Computer.
Check Your Cables and Connections.
9.1. Identify input/output devices functionality

Version -1
Page 110 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Try an Alternative USB Port.
Run CHKDSK and SFC.
Update the Device Driver.
Change Your Drive Letter. ...
Use Speccy to Check Drive Health.
What is the use of driver?
A driver, or device driver, is a set of files that tells a piece of hardware how to function by
communicating with a computer's operating system. All pieces of hardware require a driver,
from your internal computer components, such as your graphics card, to your external
peripherals, like a printer.
There are various types of device drivers for I/O devices such as keyboards, mice, CD/DVD
drives, controllers, printers, graphics cards and ports. When a driver is included in an
operating system, it may be referred to as a kernel-mode device driver.
Many parts of a computer need drivers, and common examples are:
Computer printers.
Graphic cards.
Modems.
Network cards.
Sound cards.
Drivers are part of the OS. They run with the same privilege level as the OS kernel, and to
write a driver you must know a good deal about the OS internals.
What would be the benefits of driver software?
Driver management software solves the lack of visibility, as it alerts the managers or dispatch
team of any trouble in real-time. There will be alerts if accidents, mechanical trouble, or any
other problems on the road occur, allowing the dispatch team or managers to respond quickly
to the incident.
Check Driver software work properly
Open Start
Search for Device Manager and
click the top result to open the experience.
Expand the branch for the device that you want to check the driver version.
Right-click the device and select the Properties option.
9.2. Explain appropriate driver installation

Version -1
Page 111 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Self check Test 9.
Name __________________________________ IDNo ________________ Level
__________
Start time ______________________ finishing time
_______________________
Instruction: Choice
1. All peripheral devices are Input devices.
A. True B. False
2. Which one of the following Input devices that help to write or enter the letters and
numbers in to your computer?
A. Keyboard B. Printer C. Monitor Mouse
3. From the given alternatives One is output device
B. Monitor B. Printer C. Projector D. All are answers
4. From the following one is used to control the movement of cursor.
A. keyboard B. Mouse C. Printer D. None
5. All peripheral devices are Input devices.
A. True B. False
6. Which one of the following Input devices that help to write or enter the letters and
numbers in to your computer?
A. Keyboard B. Printer C. Monitor Mouse
7. From the given alternatives One is output device
A. Monitor B. Printer C. Projector D. All are answers
Instruction: True or False
8. Drivers are part of the Operating System.
9. An input or output device error is a problem with the device that prevents Windows from
perusing its content or writing on it.

Version -1
Page 112 of 114
Ministry of Labor and
Skills
Author/Copyright
Administer network and hardware
peripherals
August, 2022
Reference
1. Pakuwal, Bivek. “Graphical User Interface.” LinkedIn SlideShare, 17 Apr. 2015, Available
here.
2. “Command-Line Interface.” Wikipedia, Wikimedia Foundation, 16 July 2018, Available
here.
Participants of this Module (training material) preparation
No
Name
Qualification (Level)
Field of Study
Organization
/ Institution
Mobile number
E-mail
1
Zerihun Abate
A(MSC)
IT
Sabata PTC
0911858358
2
Michael Kassahun
Bsc
IT
Misrak PTC
0989308914
3
sewAyew
W/Yohannies
Msc
IT
Sod PTC
0911716133
4
Yonas Beyan
Msc
IT
Ethio-Italy
PYC
0915007456
5
Abebe Mulatu
Bsc
IT
Daye PTC
0904834788
6
Solomon Yilma
Msc
IT
Asossa PTC
0911954729
7
Yohannes Bekele
Bsc
Computer
science
Hawasa PTC
0939797218
8
Tewdros Girma
Msc
IT
Sheno PTC
0911835002
0912068479
9
Subagadis Gigar
Bsc
Computer
science&ICT
MoLS
0920193859

