
BUSINESS DEVELOPMENT GUIDESEPTEMBER 2023, VERSION 1.0
ZSCALER AND AZURE DEVOPS
DEPLOYMENT GUIDE

2©2023 Zscaler, Inc. All rights reserved.
ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
Contents
Terms and Acronyms 4
About This Document 5
Zscaler Overview 5
Microso Overview 5
Audience 5
Soware Versions 5
Request for Comments 5
Zscaler and Microso Azure DevOps Introduction 6
ZPC Overview 6
Zscaler Resources 6
Microso Azure DevOps Overview 7
Microso Azure DevOps Resources 7
Zscaler Posture Control for Azure Repos 8
Version Control and CI/CD Systems 8
About Security Policies 8
Configuring the Zscaler IaC Scan for Microso Azure Repos 8
Prerequisites 9
Configuring Zscaler IaC Scan App for Azure Repos 11
Viewing the IaC Scan Summary in Azure Repos 16
Viewing Specific IaC Scan Summary in Azure Repos 17
Viewing the IaC Scan Summary in the ZPC Portal 18
Zscaler Posture Control for Azure Pipelines 23
Configuring the Zscaler IaC Scan for Microso Azure Pipelines 23
Prerequisites 23
Download the Zscaler IaC Scan Extension 24
ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
3©2023 Zscaler, Inc. All rights reserved.
Configuring the Zscaler IaC Scan Extension for Microso Azure Pipelines 26
Configuring Zscaler IaC Scan in Azure Pipeline 27
Adding ZPC Credentials as Variables 29
Executing Azure Pipeline and Viewing Zscaler IaC Scan results 31
Viewing Azure Pipeline IaC Scan Summary in the ZPC Portal 33
ZPC Support 38

ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
4©2023 Zscaler, Inc. All rights reserved.
Terms and Acronyms
The following table defines acronyms used in this deployment guide. When applicable, a Request for Change (RFC) is
included in the Definition column for your reference.
Acronym Definition
CA Central Authority (Zscaler)
CSV Comma-Separated Values
DLP Data Loss Prevention
DNS Domain Name Service
DPD Dead Peer Detection (RFC 3706)
GDPR General Data Protection Regulation
GRE Generic Routing Encapsulation (RFC2890)
IaC Infrastructure as Code
ICMP Internet Control Message Protocol
IdP Identity Provider
IKE Internet Key Exchange (RFC2409)
IPS Intrusion Prevention System
IPSec Internet Protocol Security (RFC2411)
NIST National Institute of Standards and Technology
PFS Perfect Forward Secrecy
PSK Pre-Shared Key
SaaS Soware as a Service
SSL Secure Socket Layer (RFC6101)
TLS Transport Layer Security
VDI Virtual Desktop Infrastructure
XFF X-Forwarded-For (RFC7239)
ZDX Zscaler Digital Experience (Zscaler)
ZIA Zscaler Internet Access (Zscaler)
ZPA Zscaler Private Access (Zscaler)
ZPC Zscaler Cloud Protection

ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
5©2023 Zscaler, Inc. All rights reserved.
About This Document
The following sections describe the organizations and requirements of this deployment guide.
Zscaler Overview
Zscaler (NASDAQ: ZS) enables the world’s leading organizations to securely transform their networks and applications for
a mobile and cloud-first world. Its flagship Zscaler Internet Access (ZIA) and Zscaler Private Access (ZPA) services create
fast, secure connections between users and applications, regardless of device, location, or network. Zscaler delivers its
services 100% in the cloud and offers the simplicity, enhanced security, and improved user experience that traditional
appliances or hybrid solutions can’t match. Used in more than 185 countries, Zscaler operates a massive, global cloud
security platform that protects thousands of enterprises and government agencies from cyberaacks and data loss. To
learn more, see Zscaler’s website or follow Zscaler on Twier @zscaler.
Microso Overview
Microso (MSFT) develops and licenses consumer and enterprise soware. It is known for its Windows operating
systems and Office productivity suite. The company is organized into three equally sized broad segments: productivity
and business processes (legacy Microso Office, cloud-based Microso 365, Exchange, SharePoint, Skype, LinkedIn,
Dynamics), intelligence cloud (Infrastructure as a Service and Platform as a Service offerings Azure, Windows Server OS,
SQL Server), and more personal computing (Windows Client, Xbox, Bing search, display advertising, and Surface laptops,
tablets, and desktops). To learn more, refer to Microso’s website.
Audience
This guide is for network administrators, endpoint and IT administrators, and security analysts responsible for deploying,
monitoring, and managing enterprise security systems. For additional product and company resources, see:
• ZPC Support
• Zscaler Resources
• Microso Azure DevOps Resources
Soware Versions
This document was authored using the latest version of Zscaler soware.
Request for Comments
• For prospects and customers: Zscaler values reader opinions and experiences. Contact partner-doc-support@
zscaler.com to offer feedback or corrections for this guide.
• For Zscaler employees: Contact z-bd-sa@zscaler.com to reach the team that validated and authored the
integrations in this document.

ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
6©2023 Zscaler, Inc. All rights reserved.
Zscaler and Microso Azure DevOps Introduction
Overviews of the Zscaler and Microso Azure DevOps applications are described in this section.
ZPC Overview
Zscaler Posture Control (ZPC) is a multi-tenant Soware as a Service (SaaS) platform that detects and responds to cloud
security risks. The service enables your organization to correlate across multiple security engines to prioritize hidden risks
caused by misconfigurations, threats, and vulnerabilities, and achieve continuous security, compliance, and governance.
ZPC leverages cloud service provider APIs to connect to your hybrid, multi-cloud environments and collect real-time
configuration metadata for your cloud infrastructure, such as web servers, databases, and virtual machines. ZPC evaluates
the metadata and offers visibility into your security, compliance, and risk posture.
ZPC includes:
• Cloud Security Posture Management (CSPM). Ensure cloud resources have proper configurations for authentication,
data encryption, internet connectivity, and more for compliance and a strong security posture.
• Cloud Infrastructure Entitlement Management (CIEM). Identify and remediate excessive permissions that humans
and machines have by using machine learning analysis for increased visibility into access policies, resource policies,
actions, and roles.
• Security and Compliance. Benchmark and validate public cloud configurations against best practices standards and
compliance frameworks to report misconfigurations, policy violations, and automate remediation.
• Infrastructure as Code (IaC) Security. Monitor your IaC infrastructure and implement security controls to address any
misconfigurations or security issues before deployment and thereby ensure the code is secure and compliant with
standard security policies.
• Vulnerability Management. Monitor and detect any known vulnerabilities and security weaknesses in the cloud
infrastructure and take immediate action to protect networks from potential threats.
Zscaler Resources
The following table contains links to Zscaler resources based on general topic areas.
Name Definition
ZPC Help Portal Help articles for ZPC.
Zscaler Tools Troubleshooting, security and analytics, and browser extensions that help
Zscaler determine your security needs.
Zscaler Training and Certification Training designed to help you maximize Zscaler products.
Submit a Zscaler Support Ticket ZPC Support portal for submiing requests and issues.

ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
7©2023 Zscaler, Inc. All rights reserved.
Microso Azure DevOps Overview
Microso Azure DevOps provides an integrated set of services and tools to manage your soware projects, from planning
and development through testing and deployment.
Azure DevOps delivers services through a client/server model. You can use most of the services via the web interface,
which you can access from all major browsers. You can manage some services, such as source control, build pipelines,
and work tracking, through a client.
The solution offers an end-to-end soware development platform that offers an assortment of capabilities intended to
organize and accelerate development efforts across the entire application lifecycle:
• Requirement management
• Project management for Agile soware development waterfall teams
• Version control using Team Foundation Version Control (TFVC) or Git
• Automated builds
• Reporting, such as test results, and development metrics, such as backlogs and release velocity
• Testing and release management
Microso Azure DevOps Resources
The following table contains links to Microso Azure DevOps support resources.
Name Definition
Microso Azure Repos
Documentation
Microso Azure Repos Documentation
Microso Azure Repos Training Microso Azure Repos Training Portal
Microso Azure Pipelines Microso Azure Pipelines Documentation
Microso Azure Pipelines Training Microso Azure Pipelines Training Portal
ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
8©2023 Zscaler, Inc. All rights reserved.
Zscaler Posture Control for Azure Repos
The following is an overview of the Zscaler Posture Control and Microso Azure Repos described in this deployment
guide.
Version Control and CI/CD Systems
ZPC offers the Zscaler IaC Scan security feature that enables you to apply security controls on your IaC infrastructure
before deployment. The IaC Scan tool scans the IaC templates for misconfigurations and known vulnerabilities that are
a potential risk for aacks. The IaC Scan tool leverages more than 100 security policies to check for configuration errors
in your code (e.g., missing database encryption, publicly exposed services, etc.) so you can remediate these errors and
ensure your code is secure and compliant with the security policies. To learn more, see About Security Policies.
You can easily integrate the IaC Scan with various code repositories, continuous integration (CI) and continuous
deployment/delivery (CD) tools, and integrated development environments (IDEs). The IaC Scan is also available as a
command line interface tool.
About Security Policies
Security policies protect your cloud deployment from asset misconfigurations and excessive permissions by defining a
condition or parameter for how you must configure a particular cloud asset. ZPC offers over 400 security policies across
multiple cloud service providers (CSPs), including Amazon Web Services, Microso Azure, and Google Cloud Platform.
ZPC has created security policies to protect both your runtime and build time environments. You cannot modify security
policies, but you can create new custom security policies tailored for your cloud deployment.
ZPC also bundles security policies to emulate cybersecurity benchmarks (e.g., NIST) or compliance benchmarks (e.g.,
GDPR).
The Policies page provides the following benefits and enables you to:
• View all cloud and IaC policies offered by ZPC.
• Gain cloud posture overview based on whether the policies are passing or failing for your cloud deployment.
• Create custom security policies to cater to your cloud deployment’s compliance requirements.
Configuring the Zscaler IaC Scan for Microso Azure Repos
This section provides step-by-step instructions for integrating the Zscaler IaC Scan app with Azure Repos. The integration
enables the IaC Scan app to scan and monitor your IaC files for misconfigurations.
Soware entitlements are products that you are allowed to use. You can subscribe to the Zscaler IaC Scan
service. If the soware entitlement expires, or if you’ve removed or downgraded the subscription (e.g., reverted
from ZPC-Advanced to ZPC-Essential version), then you cannot perform the IaC scan.
ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
9©2023 Zscaler, Inc. All rights reserved.
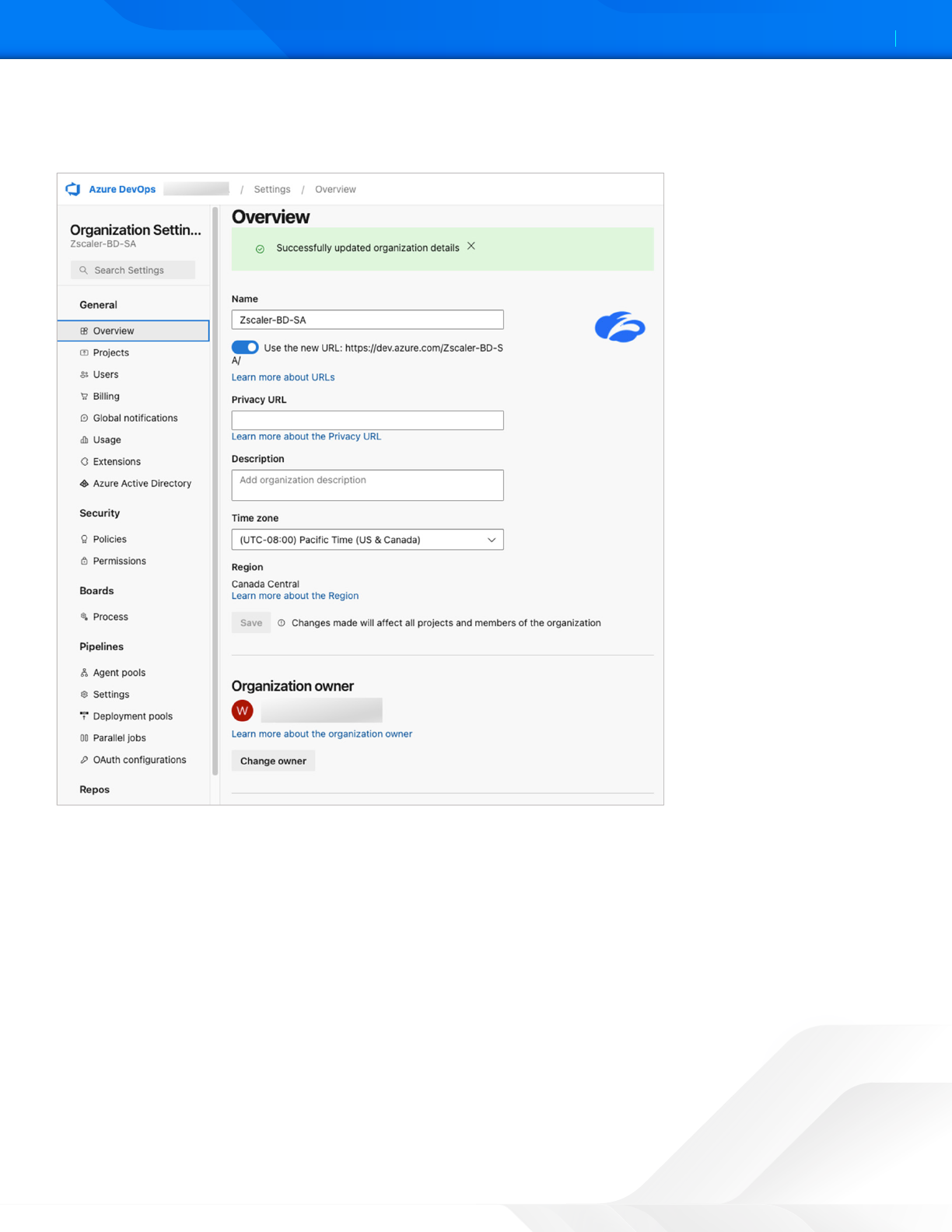
Prerequisites
Notice that only the Azure DevOps organization owner can onboard the Azure organization and accounts.
Figure 1. Azure DevOps Organization Seings
ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
10©2023 Zscaler, Inc. All rights reserved.
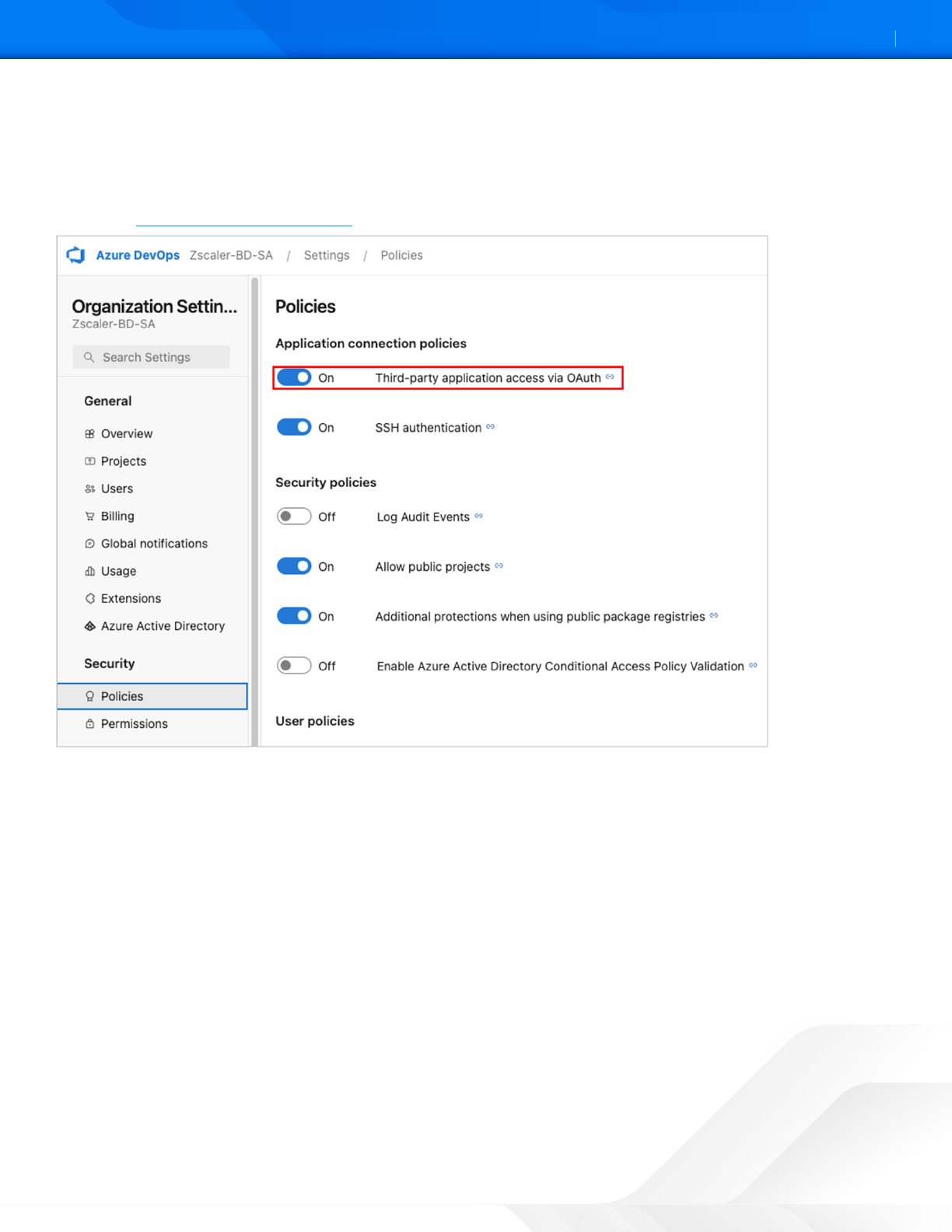
Before proceeding with the integration, you must enable and authorize the ZPC Admin Portal via OAuth to access the
Azure organization and accounts.
1. On the Azure DevOps console, go to Organization Seings > Security > Policies.
2. Under Application connection policies, enable the Third-party application access via OAuth. To learn more, refer
to the Azure DevOps documentation.
Figure 2. Azure DevOps OAuth Security Policy
ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
11©2023 Zscaler, Inc. All rights reserved.
Configuring Zscaler IaC Scan App for Azure Repos
ZPC provides support for integrating the Zscaler IaC Scan with Azure Repos to scan your IaC templates in Azure Repos
repositories. It continuously verifies security misconfigurations against ZPC security controls and displays the failed checks.
The Azure Repos integration allows you to perform IaC scans of the Azure Repos repositories on pull and push requests.
You can perform an IaC scan on the entire repository of a branch or templates that were newly added to the branch. The
scan results are displayed within Azure repos, providing visibility into the IaC policy violations.
To configure the Zscaler IaC Scan app for Azure Repos:
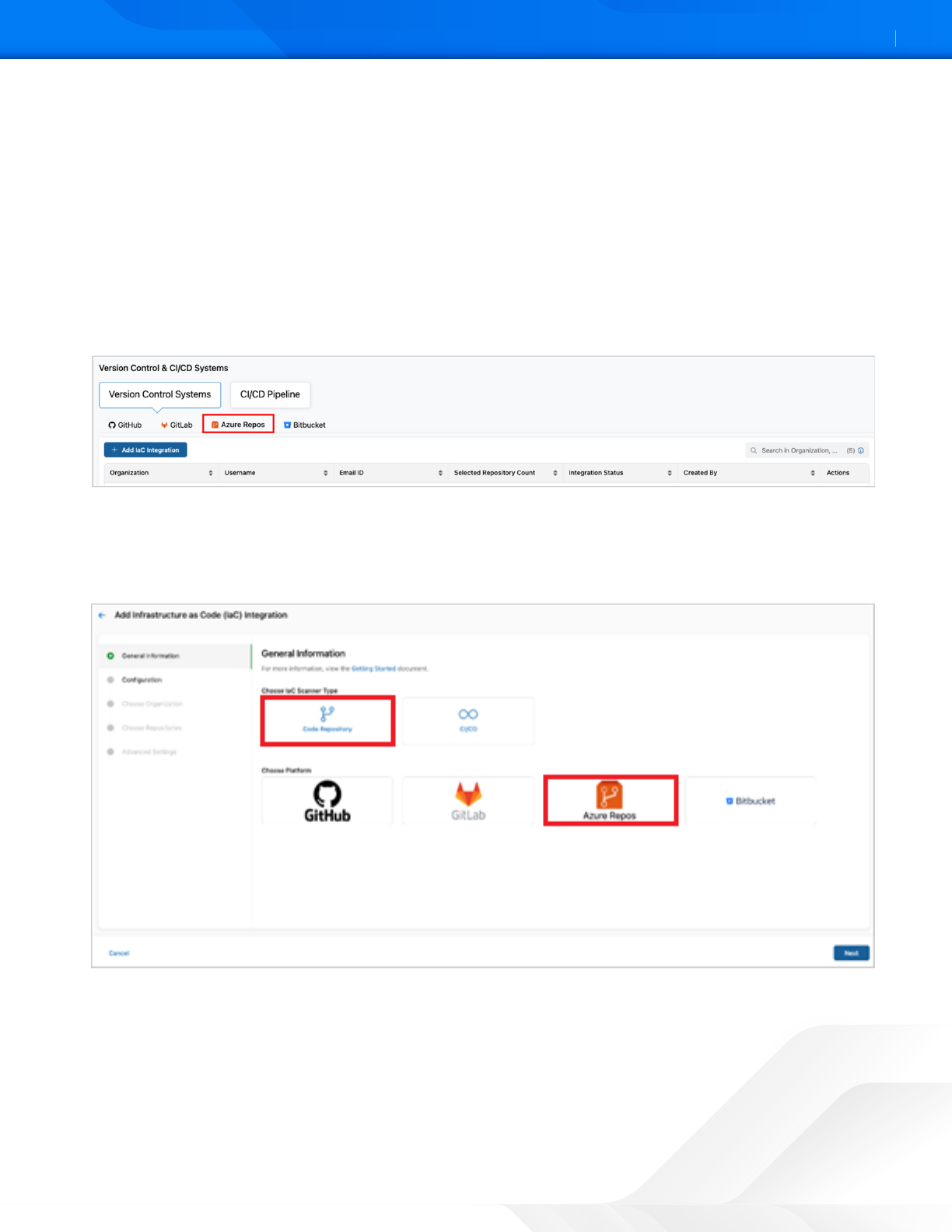
1. Go to Administration > Version Control & CI/CD Systems.
2. On the Version Control & CI/CD Systems page, click Add IaC Integration.
Figure 3. Add Azure Repos IaC integration
3. Under General Information:
a. For Choose IaC Scanner Type, select Code Repository.
b. For Choose Platform, select Azure Repos.
Figure 4. Select Azure Repos integration
ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
12©2023 Zscaler, Inc. All rights reserved.
4. Click Next.
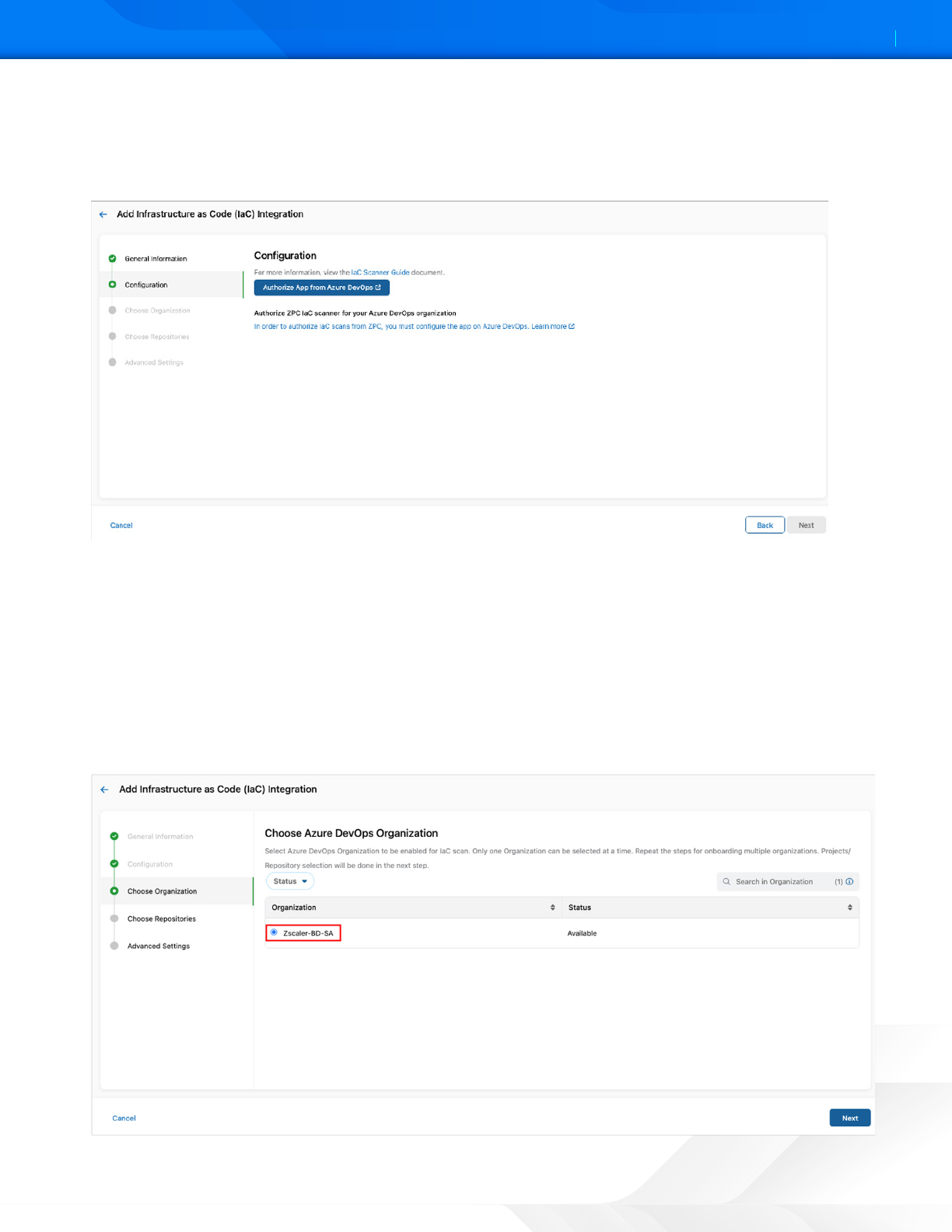
5. Under Configuration, click Authorize App from Azure DevOps to install the IaC Scan app in the Azure DevOps
account. The authorization establishes the connection between Azure DevOps and the ZPC Admin Portal to enable
IaC scanning of the Azure repositories.
Figure 5. Authorize App from Azure DevOps
6. Complete the Azure DevOps Authorization:
a. Log in to your Azure DevOps account.
b. Go through the list of actions that ZPC can perform on Azure DevOps.
c. Click Accept. You are redirected back to the Configuration page in the ZPC Admin Portal.
7. Click Next.
8. Under Organization, select the required Azure organization.
Figure 6. Choose Azure DevOps Organization
ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
13©2023 Zscaler, Inc. All rights reserved.
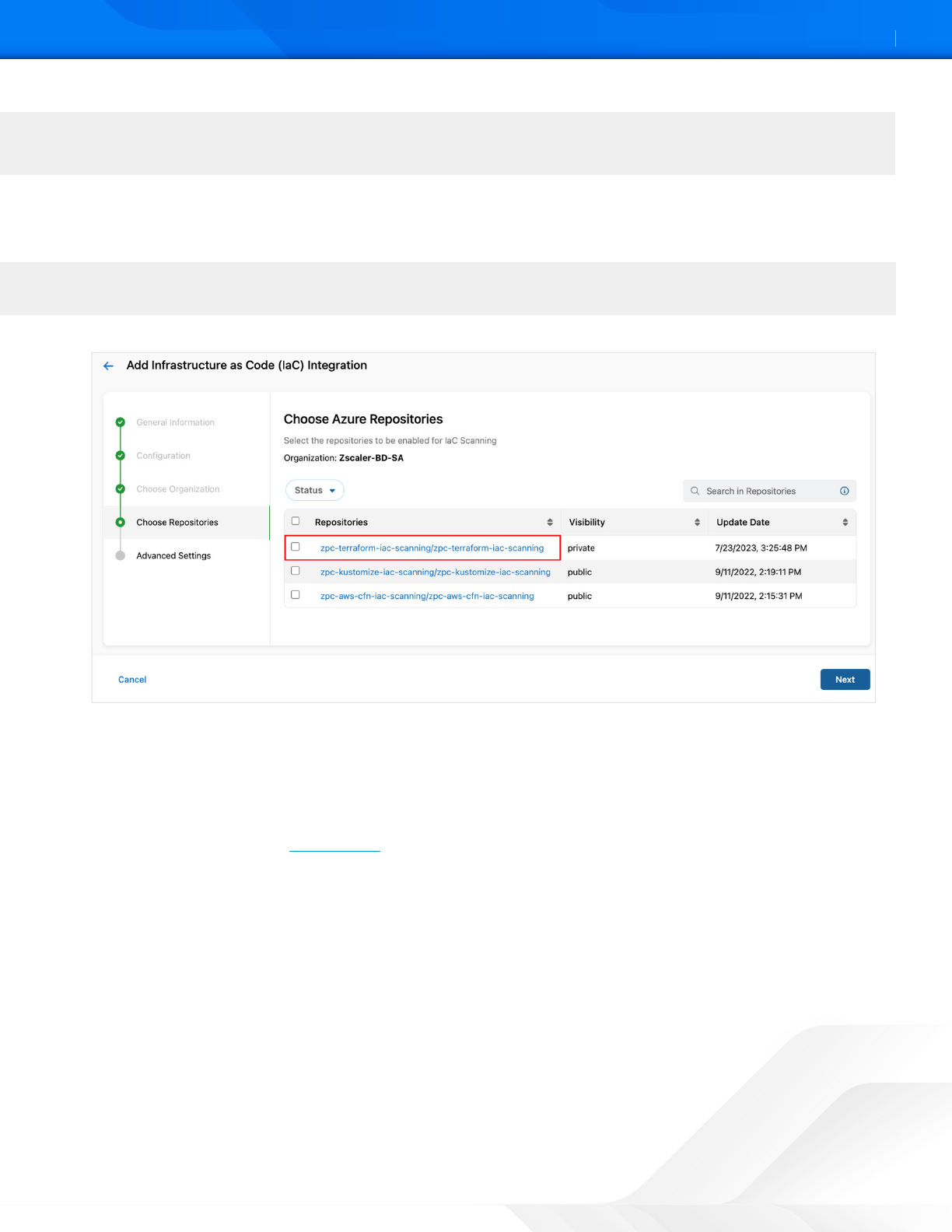
9. Click Next.
10. Under Choose Azure Repositories, enable the repositories for scanning.
Figure 7. Choose the Azure Repositories
11. Click Next.
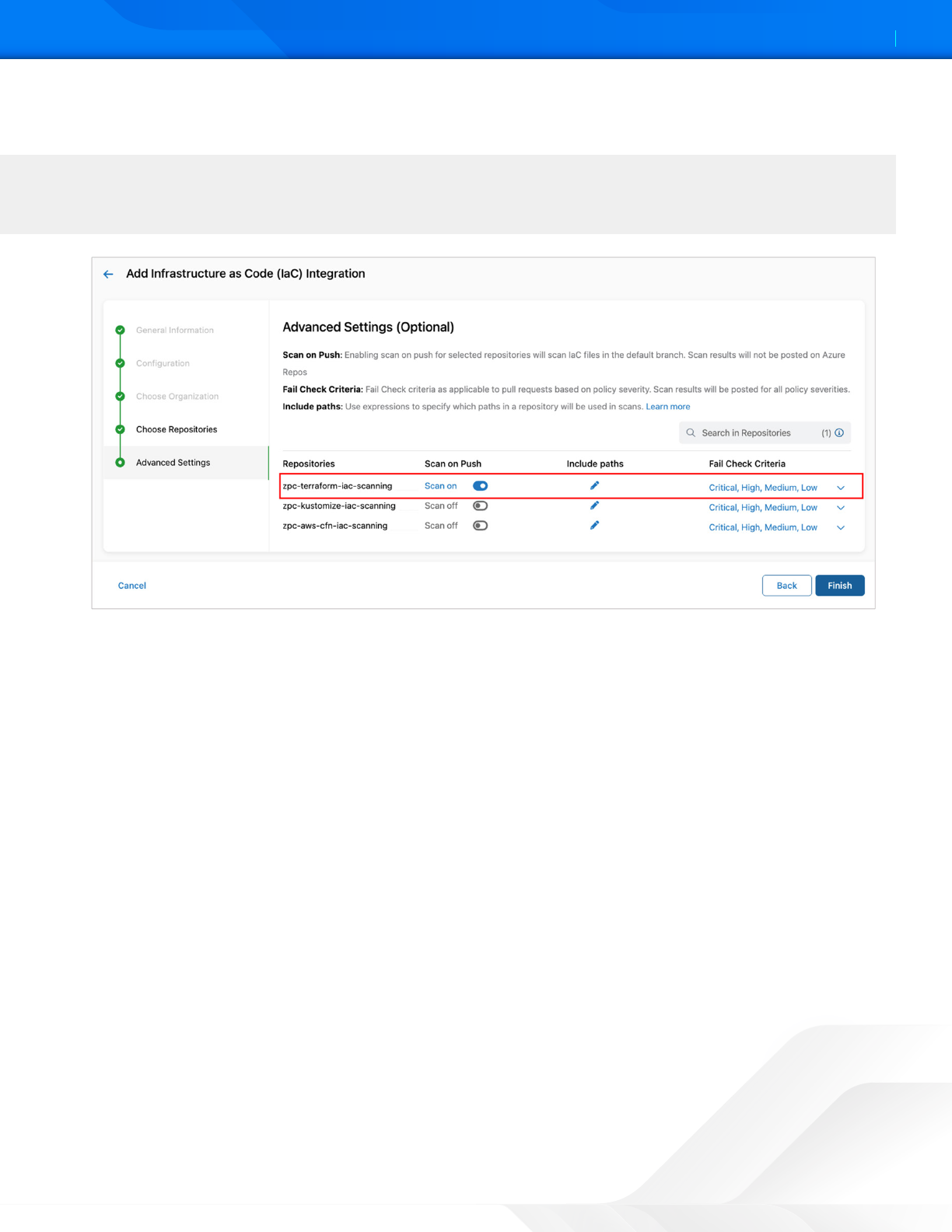
12. (Optional) Under Advanced Seings:
• Scan on Push: Click the tole to scan the code for a push command. The IaC Scan app performs the scan in
the background and triers alert notifications for any policy violations and displays the alerts in the ZPC Admin
Portal. To learn more, see About Alerts.
• Include Paths: Click the Edit icon to include the path of the specific folder for scanning within the repository. For
example, if you define an include path for a single file, then only that file is scanned and all other files and folders
within the repository are ignored. You can use regular expressions (regex) to search for and include files or folders
that must be scanned.
You can only add one organization at a time, and you cannot select organizations that are already onboarded.
Repeat the integration steps to add multiple organizations, even if they are within the same Azure account.
The date and time format displayed is based on the browser locale.

ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
14©2023 Zscaler, Inc. All rights reserved.
Regex Paern Description Example
/**/ Match zero or more directories If you type charts/**/, then the following files are
included:
• charts / docker.yml
• charts / stub
• charts / stub / config.yml
• charts / server / config / app1 / app.yml
**/ Match any directory/directories,
start of paern only
If you type **/internal/test/**, then the following files are
included:
• root/internal/test/stub.txt
• internal/test/stub.txt
• /internal/test/server
• root/internal/test
/** Match any directory/directories,
end of paern only
If you type monorepo/**/terraform/**, then the
following files are included:
• monorepo/terraform/doc.tf
• monorepo/app1/terraform
• monorepo/app1/terraform/stub.yml
• monorepo/app1/app2/terraform
* Match any non-separator
character
If you type *repo/**/terraform/**, then the following files
are included:
• monorepo/terraform/doc.tf
• monorepo/app1/terraform
• publicrepo/app1/terraform/stub.yml
• newrepo/app1/app2/terraform
! Excludes all matches from the
result set, start of paern only
If you type !**/internal/test/**, then the following files
are excluded:
• root/internal/test/stub.txt
• internal/test/stub.txt
• /internal/test/server
• root/internal/test
ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
15©2023 Zscaler, Inc. All rights reserved.
• Fail Check Criteria: Fail check criteria applies to only pull requests based on policy severity. Select the security
threshold (Critical, High, Medium, or Low) for the policy from the drop-down menu.
Figure 8. Advanced Seings
13. Click Finish.
You can apply a security threshold to each repository. For example, if the fail check criteria are set as Critical and
High and there are only violations with Medium or Low severity, then the Zscaler IaC Scan does not fail the pull
request.
ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
16©2023 Zscaler, Inc. All rights reserved.
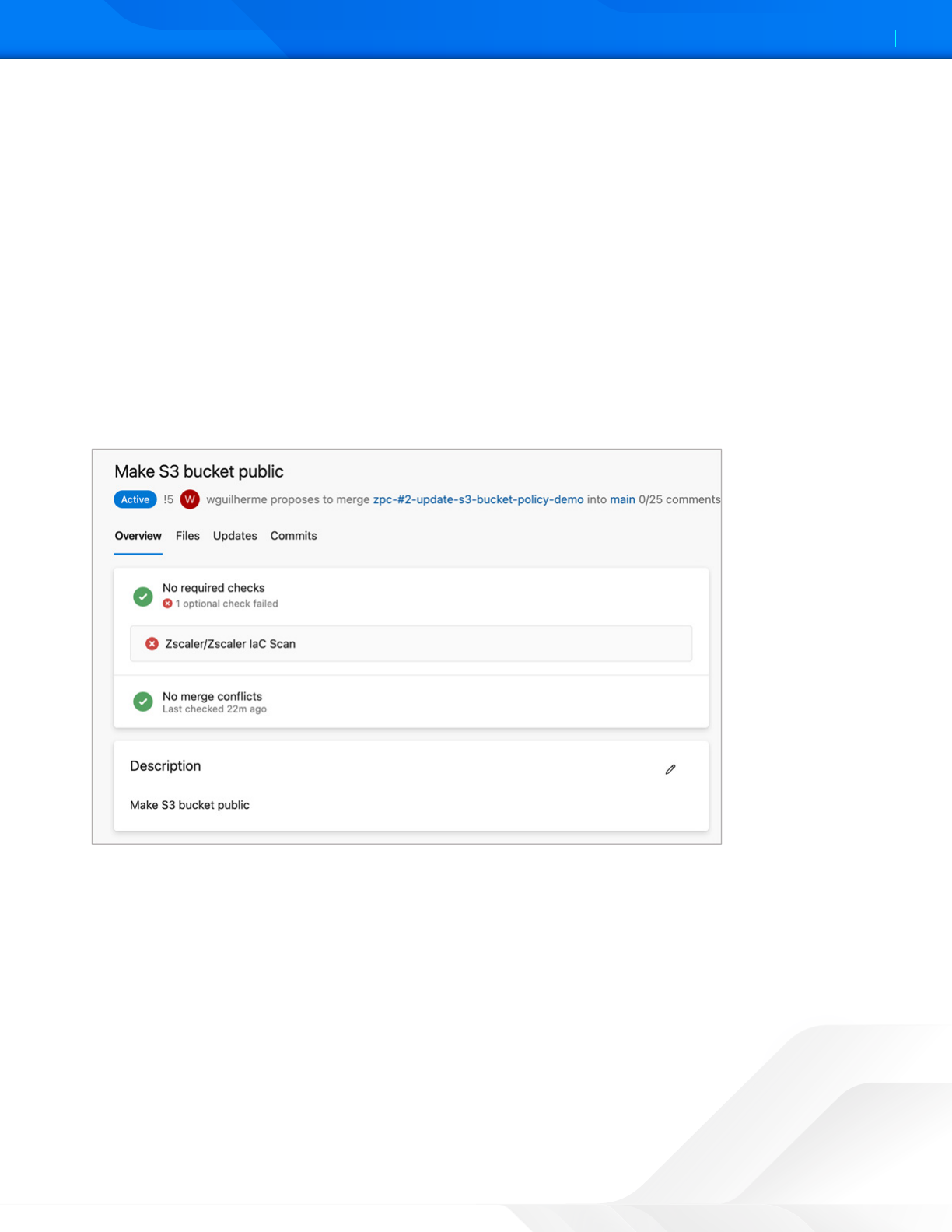
Viewing the IaC Scan Summary in Azure Repos
Aer you enable the selected repositories for scanning, the Zscaler IaC Scan app performs a scan every time you add
or update a code and make a pull request. The IaC Scan app identifies security misconfigurations and displays policy
violations and remediation steps within the code. You can fix the issues and then merge the code.
You can see the total policies along with passed and failed findings. This information indicates if the code is violation-free
for the policies evaluated or if none of the policies were evaluated for this resource. You can see the policy title and ID,
severity, and resource details aer the line of code that has issues.
To view the scan summary report in the Azure Repo pull request:
1. Select the repository where the new pull request was created.
2. Go to Pull Requests.
3. Select the new pull request.
4. Select Overview. The Scan Summary Report is displayed
Figure 9. Zscaler IaC Scan Overview
ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
17©2023 Zscaler, Inc. All rights reserved.
5. Review the Scan Summary Report.
Figure 10. Zscaler IaC Scan Summary
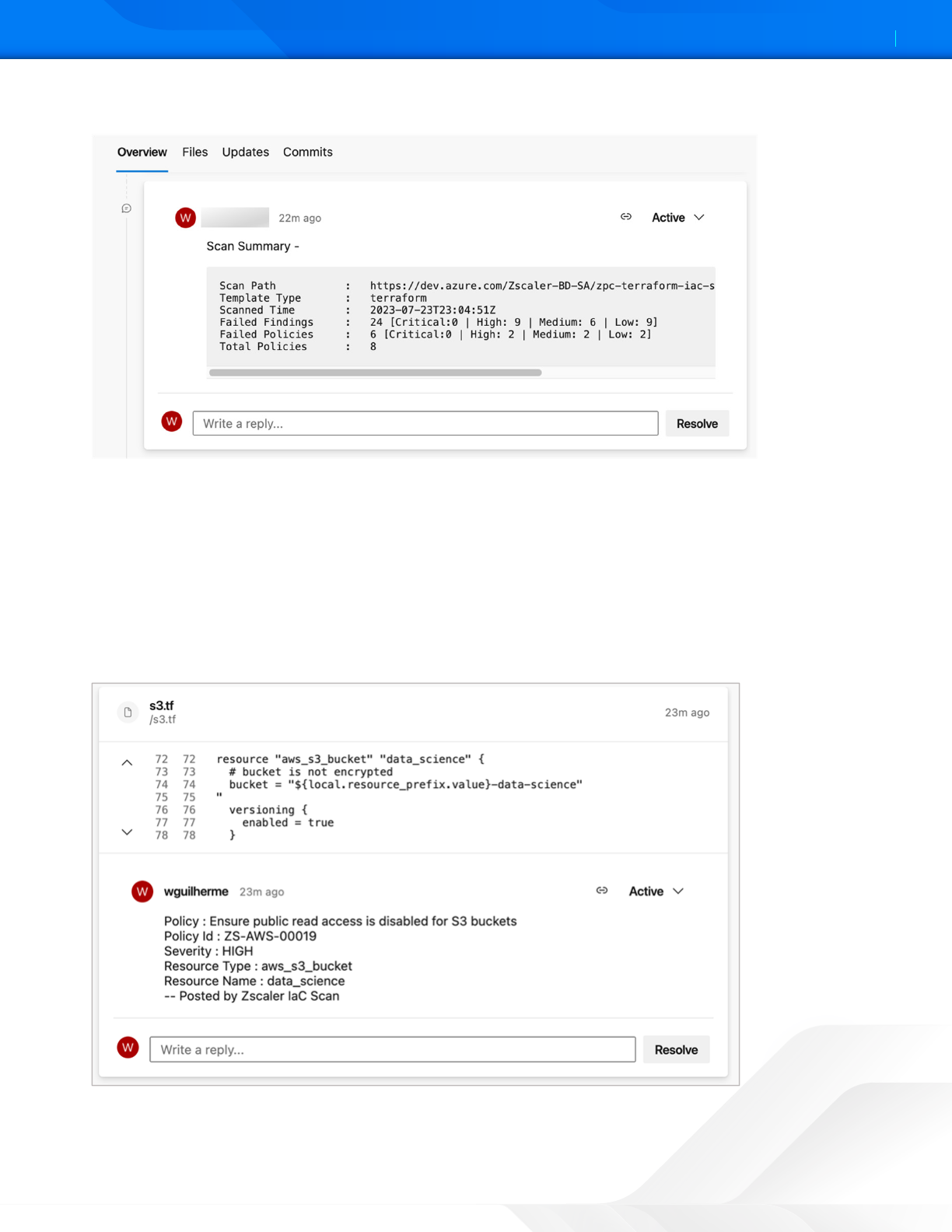
Viewing Specific IaC Scan Summary in Azure Repos
In addition to scan summary, the Azure repos integration with Zscaler Posture Control provides visibility and details on
specific alerts.
To resolve a specific alert via the Azure Repos portal:
1. Click Resolve.
2. Add a comment to the thread.
Figure 11. Zscaler IaC Scan Alert summary
ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
18©2023 Zscaler, Inc. All rights reserved.
Viewing the IaC Scan Summary in the ZPC Portal
To visualize the Azure repos alerts generated by the Zscaler IaC Scan tool:
1. Login to the ZPC Admin Portal.
Figure 12. ZPC Admin Portal
2. Select the Infrastructure as Code widget.
Figure 13. ZPC IaC Widget
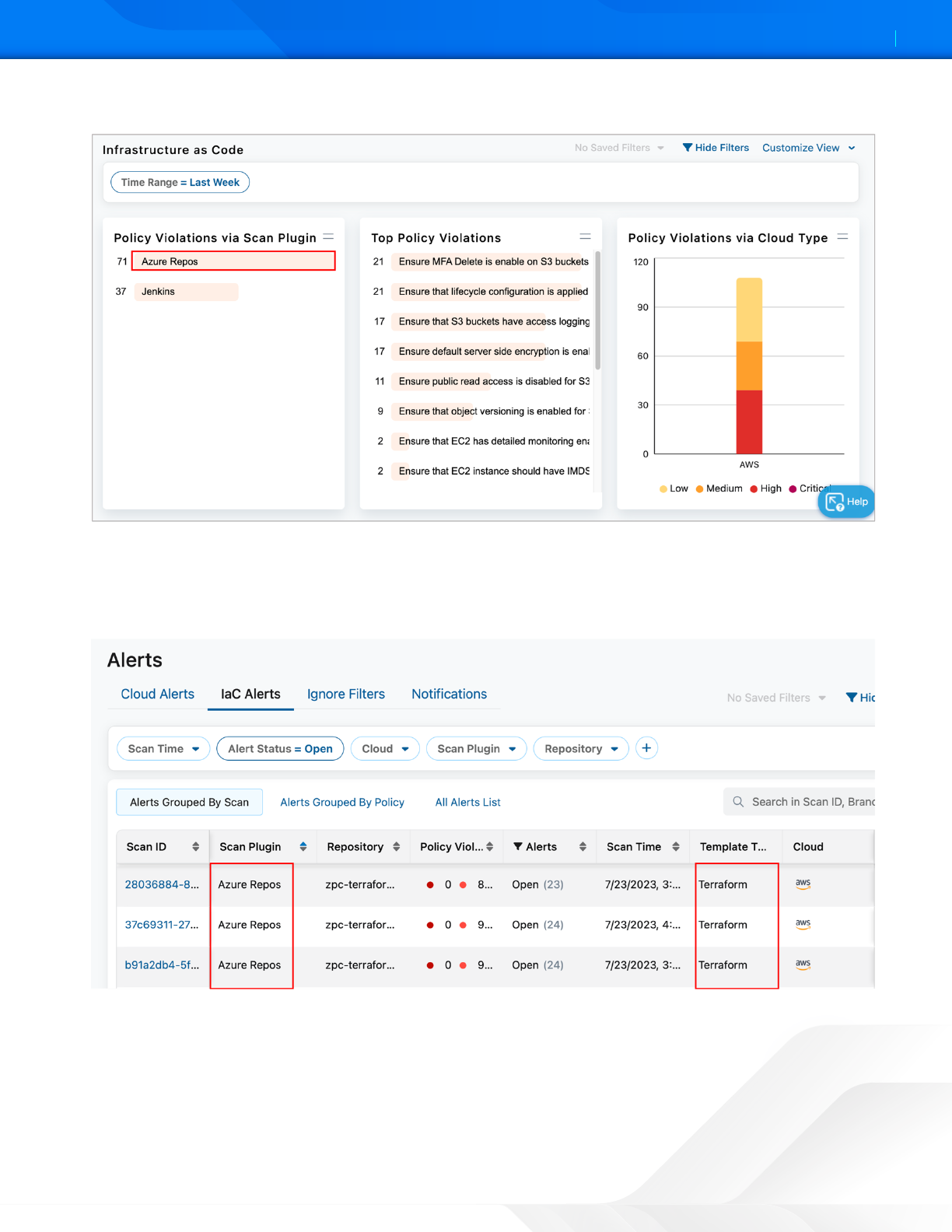
3. In the main Infrastructure as Code dashboard, Zscaler provides a summary of the following:
a. Policy violations identified via the Zscaler Scan Plugin.
b. Top Policy Violations.
c. Policy Violations by Cloud Type.
ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
19©2023 Zscaler, Inc. All rights reserved.
4. Select one of the Top Policy Violations. This example uses Ensure MFA Delete is enabled on S3 buckets.
Figure 14. ZPC Infrastructure as Code Dashboard summary
5. Group the IaC alerts by Scan type. In the following example, the filter only displays Scan Plugin = Azure Repos.
a. Other filters are also available (e.g., Scan Time, Alerts, Cloud, and Repository).
b. Add other filters by selecting the Add (+) icon in the filter area.
Figure 15. ZPC Alerts Grouped by Scan
ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
20©2023 Zscaler, Inc. All rights reserved.
6. (Optional) Select the top violations and ZPC automatically creates an IaC alerts filter containing all violations
originated by the Azure Repos Scan Plugin.
Figure 16. ZPC Alerts Grouped by Scan
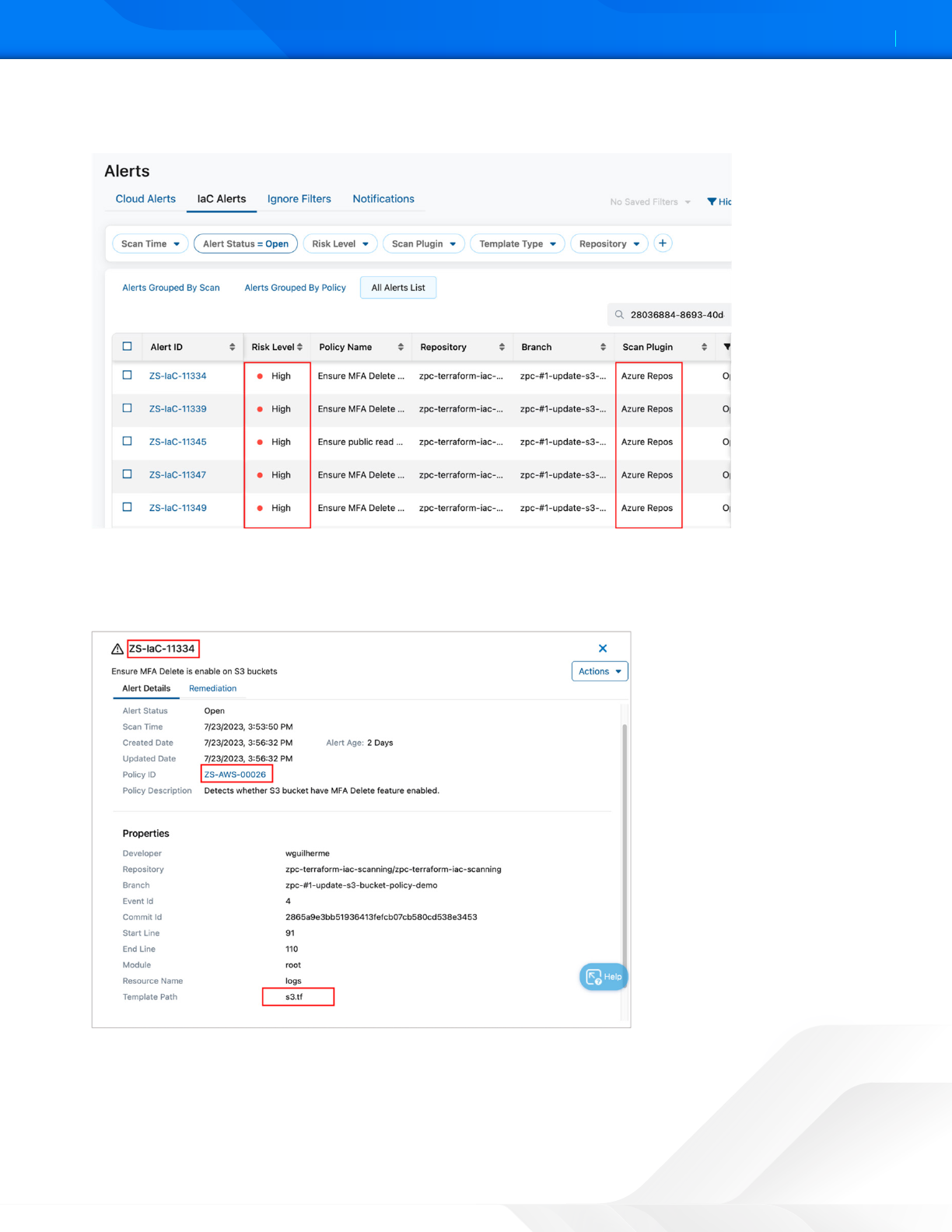
7. Select one of the alerts listed in the Alert ID column. This example selects the alert ID ZS-IaC-11334, which indicates
that ZPC has detected a violation associated with a Policy ID: ZS-AWS-00026. This policy detects whether the MFA
Delete feature is enabled on S3 buckets.
Figure 17. ZPC Alerts Details
ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
21©2023 Zscaler, Inc. All rights reserved.
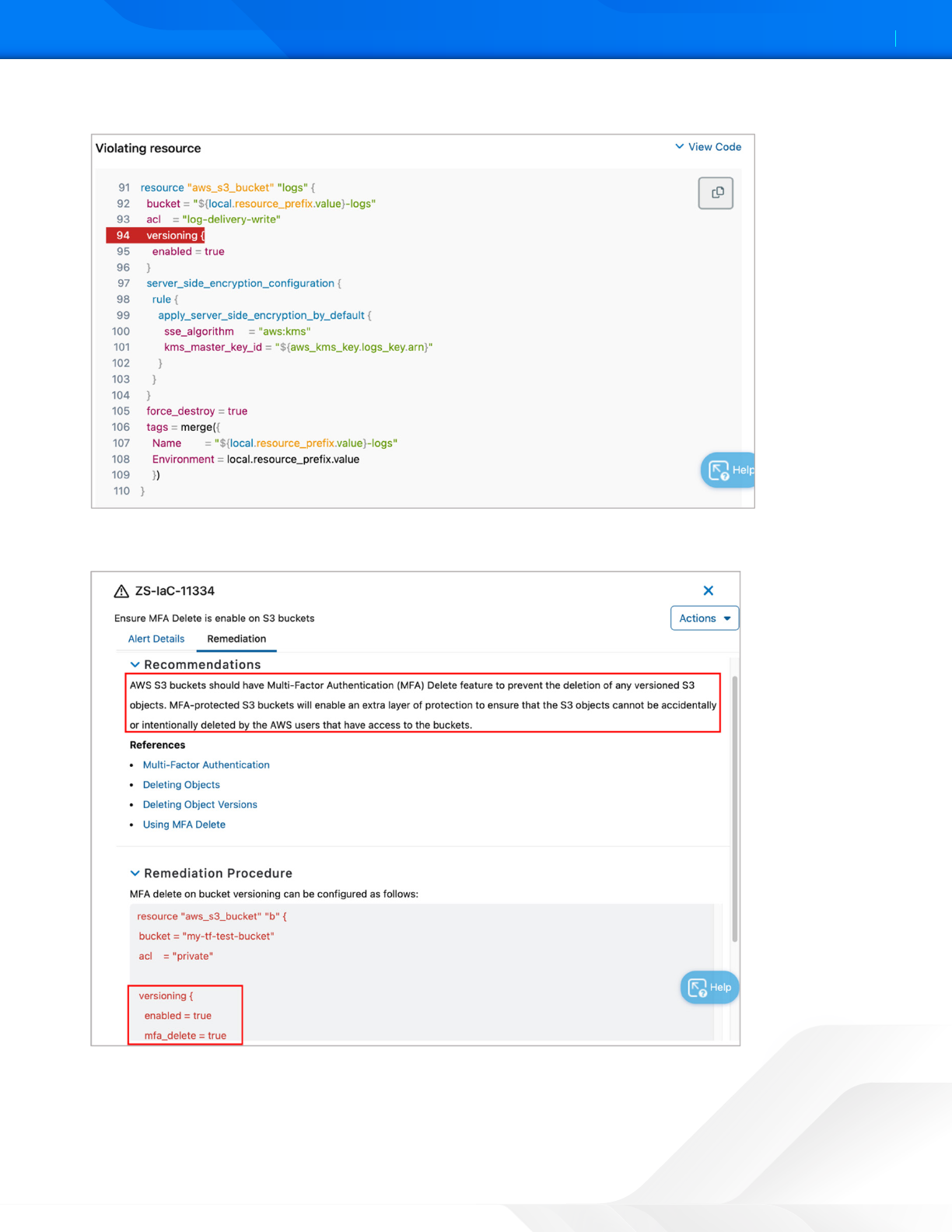
8. See the alert, which provides a code snippet with information about the violating resource.
Figure 18. ZPC Violating Resource
9. Click the Remediation tab to see the recommendations.
Figure 19. ZPC remediation
ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
22©2023 Zscaler, Inc. All rights reserved.
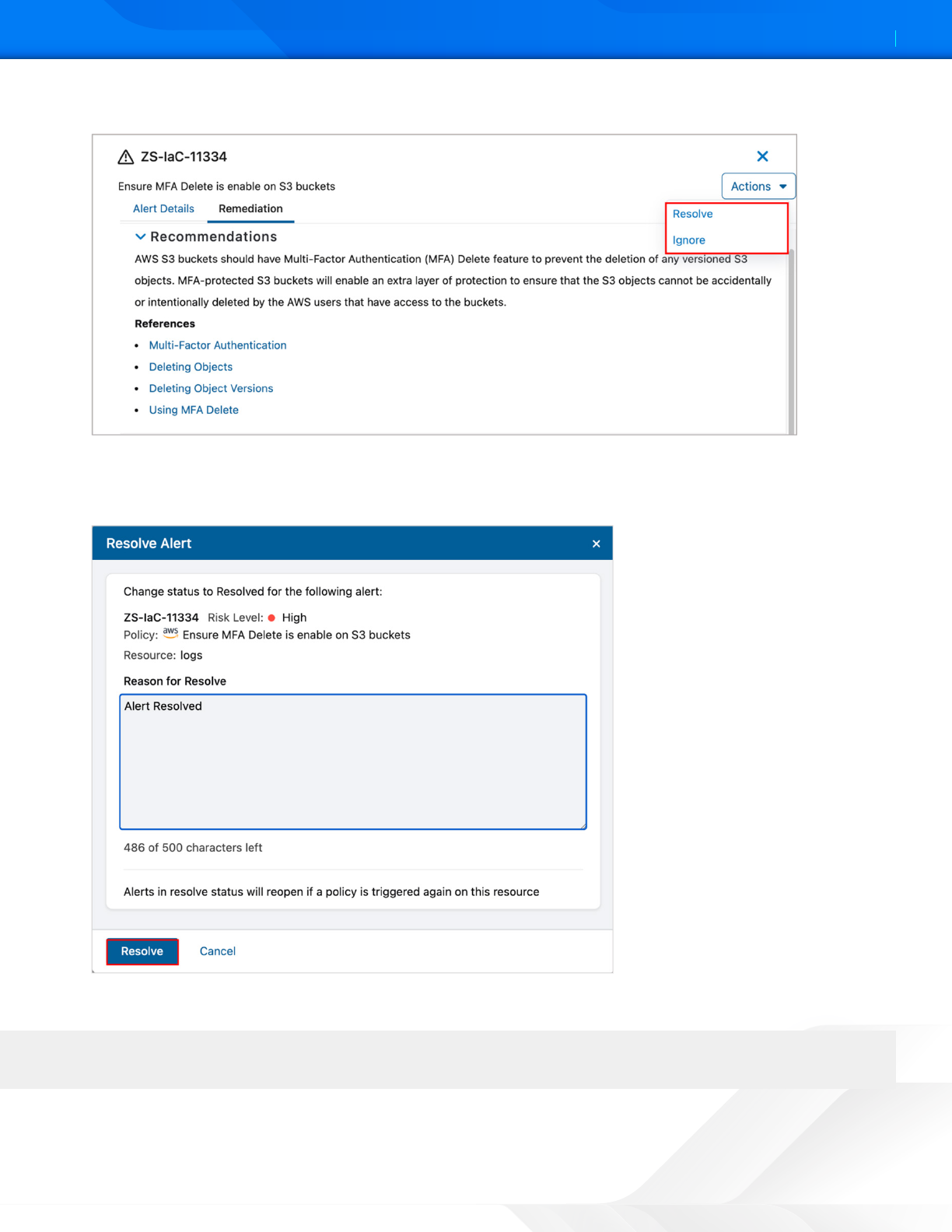
10. To resolve or ignore the alert, select Actions, and then select Resolve or Ignore.
Figure 20. ZPC remediation
11. Enter a reason to resolve the alert.
12. Click Resolve. This example uses Resolve. The Resolve Alert screen is displayed
Figure 21. ZPC resolve alert
Alerts in resolve status reopen if a policy is triered again on this resource.
ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
23©2023 Zscaler, Inc. All rights reserved.
Zscaler Posture Control for Azure Pipelines
The IaC Scan extension scans and identifies security misconfigurations in the IaC Terraform, Kubernetes, Helm, and
CloudFormation templates for pipeline jobs in Microso Azure. The IaC Scan extension automatically triers a scan of
the IaC templates, identifies configuration errors and policy violations, and displays the scan results in the Azure console
output.
Configuring the Zscaler IaC Scan for Microso Azure Pipelines
This section provides step-by-step instructions to configure the Zscaler IaC Scan for Azure Pipelines.
Prerequisites
To add Zscaler IaC Scan to a pipeline, make sure that you enable the Azure Pipeline services in the project that is scanned
during the pipeline execution process.
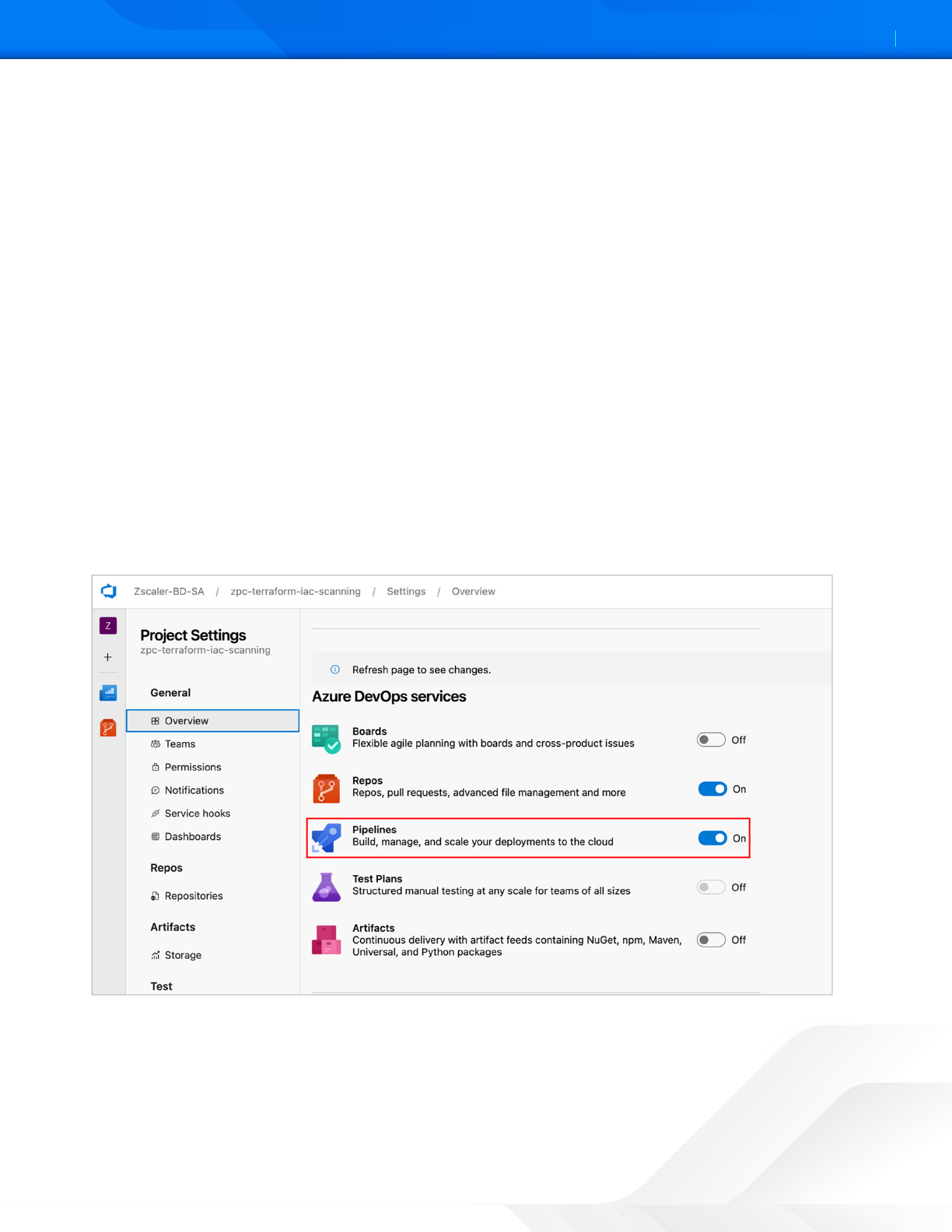
To enable the pipeline service for a specific project:
1. Login as administrator to the Azure DevOps portal.
2. Select the project where the service is enabled.
3. Go to Project Seings > Overview.
4. Under Azure DevOps Services, enable Pipelines.
Figure 22. Azure Pipelines
ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
24©2023 Zscaler, Inc. All rights reserved.
Download the Zscaler IaC Scan Extension
This integration requires that you download and install the Zscaler IaC Scan extension from the Visual Studio Marketplace.
To learn more, refer to the Azure Documentation.
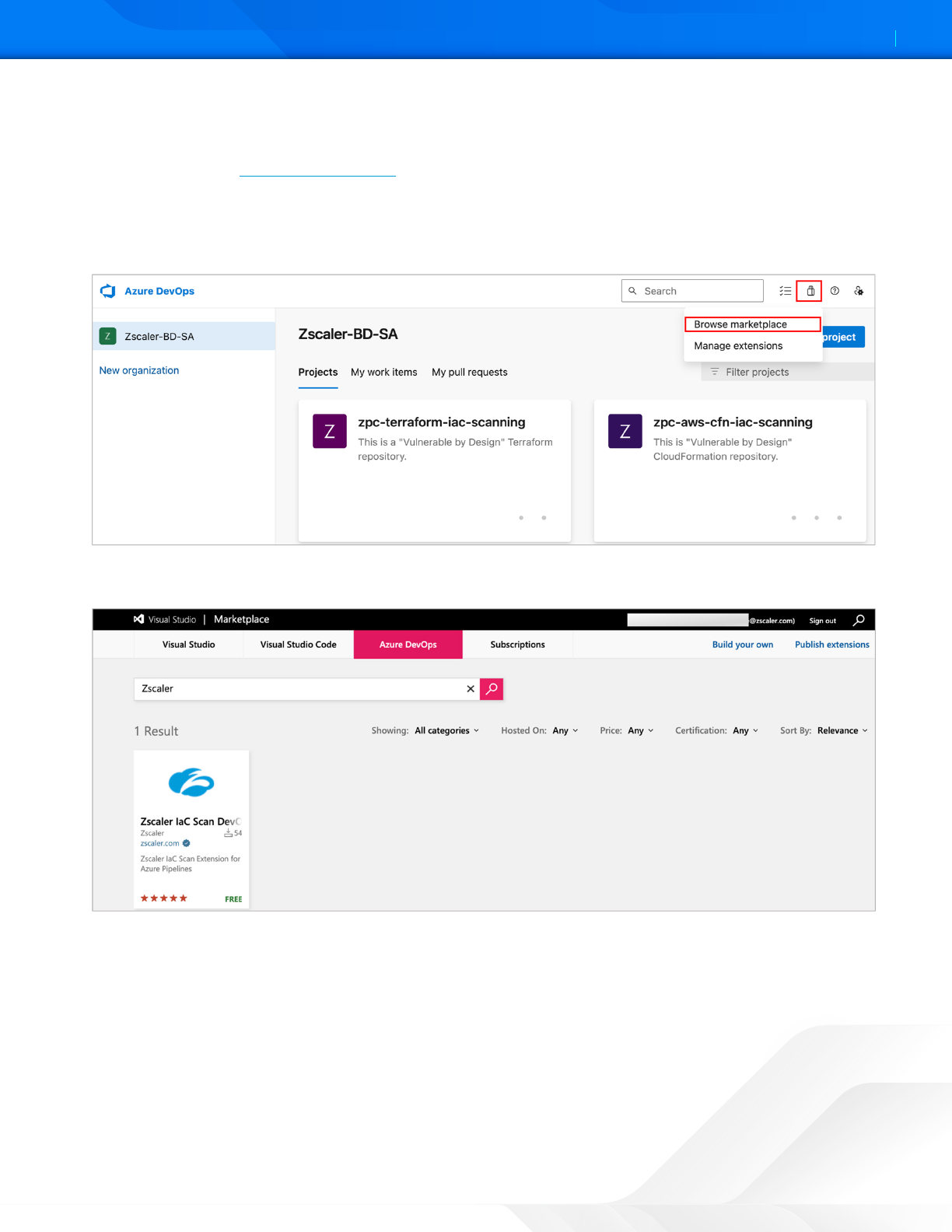
1. Install an extension to your organization by doing the following steps:
a. Login to your Azure DevOps portal.
b. Open the extensions menu and choose Browse marketplace.
Figure 23. Azure DevOps Browse Marketplace
2. Search for Zscaler.
Figure 24. Azure DevOps Browse Marketplace
ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
25©2023 Zscaler, Inc. All rights reserved.
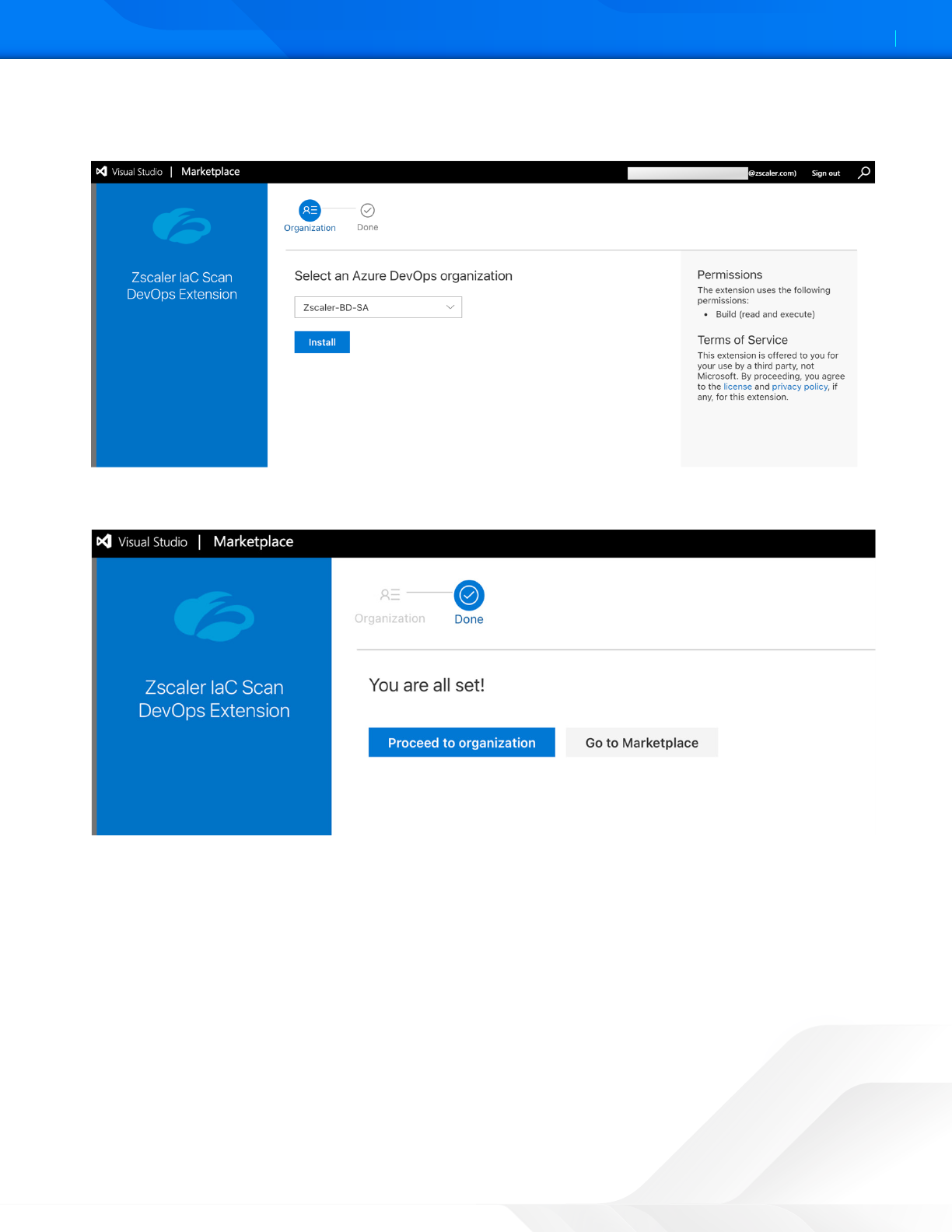
3. Search for Zscaler IaC Scanner DevOps Extension.
4. Click Install.
Figure 25. Install Zscaler IaC Scan DevOps Extension
5. Aer the installation finishes, click Proceed to organization.
Figure 26. Proceed to organization
ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
26©2023 Zscaler, Inc. All rights reserved.
Configuring the Zscaler IaC Scan Extension for Microso Azure Pipelines
To configure the Zscaler IaC Scan plugin for Azure:
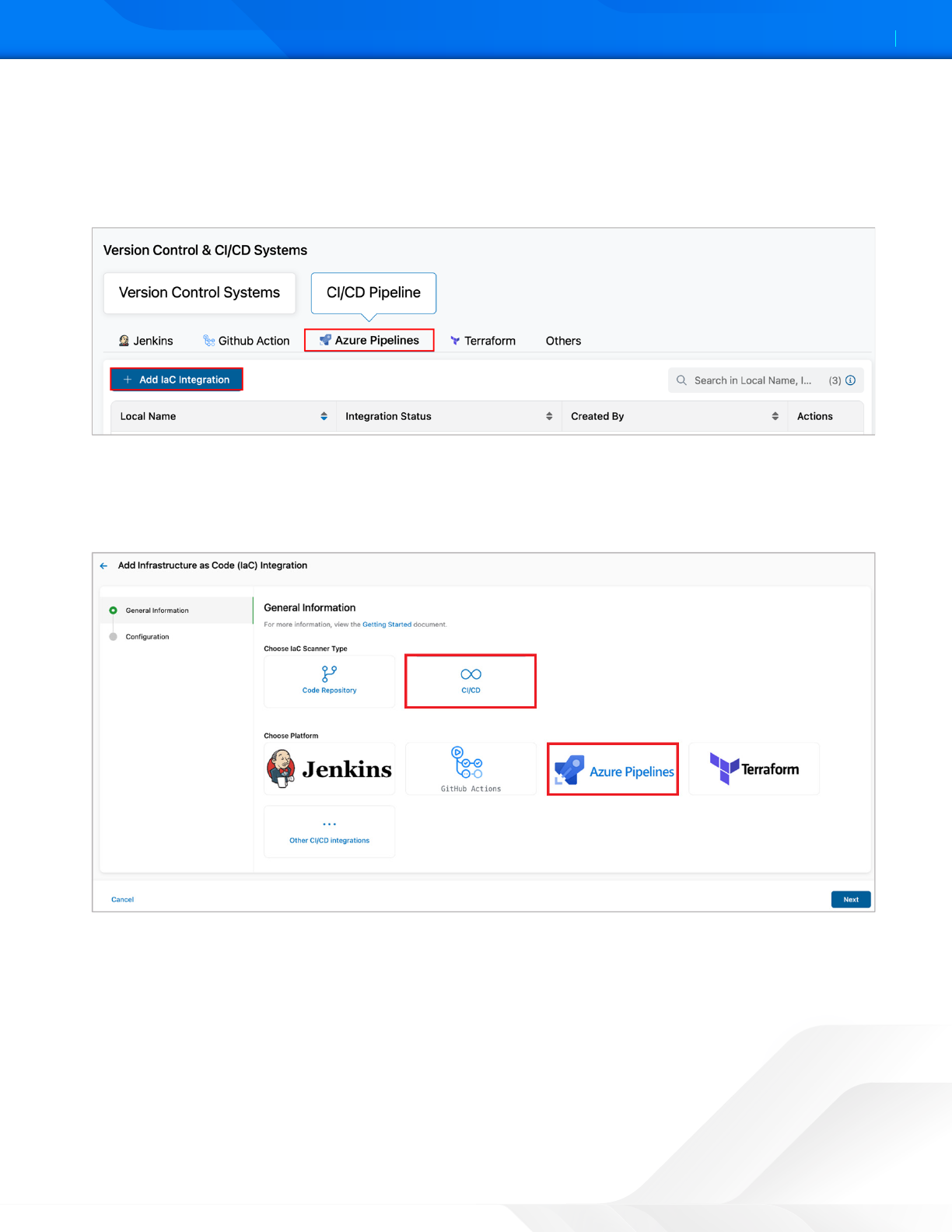
1. Go to Administration > Version Control & CI/CD Systems.
2. On the Azure Pipelines page, click Add IaC Integration.
Figure 27. ZPC CI/CD Pipeline
3. Under General Information:
a. For Choose IaC Scanner Type, select CI/CD.
b. For Choose Platform, select Azure Pipelines.
Figure 28. ZPC Integration Generation Information Page
4. Click Next.
ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
27©2023 Zscaler, Inc. All rights reserved.
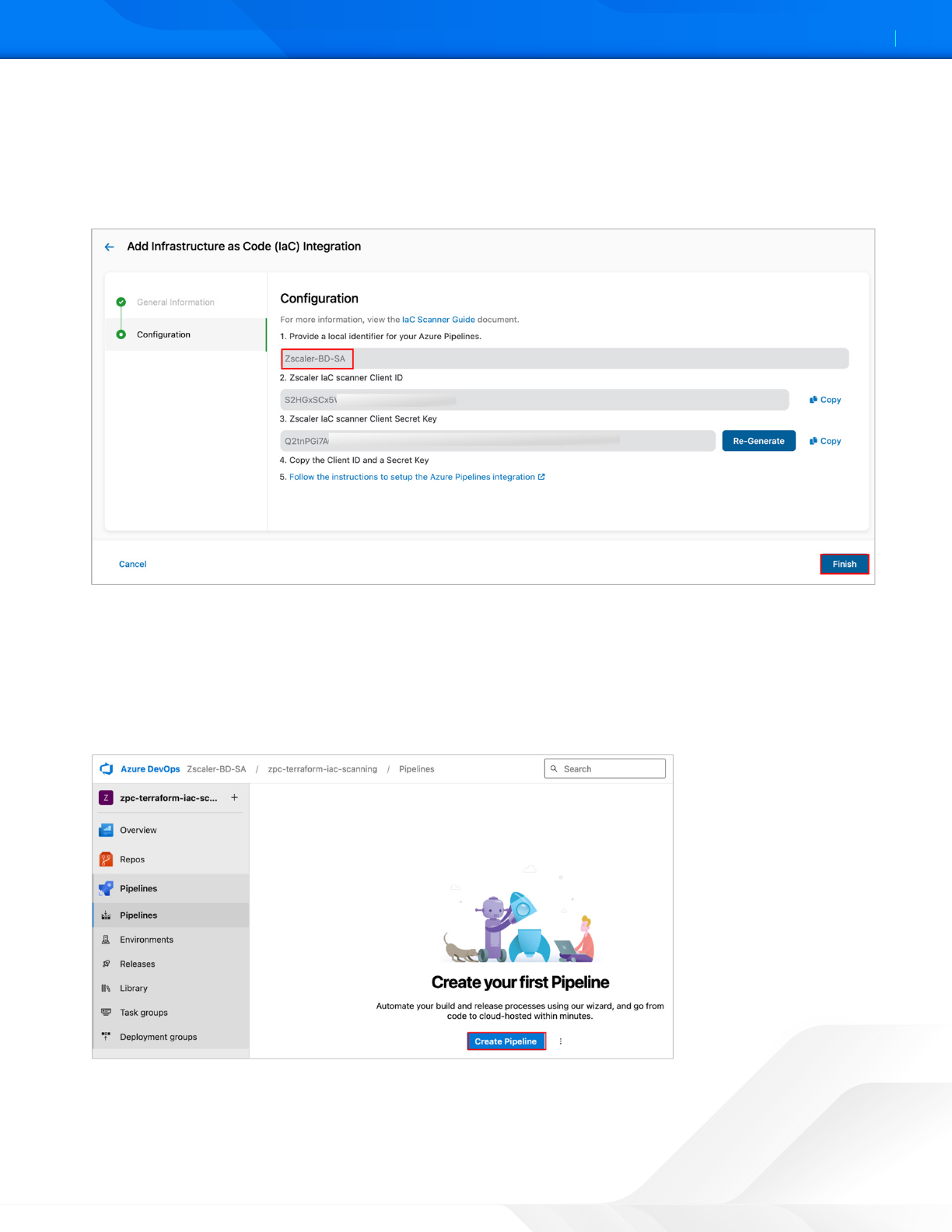
5. Under Configuration, enter the unique name for the Azure Pipeline, then click Confirm. Microso Visual Studio
generates a Client ID and Client Secret aer confirmation. Zscaler requires these values to authorize the Zscaler IaC
Scan extension to access the Azure Pipeline jobs.
6. Copy the Client ID and Client Secret.
7. Click Finish.
Figure 29. ZPC Azure Pipeline Configuration
Configuring Zscaler IaC Scan in Azure Pipeline
The following explains how to add the Zscaler IaC scan to an Azure pipeline:
1. Select the desired project in the Azure DevOps portal.
2. Select Pipelines and click Create Pipeline.
Figure 30. Create Azure Pipeline
ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
28©2023 Zscaler, Inc. All rights reserved.
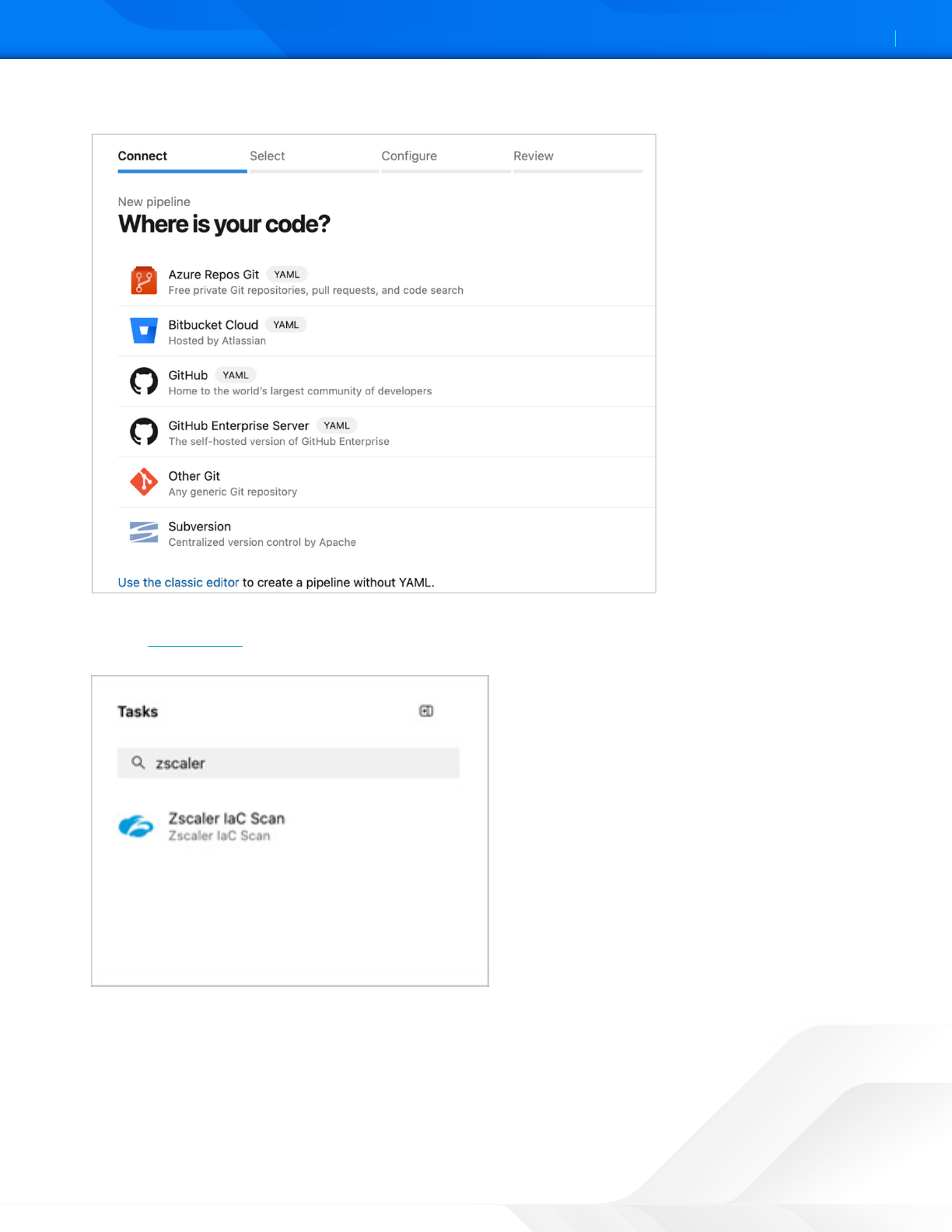
3. Choose the location of the code. This example uses Azure Repos Git.
Figure 31. Choose the code location
4. Use the task assistant to add tasks to the YAML pipeline. Click Show assistant to view the list of tasks in Azure
DevOps. Azure DevOps calls all third-party tools, including the Zscaler IaC Scan extension, Tasks.
Figure 32. Zscaler IaC Scan extension
ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
29©2023 Zscaler, Inc. All rights reserved.
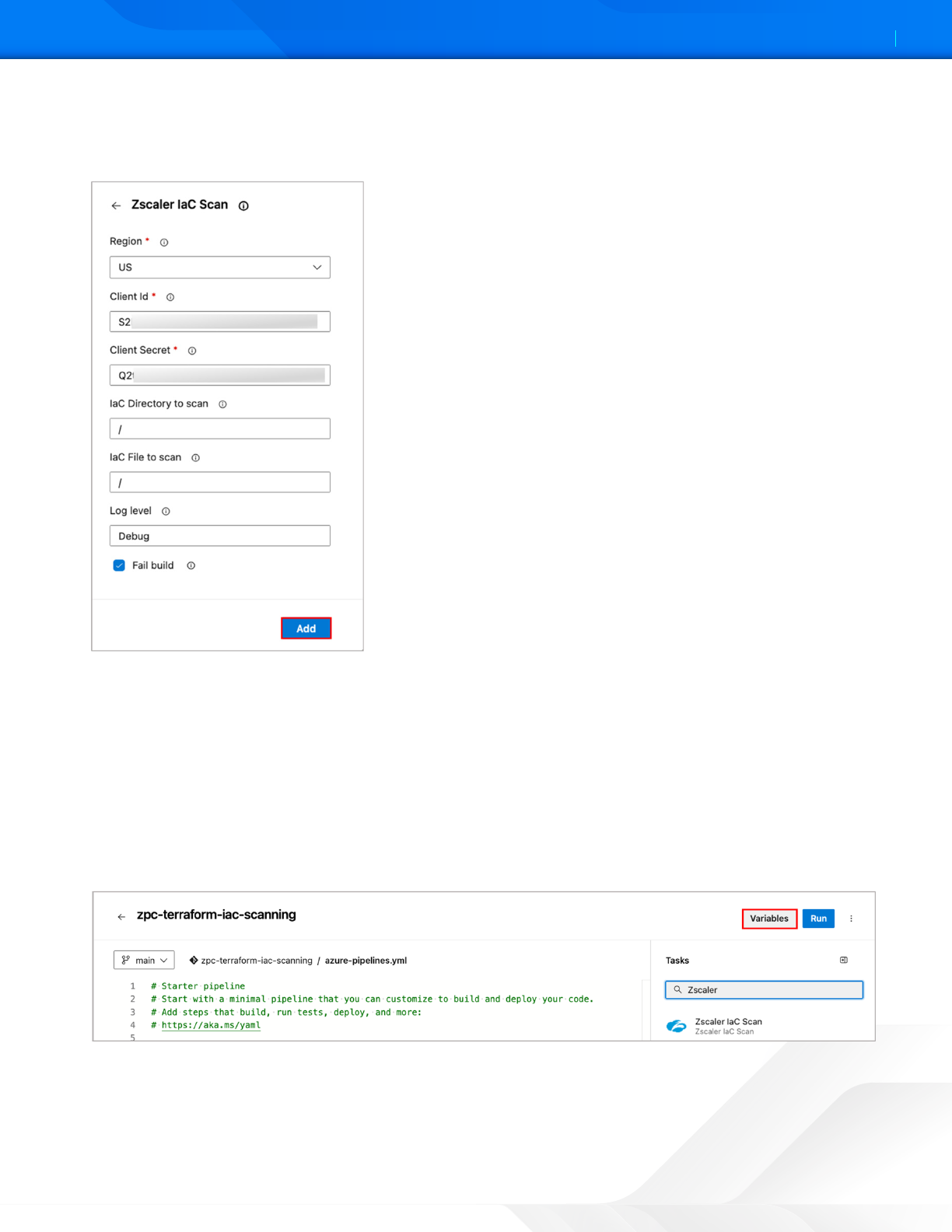
5. Select Zscaler IaC Scan from the list.
6. Fill in the required configuration parameters with your Client Id, Client Secret, Region, and other optional
parameters.
Figure 33. Zscaler IaC Scan extension configuration
7. Click Add. Azure DevOps portal automatically adds the parameters to the azure-pipeline.yml file.
8. Click Seings within the script to edit these parameters.
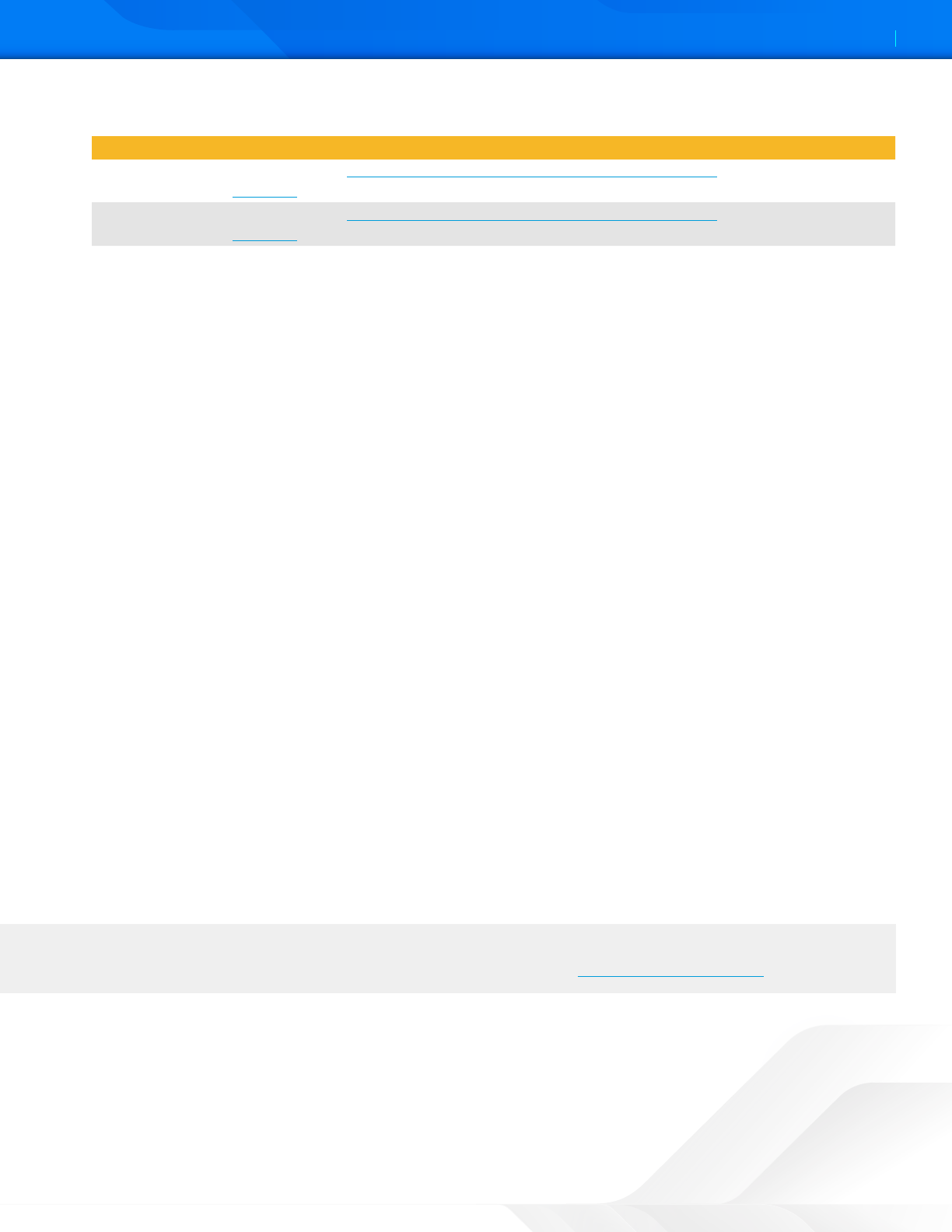
Adding ZPC Credentials as Variables
By default, credentials are hard-coded within the azure-pipeline.yml file aer they are added to the Zscaler IaC Scan
configuration.
To prevent this behavior, add your credentials as environment variables by doing the following:
1. Click Variables.
Figure 34. Added credential variables
ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
30©2023 Zscaler, Inc. All rights reserved.
2. Click the Add (+) icon to add new variables.
Variable Name Value YAML Reference
CLIENT_ID Value created in Configuring the Zscaler IaC Scan for Microso Azure
Pipelines.
$(CLIENT_ID).
CLIENT_SECRET Value created in Configuring the Zscaler IaC Scan for Microso Azure
Pipelines.
$(CLIENT_SECRET
Aer the credential variables are added, they are automatically added to the azure-pipelines.yml file. The following
is an example YAML file configuration.
# Starter pipeline
# Start with a minimal pipeline that you can customize to build and deploy your code.
# Add steps that build, run tests, deploy, and more:
# https://aka.ms/yaml
trigger:
- main
pool:
vmImage: ubuntu-latest
steps:
- task: ZscalerIaCScan@1
inputs:
region: ‘US’
clientId: ‘$(CLIENT_ID)’
clientSecret: ‘$(CLIENT_SECRET)’
iacdir: ‘/’
iacle: ‘/’
failBuild: true
logLevel: ‘Debug’
You can configure the ZPC credentials within an Azure Key Vault, but the process is out of the scope of this
deployment guide. To configure credentials via Azure Key Vault, refer to Azure DevOps Labs portal.
ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
31©2023 Zscaler, Inc. All rights reserved.
Executing Azure Pipeline and Viewing Zscaler IaC Scan results
ZPC generates a graphical report that contains the details of the IaC scan results and policy violations detected in an
Azure Pipeline job. You can see this report on Azure DevOps and download the report as a CSV or PDF file.
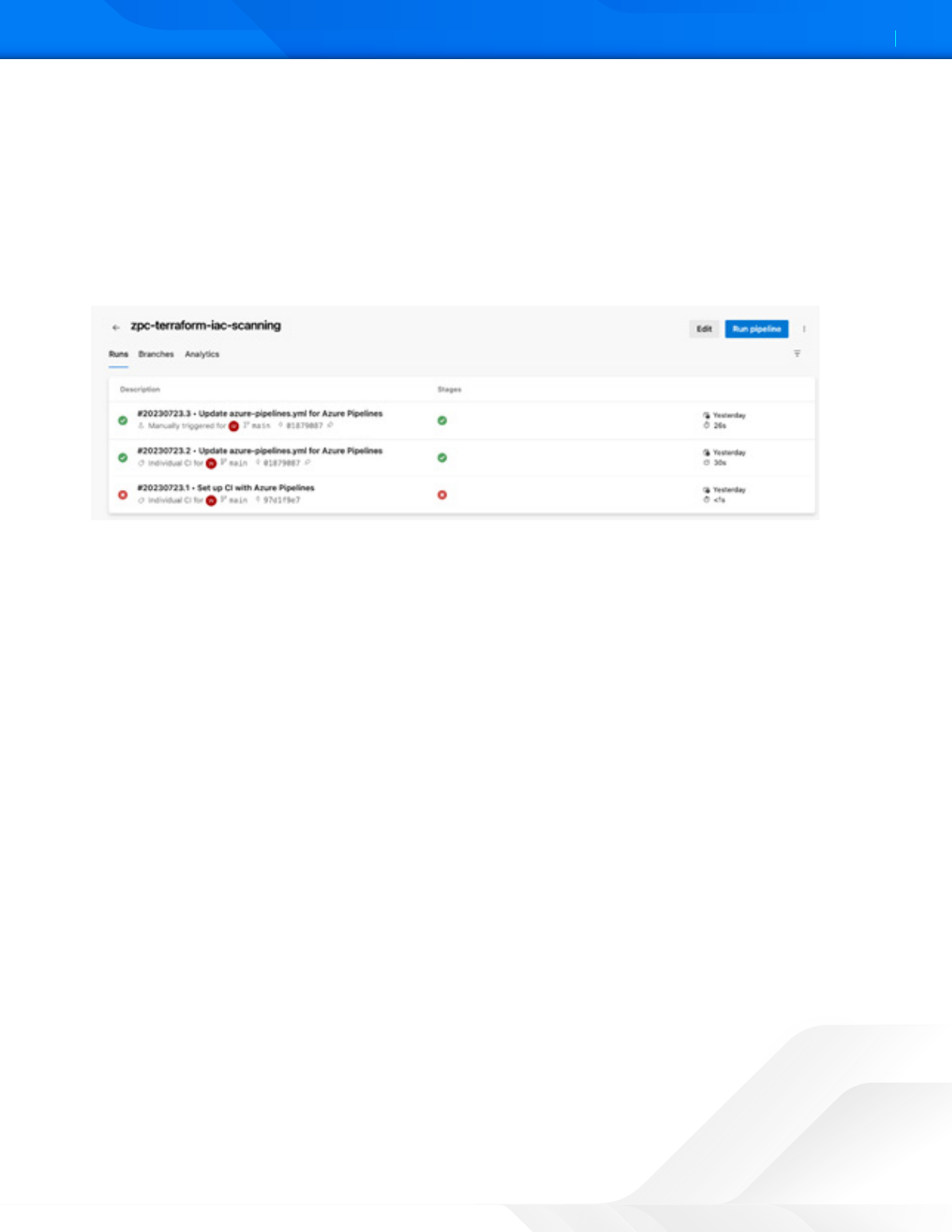
To view the IaC scan results on Azure DevOps:
1. Log in to Azure DevOps.
2. In the le-side navigation, click Pipeline to view the list of recently run Pipeline jobs.
3. Click the required Pipeline job.
Figure 35. Azure pipeline scan results
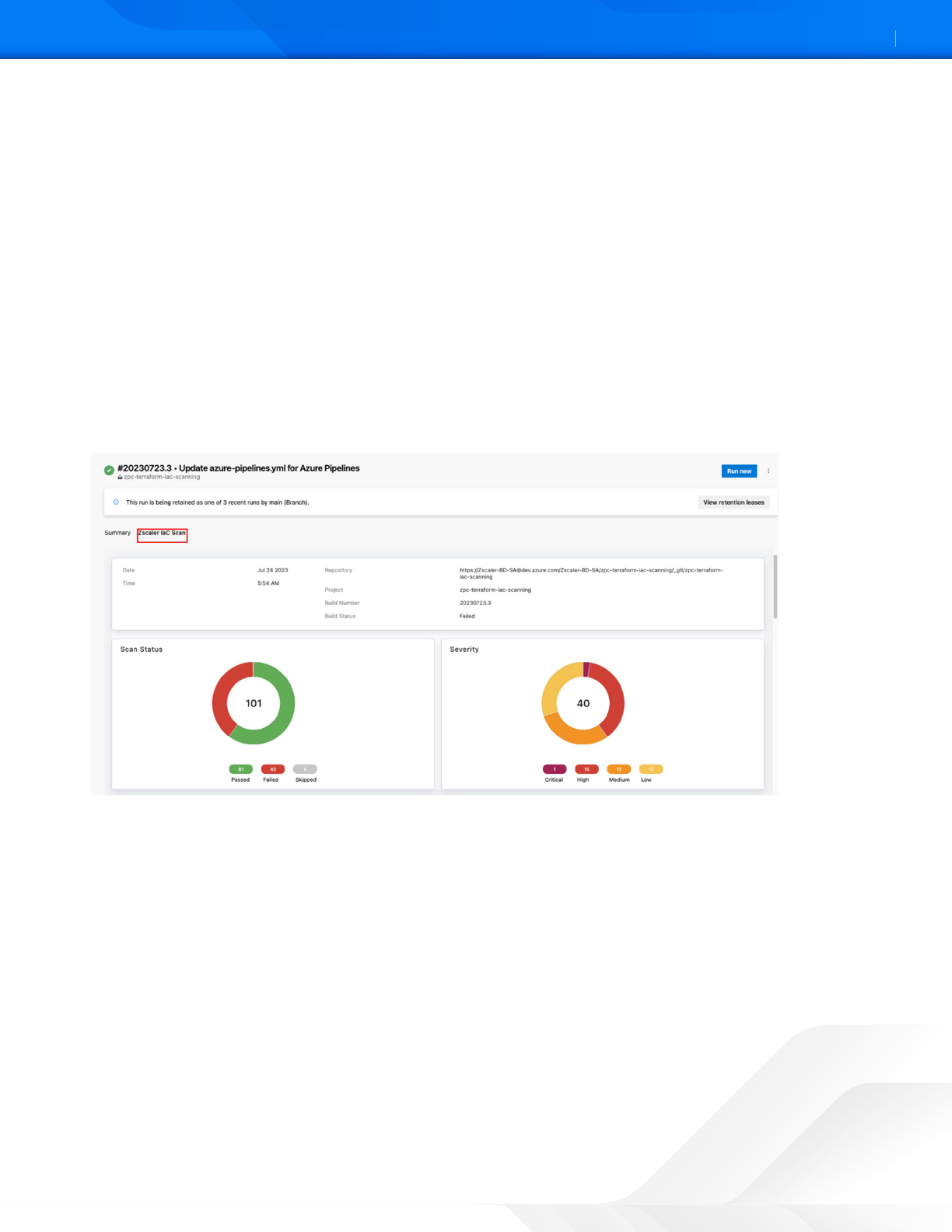
ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
32©2023 Zscaler, Inc. All rights reserved.
4. Click the Zscaler IaC Scan tab to view the report with the following details:
• Scan Status: The total number of scans and status (Passed, Failed, Skipped).
• Severity: The overall severity level of the policy violations (Critical, High, Medium, or Low).
• Failed, Skipped, and Passed tabs: The number of policies that ZCP failed, skipped, and passed during the IaC
scan. For each policy, you can see:
• Policy Name: The policy title. Click the arrow next to the policy to view:
• Resource: The name of the resource (e.g., the name of the AWS S3 bucket).
• Resource Type: The type of resource (e.g., aws_s3_bucket).
• File: The name of the scanned file.
• Line: The line within the code that has misconfigurations.
• Scan Status: The status of the scan (Failed, Skipped, or Passed).
• Policy ID: The unique identification number for the security policy.
• Severity: The severity level of the policy violation (Critical, High, Medium, or Low).
Figure 36. Azure pipeline scan results
ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
33©2023 Zscaler, Inc. All rights reserved.
Viewing Azure Pipeline IaC Scan Summary in the ZPC Portal
To visualize the Azure repos alerts generated by the Zscaler IaC Scan tool:
1. Login to the ZPC Admin Portal.
Figure 37. ZPC Administrator portal
2. Select the Infrastructure as Code widget.
Figure 38. ZPC IaC Widget
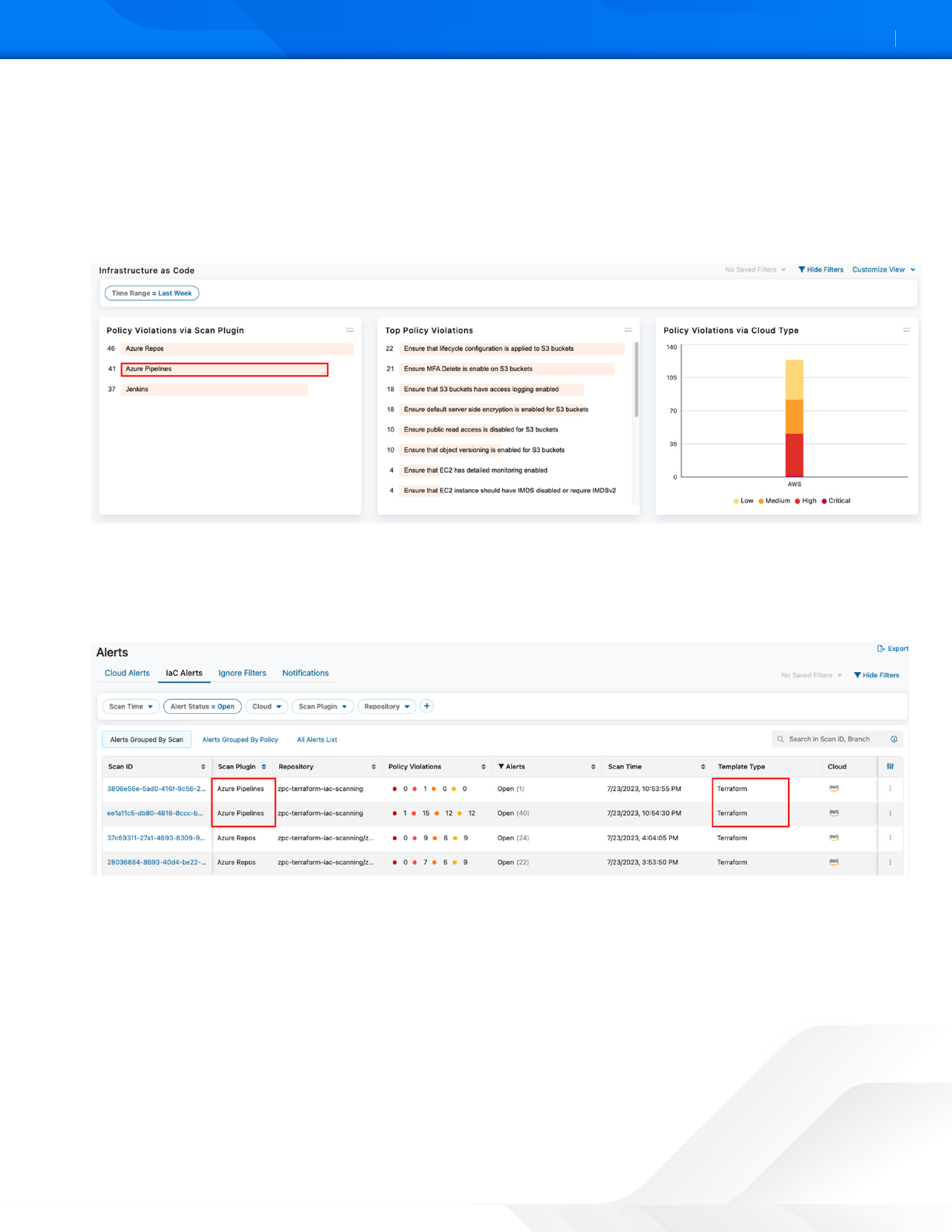
ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
34©2023 Zscaler, Inc. All rights reserved.
3. In the main Infrastructure as Code dashboard, Zscaler provides a summary of the following:
a. Policy violations identified via the Zscaler Scan Plugin.
b. Top Policy Violations.
c. Policy Violations by Cloud Type.
4. Select one of the Top Policy Violations. This example uses Ensure that lifecycle configuration is applied to S3
buckets.
Figure 39. ZPC Infrastructure as Code Dashboard summary
5. Group the IaC alerts by Scan type. In the following example, the filter only displays Scan Plugin = Azure Pipelines.
a. Other filters are also available (e.g., Scan Time, Alerts, Cloud, and Repository).
b. Add other filters by selecting the Add (+) icon in the filter area.
Figure 40. ZPC Alerts Grouped by Scan
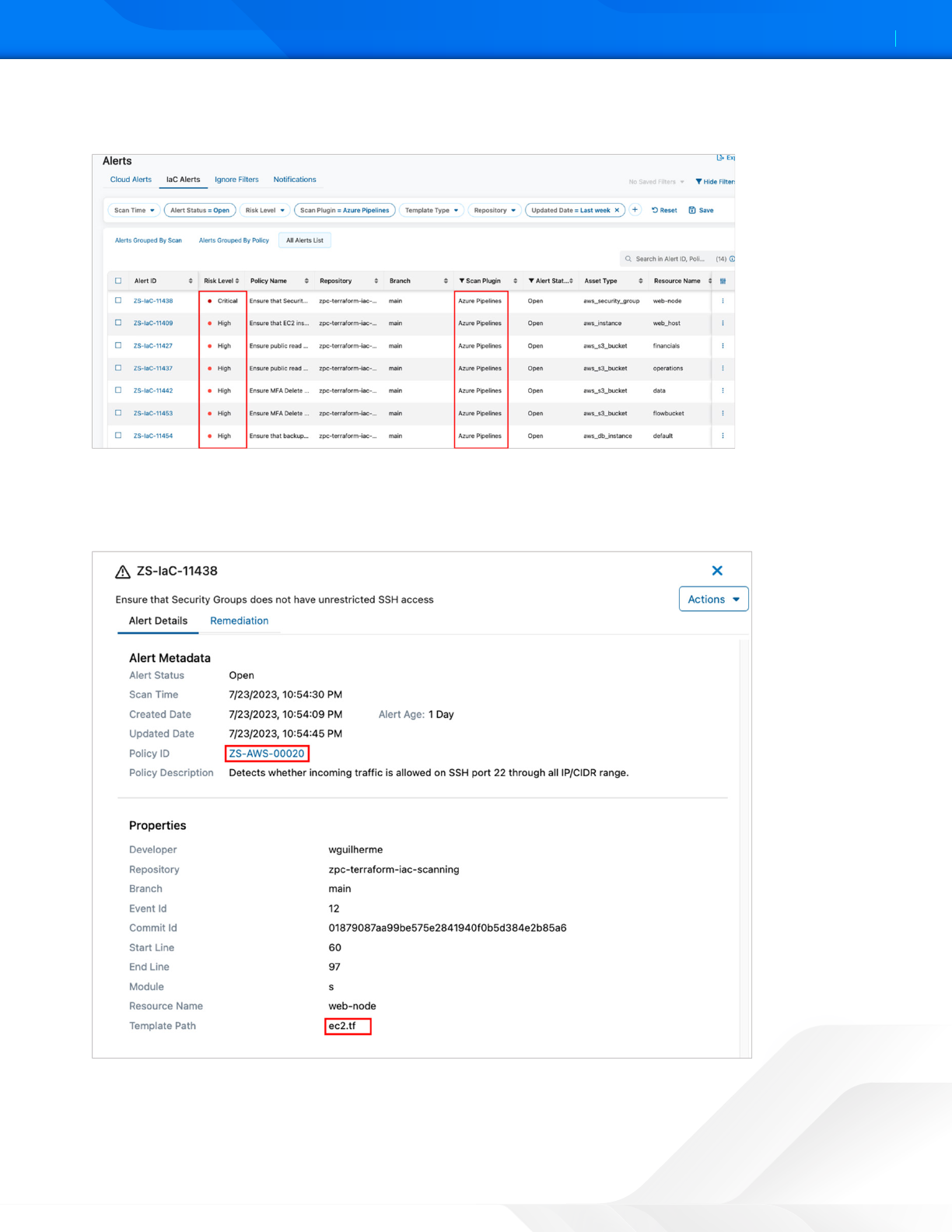
ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
35©2023 Zscaler, Inc. All rights reserved.
6. (Optional) Select the top violations and ZPC automatically creates an IaC alerts filter containing all violations
originated by the Azure Pipeline Scan Plugin.
Figure 41. ZPC Alerts Grouped by Scan
7. Select one of the alerts listed in the Alert ID column. This example uses the alert ID ZS-IaC-11438, which indicates
that ZPC has detected violations associated with a Policy ID: ZS-AWS-00020. This policy detects whether incoming
traffic is allowed on SSH port 22 through all IP/CIDR range.
Figure 42. ZPC Alerts Details
ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
36©2023 Zscaler, Inc. All rights reserved.
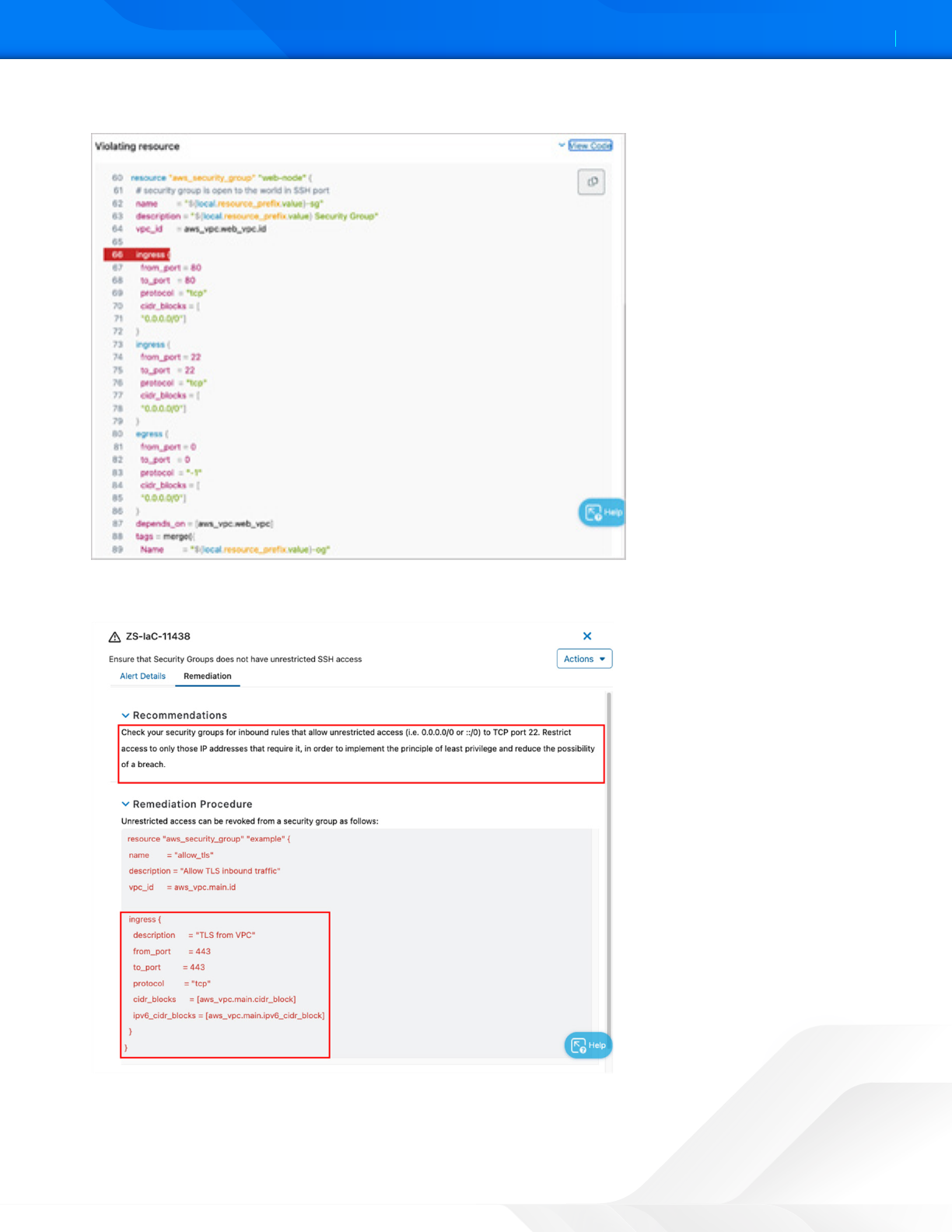
8. See the alert, which also provides a code snippet with information about the violating resource.
Figure 43. ZPC Violating Resource
9. Click the Remediation tab to see the recommendations.
Figure 44. ZPC remediation
ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
37©2023 Zscaler, Inc. All rights reserved.
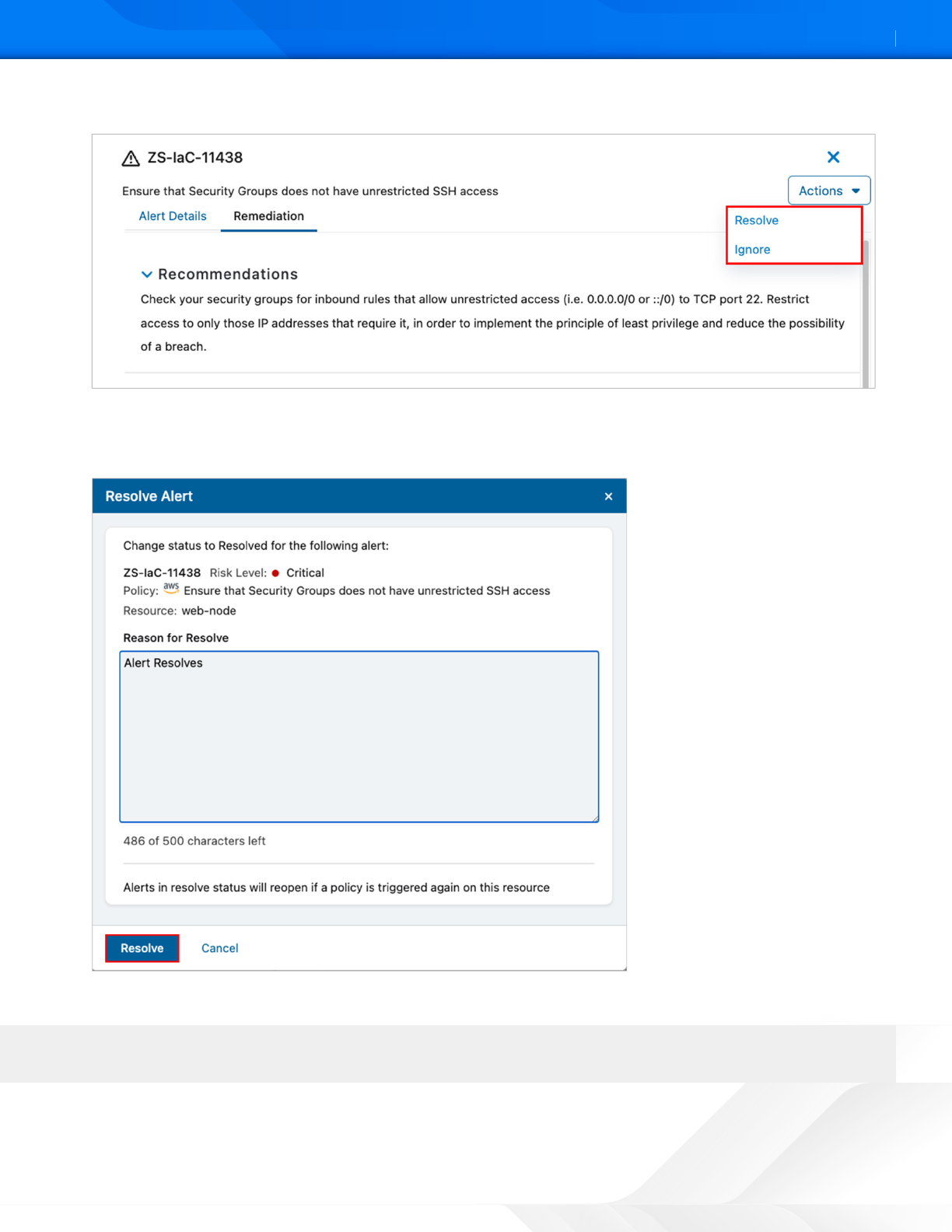
10. To resolve or ignore the alert, select Actions, and then select Resolve or Ignore.
Figure 45. ZPC remediation
11. Provide a reason to resolve the alert.
12. Click Resolve. This example uses Resolve. The Resolve Alert screen is displayed
Figure 46. ZPC resolve alert
ZPC Support
Alerts in resolve status reopen if a policy is triered again on this resource.
ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
38©2023 Zscaler, Inc. All rights reserved.
If you need Zscaler Support for provisioning certain services or to help troubleshoot configuration and service issues, it is
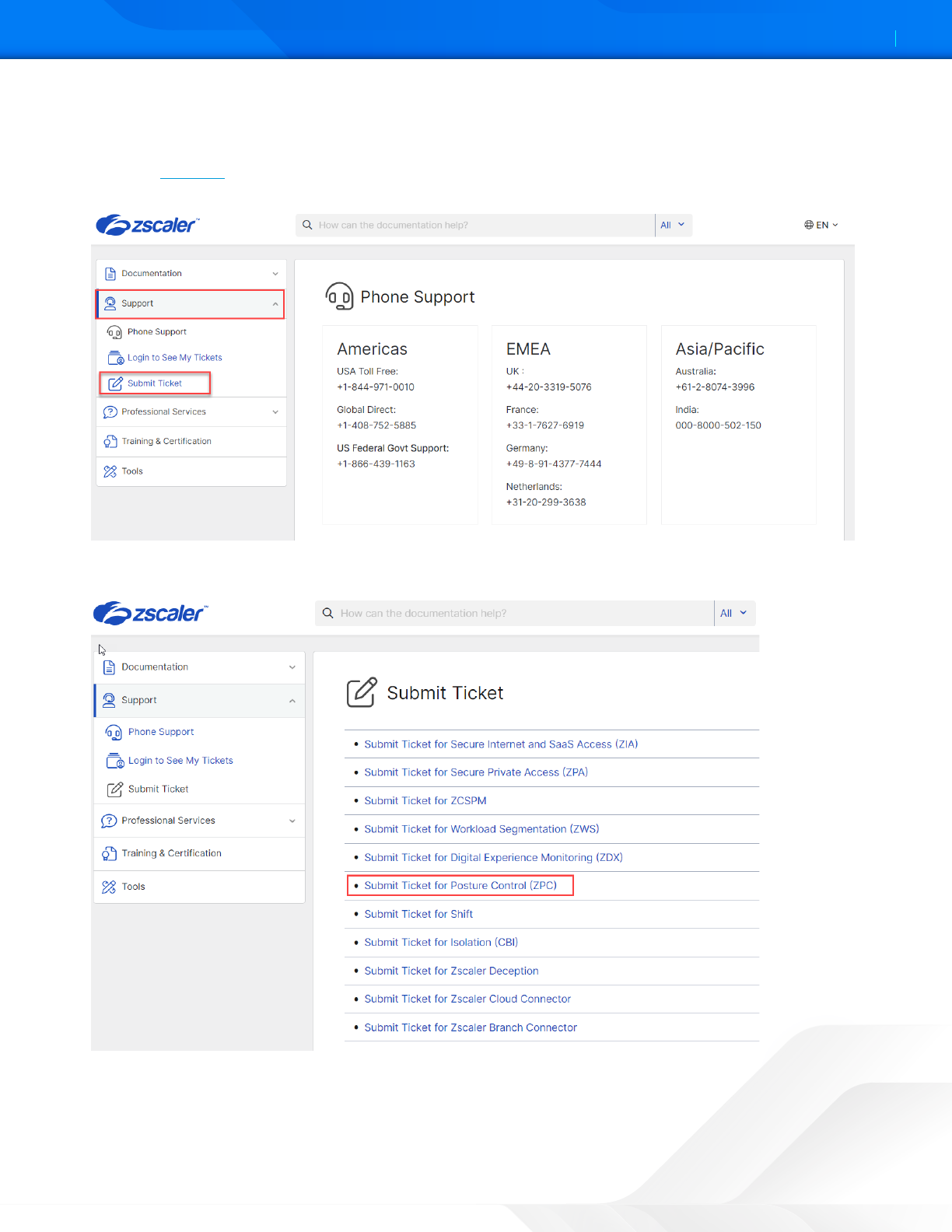
available 24/7/365. To contact Zscaler Support:
1. Go to the ZPC help and select Support from the le-side navigation.
2. Select Submit Ticket.
Figure 47. ZPC Help
3. In the Submit Ticket window, select Submit Ticket for Posture Control (ZPC).
Figure 48. ZPC Support
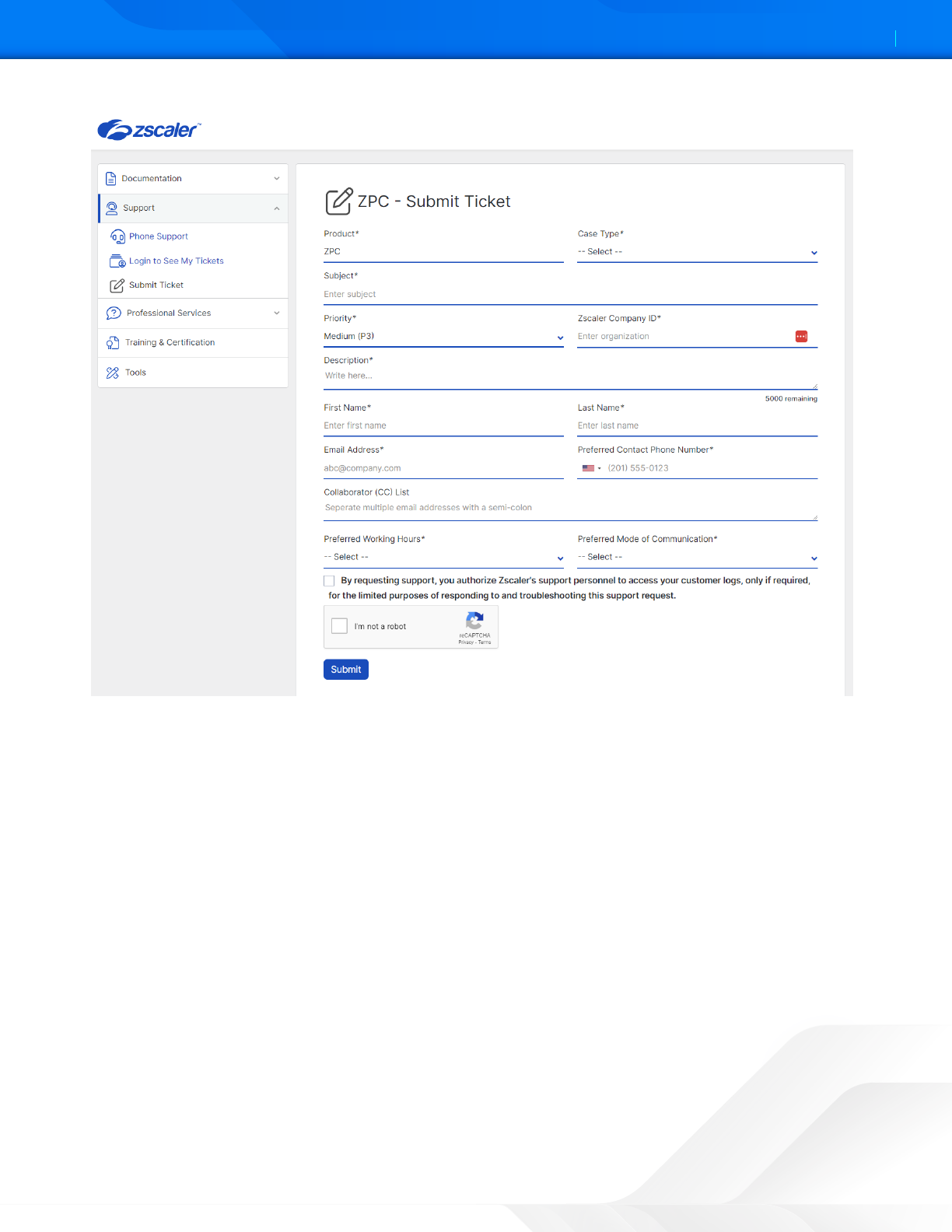
4. In the ZPC - Submit Ticket window, fill in the required fields.
ZSCALER AND AZURE DEVOPS DEPLOYMENT GUIDE
39©2023 Zscaler, Inc. All rights reserved.
Figure 49. Submit ZPC ticket
5. Select the reCAPCHA checkbox, and click Submit. A Zscaler Support representative contacts you via the submied
contact information within 24 hours.
